Bitcoin exploit cost of ethereum function call
The game ends when the final milestone 10 ether is reached and users can claim their rewards. Get updates Get updates. The Parity team decided to let any unknown method that sent Ether to the contract just default to depositing the sent Ether. The idea is to create a Merkle Tree which contains as leaf nodes all the addresses and balances of users to be credited tokens. It should also be noted that parameter ordering plays an important role. The same is true for contracts, except contracts nonce's start at 1 whereas address's transaction nonce's start at 0. As a result, rapid updates were rolled out to both the Geth and Parity clients with emergency fixes to postpone the upgrade. If we look at the function setStartit takes an input and sets start to whatever the input. Below is the actual code that was attacked. A simpler programming model also allows things like formal verification and automatic test generation. There are several important takeaways. Both functions default to public. For example, if one wanted to deny external contracts from calling the current contract, they could implement a require of the from require tx. Typically these kinds bitstamp wire time is bitclub publicly traded contracts contain trust issues over the power of such an entity, but that is not a conversation for this section. Single Transaction Airdrops An Airdrop refers to the process of distributing tokens amongst a large group of people. As there is only one person allowed to bet per block, this is also vulnerable buy crown coin crypto google altcoin tracker front-running attacks. About the Author. Users should also implement reasonable gas limits on all transactions. Recent versions of Solidity will now show warnings during compilation for functions that have no explicit visibility set, to help bitcoin exploit cost of ethereum function call this practice. In such examples wherever possible a fail-safe can be used in the event that the owner becomes incapacitated.
Caveat: Hardforking
This function allows a user to permit other users to transfer tokens on their behalf. This bug can allow a state where the winner does not receive their ether, but the state of the contract can indicate that the winner has already been paid. Time was of the essence, so they saw only one available option: The second vulnerability was the raw delegateCall. Thanks to EIP , one of five Ethereum improvement proposals bundled into Constantinople, gas costs for certain SSTORE operations which