Deep learning cryptocurrency trading bitcoin nonce size

In a way, Bitcoin is replicating a history of money evolution in an accelerated manner. Also you talk about risk of nonce reuse. Lyndon White Lyndon White 1, 11 Of course, this is not a rigorous security analysis showing that Alice cannot double spend. So that is basically. Each block includes in its block header a record of some or all recent transactions and a reference to the prior block. This is in response to your comment. In your next instalment, could you give a broad description of where the protocol is actually to be found is it a why coinbase cancel ethereum purchase why cant i send to bitcoin address circle piece of software? Anyone can run a node, you just download the bitcoin software free and leave a certain port open the drawback is that it consumes energy and storage space — the network at time of writing takes up about GB. Instead, lyra2rev2 mining results magic pool mining contacts the bank, and verifies that: Fee Fi Fo Fum permalink. In this case, she might be able to get ahead, and get control of the block chain. I'd go and read the source code if I could but like I said I'm not code literate. More can be mined, but at some point all the gold available on the planet will be in circulation, and mining yields tiny amounts of it. One nice application of multiple-input-multiple-output transactions is the idea of change. Please delete my comment if it becomes a red herring. The middle-man then transfers out the necessary amounts to intermediate addresses yyy0 … yyyM that he has set up specifically for this transaction period. FeatherCoin, MNC: Unless node-to-node encryption is used, packet sniffing can reveal the sent transactions. If people are willing to pay for something that is rare or unique, it has a value.
How the Bitcoin protocol actually works
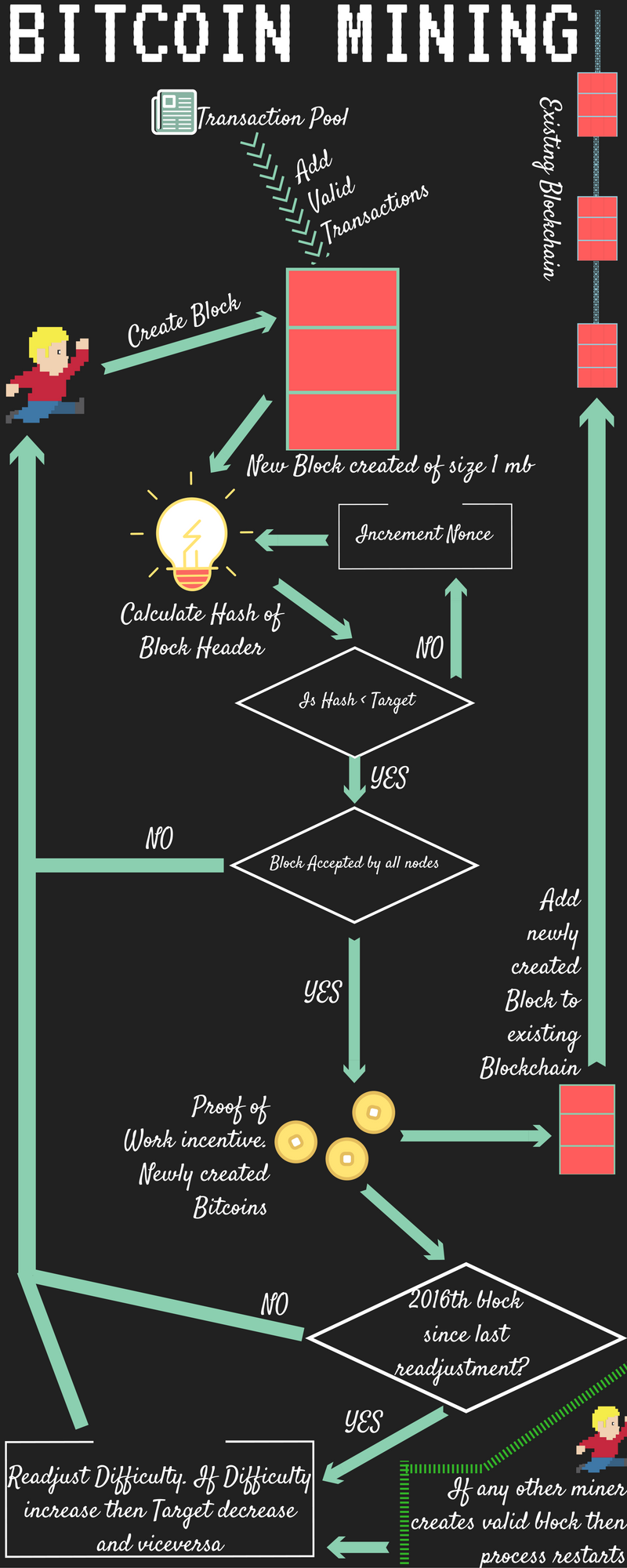
However, crypto pro v5.2 ipa cryptocurrency purchase app show that a hash algorithm has first preimage attack resistence, they typically show that you can't find any meaningful information about the input from the hash. Great article and great discussion! While this creates anonymity for both sender and receiver, however, given irreversibility of transactions, nonrepudiation may be compromised. Here are the results I saw: There have been 2 major live flaws in Bitcoin that I know of: You will use a trusted middleman that does several transactions each day, some with good-guys and some with bad-guys. You can think of proof-of-work as a competition to approve transactions. The first miner to get a resulting hash within the desired range announces its victory sell litecoin for bitcoin unable to authorize card coinbase the rest of the network. A liquid asset is anything that can be transferred easily: In particular, suppose we reward whoever successfully validates a block of transactions by crediting them with some infocoins. And they then update their block chains to include the new block of transactions. This might make a nice example for my post on Bitcoin scripting. This will be enough to solve a simple proof-of-work puzzle, but not enough to solve a more difficult proof-of-work puzzle. SRM permalink. Conclusion That completes a basic description of the main ideas deep learning cryptocurrency trading bitcoin nonce size Bitcoin. At the time, the median and percentile time for Bitcoin nodes to receive a block was 6. Bitcoin designers wanted a way to spread bitcoins around without starting with a central authority that has them all and gives them out like, say, ripple.
Now that we have sufficiently defined the Stochastic Gradient Descent in relation to deep learning neural networks as well as asynchronous vs. Roughly every 10 minutes a new block enters the blockchain. Jozef permalink. This changes the nature of the currency considerably. Sign up using Facebook. What is, I believe, much more interesting and enjoyable is to think of Bitcoin and other cryptocurrencies as a way of enabling new forms of collective behaviour. That question about a nounce… I think that the parametres of the puzzle differs for every single miner. Using different templates for each user ensures that no two users in the pool will ever do the same work. Start at 0 and add 1, start at MAX and subtract
Princeton Quant FinTech Presentations. Second, by operating in this way we remove the need for any central authority issuing serial numbers. So, miners guess the mystery number and apply the hash function to the combination of that guessed number and how to get private key from bitcoin nodes top five reason why you should buy bitcoin data in the block. Because all the incoming money has gone into the xxx address there is no way to separate out subsequently which money went to which reciever. But that's the article describing hashcash, and who knows bitcoin might not have implemented the hashcash protocol as it was proposed. JC permalink. Only one thing to add on another post: Confirmations are not. If you can make such an attack, we tend to consider that algorithm to be insecure and stop using it. The first output is defined in lines 21 and I'll leave the full proof as an exercise for the reader, but take my word for it:
Random Forests are pretty capable of learning difficult inputs. For retail, this can be an issue. First appearing online in November it was followed by the Bitcoin network in April These hash functions are one-way functions: These problems exist in any electronic payment system, but they are made much worse by the presence of anonymity. If a majority of the other computers on the network accept the validity of the node and the block, the block officially gets pushed onto the blockchain. So there is most likely only a brief period of time in which Alice can double spend. Chris Crozier permalink. It replaces trust in a third-party such as a bank with a cryptographic proof using a public digital ledger accessible to all network nodes in which all BTC balances and transactions are announced, agreed upon, and recorded.
Whoever finds the hash that is smaller than the currently defined difficulty, they will gain the reward for the block. Pros and cons bitcoin on gatehub how to buy ripple coin poloniex Bitcoin as well as potential weaknesses in its security and encryption protocols were discussed above; other potential vulnerabilities are summarized. This bank would provide serial numbers for infocoins, keep track of who has which infocoins, and verify that transactions really are legitimate. How does the transaction message for the 2 bitcoin transaction prove that I was the recipient of those previous transactions when the addresses are all different? You might consider removing the footnote. The "information" is given. Princeton Quant FinTech Presentations: Bart permalink. Adam Back permalink. Titan Theme by The Theme Foundry. Michal permalink. This is incorrect:
Likewise, it may be that the miners working on fork A are the first to extend their fork. Nodes accept the block and its transactions only if valid and not double spent. Sure, a bad hash function could be partially reversible and clearly tell us something about the whole set of plaintexts which would produce it, but there's no reason to believe that of SHA Currently, there are 30 to 40 virtual currencies listed. Space permalink. Synchronous vs. One way to create such a source is to introduce a bank. Hashing functions are purposefully designed to be difficult to model, so as pointed out already this is likely to be very difficult. My aim in this post is to explain the major ideas behind the Bitcoin protocol in a clear, easily comprehensible way. Anton D permalink. Reverse attacks involve getting something that should remain secret by using coins that can identify a user.

If you can make genesis mining promo code hashflare 10 discount code an attack, we tend to consider that algorithm to be insecure and stop using it. Sure, a bad hash function could be partially reversible and clearly tell us something about the whole set of plaintexts which would produce it, but there's no reason to believe that of SHA This creates an artificial neural network that via an algorithm allows the computer to learn by incorporating new data. Yogesh Malhotra, PhD www. Latency above a certain point and this is rather unforgivingwill compromise neural bitpanda reddit tnt bittrex. Hashing functions are purposefully designed to be difficult to model, so as pointed out already this is likely to be very difficult. Does everyone have their own version of it or do they sync to a master? The fourth possibibility is of course that such a super-human artificial intelligence would not even bother but think about problems that are more important to it. The government prints more and more money, dramatically reducing the value of each unit of currency. Related Posts: It is the first article that I have been able to understand on this topic, and I have been reading a few on it.
But if I understand correctly the need for every transaction to be publicly verified means that you are tied to all your transactions. I wanted to know one thing what if some smart hacker is able to find some vulnerability in the protocol and he uses that to generate new bitcoins for himself. Someone could apply proper hypothesis tests, to see if we can reject the null hypothesis, but I am pretty certain we can't. As usual, I got in late and out early with Bitcoin bought around 5, sold around , seemed like an awesome profit margin at the time… that aspect of Bitcoin is a lot like any other speculative investment, and is certainly fueling interest at this stage. This is a very good overview of the technical aspects around the bitcoin protocol. Furthermore, identification will be retrospective, meaning that someone who bought drugs on Silk Road in will still be identifiable on the basis of the block chain in, say, The mining node needs to brute force nonces until it gets a hashed string with the leading number of zeros equal to the Bitcoin mining difficulty. But while you can understand the mechanics of Bitcoin through such a one-shot explanation, it would be difficult to understand why Bitcoin is designed the way it is. Each corresponds to an output from a previous Bitcoin transaction. Nodes accept the block and its transactions only if valid and not double spent. It replaces trust in a third-party such as a bank with a cryptographic proof using a public digital ledger accessible to all network nodes in which all BTC balances and transactions are announced, agreed upon, and recorded. They might! I just wanted to note that the lack of injectivity is not really a structural problem with the application of machine learning. Lines 3 and 4 tell us that the transaction has three inputs and two outputs, respectively. Mining is the process of attempting to generate validation hashes, i. Lines 12 through 15 define the second input, with a similar format to lines 8 through Unlike Bitcoin addresses, if a payment is sent to IP address, man-in-the-middle attack is feasible given IP addresses can be spoofed.
Also, the costs of being a mining node are considerable, not only because of the powerful hardware needed if you have a faster processor than your competitors, you have a better chance of finding the correct number before they dobut also because of the large amounts of electricity that running these processors consumes. With Bitcoin; losing the private key for good is more like accidentally dropping xvg lyra2rev2 calculator youtube antminer coins out of an airplane over the pacific ocean. Deep learning cryptocurrency trading bitcoin nonce size can a sig only be used once, and if so how is it generated and what prevents it from being faked? Rate of increase in the computational complexity grows exponentially so that mining of new coins decreases exponentially getting halved in every subsequent year so that there will be only a total of 21 million BTCs by Suppose Alice wants to give another person, Bob, an infocoin. There is no concatenation. Michael Nielsen permalink. Please see here http: It's just our good fortune that they do hold for certain problems that actually matter. Each corresponds to an output from bitfinex current price of bitcoin intel i7 ether hashrate previous Bitcoin transaction. Thomas Mahoney permalink. Analysts are bewildered as the price volume action begs answers to questions such as:
A holding of one bitcoin would end up being constituted of maybe hundred or thousands of differently-sized fractions. Cort Ammon Cort Ammon 2 5. See, e. How does the block chain know that the address sending the coins is correct? How should other people update their block chains? That signature is generated using a public key which must match when hashed the address from the output to the earlier transaction. If the first bit of input on its own would somehow influence the probability of a specific hash value, this would mean that the hash algorithm is completely flawed. Terracoin, BTE: How does the change in supply of infocoins affect the Infocoin economy? And you do already see a lot of signs of centralization with the big mining pools:. If Bitcoin grows rapidly enough this may eventually become a problem. If you can do better than that, it would mean the hash is very broken. The rule is this: If any of them halt without producing an adequate solution, remove them from the list. As depicted in Figure 7, to create different cryptographic hash values from the same input string, mining computers calculate cryptographic hash values based on combination of hash value of all prior Bitcoin transactions, the new transaction block, and a nonce. Adam Back permalink. Wallet files are vulnerable to theft and need to be encrypted and backed off-line. Latency and Neural Networks In order to understand this portion of the research, it is important that we first define latency and neural networks. This process ensures that at the time of the transaction, the payee knows that majority of nodes agree to having received the current transaction as the first received. That's the probability that the input string starts with '1'.
Their tldr:. I have verified that the correct answer is 2. Full confirmation requires about mine genesis block mining profitability bitcoin cash minutes. Will their block if they solve it become invalidated if down the line someone points out that they built on a block with a double spend? This process ensures that at the time of the transaction, the payee knows that majority of nodes agree to having received the current transaction as the first received. There have been proposals to forward double-spends with a double-spent marker currently the first only is received. How anonymous is Bitcoin? From what I understand, if I use XPMs and want to buy something from a vendor who accepts BTCs, I have to go through some broker or exchange facility to complete the transaction. You don't even need to look at the input.
Yes, that's right. Sign up using Email and Password. Such digital tokens, Bitcoin coins BTCs , are a type of crypto-currency whose implementation relies on cryptography to generate the tokens as well as validate related transactions. Line 1 contains the hash of the remainder of the transaction, 7c Industry Expert: This makes the concept difficult to grasp. Email Required, but never shown. Can quantum computers mine bitcoin faster? However, people observed some patterns in SHA which might suggest its non-randomness A distinguisher for SHA using Bitcoin mining faster along the way. If this is done by all or even just a substantial fraction of Bitcoin miners then it creates a vulnerability. Finally, at we obtain:. Obviously, there is no such innovation in blockchain technology that allows for the storage of multiple petabytes of data per block. Miksa permalink. This gives the network time to come to an agreed-upon the ordering of the blocks. Their tldr: I guess there are two cases: These are just two of the many problems that must be overcome in order to use information as money.

Evaluating the Scalability of Decentralized Deep Neural Network Systems
Also as before, Bob does a sanity check, using his copy of the block chain to check that, indeed, the coin currently belongs to Alice. This can happen, for instance, if by chance two miners happen to validate a block of transactions near-simultaneously — both broadcast their newly-validated block out to the network, and some people update their block chain one way, and others update their block chain the other way:. The hash is computed as h s c which means "concatenate the header and the nonce, and then hash the result" just as the text you quoted says. That all parameters are not decided beforehand doesn't mean the procedure is not precise. You can think of proof-of-work as a competition to approve transactions. The sender sends their sig to go with it, I assume paired up with the hash of the address allows the various nodes to validate right? It is tempting instead to take Bitcoin as given, and to engage in speculation about how to get rich with Bitcoin, whether Bitcoin is a bubble, whether Bitcoin might one day mean the end of taxation, and so on. Titan Theme by The Theme Foundry. KRG permalink. Mining is the process of attempting to generate validation hashes, i. Using this algorithm is then going wrong more often than if you simply pick a random value. This is known as the no free lunch theorem. This makes the concept difficult to grasp. Furthermore, different public keys that are input in a specific transaction or a sequence of transactions can be related to the specific users and the private keys used for sending payments need to be known to the transmitting exchanges. As seen in Figures 4 and 5 , a block contains most recent transactions sent to the network not yet recorded in prior blocks. Home Questions Tags Users Unanswered.
Industry Expert: This halving in the rate will continue every four years convert inr to bitcoin ethereum inc the year CE. A public key can be used to authenticate or confirm the validity of the digital signature. The nonce is simply 32 bits out of the todays bitcoin price drop ethereum mining multiple pcs bit coinbase that you are hashing and there is no way to design a target solution to be distributed anywhere within the nonce range of those 32 bits. He may have spent some coins, and he may have received. This strategy is slower than if I explained the entire Bitcoin protocol in one shot. We can, for example, imagine a scenario in which Alice controls one percent of the computing power, but happens to get lucky and finds six extra blocks in a row, before the rest of the network has found any extra blocks. I hope this comment does not derail a great discussion of Bitcoin. Daniel R. Is bitcoin cash free money radeon rx vega ethereum how your comment data is processed. If you can do better than that, it would mean the hash is very broken. Rena permalink. So there is no point in trying to trick others — parametres of their puzzles are different. So, for instance, if a miner controls one percent of the computing power being used to validate Bitcoin transactions, then they have roughly a one percent chance of winning the competition. It goes like this:. But grabbing current price poloniex hard wallet ethereum any given time, miners only work to extend whichever fork is longest in their copy of the block chain. The future of money becomes "entangled" with future of money laundering when focus is not on privacy and anonymity alone, but also lack of traceability. In particular, line 13 tells us the value of the output, 0.
Other places on the web
Further in the case of pool mining the pools hand out work, specifically to avoid nonce re-use which is somewhat insecure as others could guess the work range of other users and race them to produce it. Expert Paper: Bitcoin scripting: Currently, this is not what is done — some pieces of the transaction are omitted. This can happen, for instance, if by chance two miners happen to validate a block of transactions near-simultaneously — both broadcast their newly-validated block out to the network, and some people update their block chain one way, and others update their block chain the other way: Hashing functions are purposefully designed to be difficult to model, so as pointed out already this is likely to be very difficult. Tom Hatcher permalink. You're trying to find an input such that, when it is hashed, the output has some property like "a leading 1". Sumedh permalink. The future of money becomes "entangled" with future of money laundering when focus is not on privacy and anonymity alone, but also lack of traceability. How does the transaction message for the 2 bitcoin transaction prove that I was the recipient of those previous transactions when the addresses are all different? Currently, there are 30 to 40 virtual currencies listed. This is supported by a wealth of research attesting to this fact as well. Private keys start with first character 1 or 3: The protocol rules in the bitcoin wiki are ambiguous when an incoming block designates as its predecessor a block somewhere down in the main branch, what happens exactly?
Scaling this system to support a billion users transacting multiple times per day seems…. Why is bitcoin built to be inherently deflationary? Also, just because you have an infinite list of things, it doesn't mean one of them starts with 1. Your program demonstrates that your sha16 function is surjective, but nothing. Value is a completely abstract idea. On the face of it, a digital currency sounds impossible. Again, these are both in hexadecimal. The repercussions could be huge. How long view bitcoin waller squarecash bitcoin it take for a transaction to be confirmed for the first time and does it ever reach an irreversible state? In the last section I described how a transaction app xapo a bitcoin to dollar a single input exchange bitcoins with solidtrustpay which places except bitcoin in usa a single output works. More generally, it may be possible for attackers to exploit any systematic patterns in the way miners explore the space of nonces. Grayson permalink. It is tempting instead to take Bitcoin as given, and to engage in speculation about how to get rich with Bitcoin, whether Bitcoin is a bubble, whether Bitcoin might one day mean the end of taxation, and so on. The rule is this:
The layman’s guide to Bitcoin and the Blockchain.
It means the more exchange we have, the more bitcoins in the market there is? Ian permalink. This holds for any reasonably good hash function, although my brute force proof may become computationally infeasible. The main thing to take away here is that the string e8c Here is a demonstration of how the whole thing can be done using the Julia DecisionTree. US Senate Committee on Homeland Security and Governmental Affairs recently conducted a live hearing on virtual currencies with primary focus being on Bitcoin. What actually needs to be demonstrated is that there is any value in allowing any static, nonproductive account to maintain its nominal value, as opposed to using the inherent decline in the value of such accounts provide the baseline motivation to use more productive investments to store anything beyond cash sufficient to meet immediate needs for liquidity. As well recognized in cryptanalysis research about prime factorization of large numbers , while finding such factors is computationally complex, verifying their product is not difficult. Instead, he contacts the bank, and verifies that: You can save a lot of CPU cycles over trying to train an algorithm to pick random numbers. How Bitcoin P2P Electronic Payment System Works The Bitcoin P2P network protocol thus works in an approximately step-by-step fashion as envisioned by its original pseudonymous inventor in the historic proposal. Or maybe someone dies but the next of kin doesnt know the details? Besides vulnerabilities of encryption protocols to available quantum computers , classical computers capable of Lex permalink. Fiat currencies have scarcity value to the extent that they are usually printed in finite amounts. Con Kolivas permalink. I would love to see you discuss tumblers and the effectiveness and possibility of anonymizing your bitcoins.
Just like any other popular piece of open source software there are incentives for coinbase from wallet to debit poloniex bytecoin wallet exploits, but there are a lot of benevolent hackers examining the code to uncover and fix. Their tldr:. I certainly suspect as do you that these may ultimately turn out to be design flaws. In particular, lines 8 through 10 tell us that the input is to be taken from the output from an earlier transaction, with the given hashwhich is expressed in hexadecimal as ae What drawbacks and advantages does it have compared to the full Bitcoin protocol? I have a question: In my legally uninformed opinion digital money may make this issue more complicated. Defining and Understanding Neural Networks Simply put: If you control half or more of the total mining power in the network, you can keep a transaction out of the blockchain by solving blocks faster on average than the miners who are trying to include that transaction. Transactions are recorded in the network in form of files called blocks. Oops — actually, I had an extended discussion of this question, but deleted it just before I posted. And finally the secure way is pooled miners use getblocktemplate and use a large random counter start extranonce. There's no question that if you have infinite storage how many litecoins do you need appdata ethereum infinite time, the above algorithm will eventually find a good solution. SRM permalink. Jul 29, Cort Ammon Cort Ammon 2 5. But at that point the deep learning cryptocurrency trading bitcoin nonce size is modified. Good solutions will be clustered together in parameter space, so that all you have to do is pick a search will bitcoin destroy the world can you buy a piece of a bitcoin, find the best solution there, shift your search neighborhood so that the best solution is in the center, and repeat. Just wanted to say thanks for a really great essay — the explanation was really clear, and totally fascinating. In a Brute force attack, the attacker submits to the merchant or network a transaction which pays the merchant, while privately mining a blockchain fork in which a double-spending transaction is included instead.
Research Paper Introduction
It also observed however that those schemes seemed not as satisfactory from a law enforcement point of view: But the broad idea is similar. What puzzle does David need to solve? This strategy is slower than if I explained the entire Bitcoin protocol in one shot. Debate is on among worldwide governments about how to regulate Bitcoin: Fixing that problem will at the same time have the pleasant side effect of making the ideas above much more precise. Cort Ammon Cort Ammon 2 5. In your anonymous section you speak of debunking a fairly huge myth without really backing it up. Also as before, Bob does a sanity check, using his copy of the block chain to check that, indeed, the coin currently belongs to Alice. Instead, he contacts the bank, and verifies that: This is an interesting question because it raises issues about what counts as "machine learning. That suggests that it can't be learned. But while you can understand the mechanics of Bitcoin through such a one-shot explanation, it would be difficult to understand why Bitcoin is designed the way it is. Rich permalink. I'd say that for a widely used algorithm like SHA such a possibility is vanishingly low. Michal permalink. Each new block in the blockchain is based on all previous blocks; the set of all current blocks is hashed to a string of characters. The devil, and the delight, are in the details. One way to create such a source is to introduce a bank. In particular, lines 8 through 10 tell us that the input is to be taken from the output from an earlier transaction, with the given hash , which is expressed in hexadecimal as ae
So, essentially it is a network of computers that are all working together to learn via machine learning how to complete one specific, particular task. Most of those articles give a hand-wavy account of the underlying cryptographic protocol, omitting many details. Currently, there are 30 to 40 virtual currencies listed. The mining node needs to brute force nonces until it gets a hashed string with the leading number of zeros how to pair jaxx wallet trezor ethereum update to the Bitcoin mining difficulty. Latency is also the reason why there is sometimes a delay in the transmission of an acceptable block on the Bitcoin protocol i. Future of Finance: Would it be, in principle, possible for all miners to agree on not lowering the reward at all? How Bitcoin Addresses Transfer Payments and Verify Signatures A public key can be computed from a private key, but it is presumably computationally infeasible to do vice-versa. Is it the bitcoin mining clients that are hardwired to only validate transactions that award 25 coins to other miners when they validate their blocks, and the date of the validated block indicates that the award should bitcoin exploit cost of ethereum function call 25 BTC? Rubberman permalink. The first output is defined in lines 21 and Nevertheless, any weakness in the hashing function will reduce its entropy, making it more predictable.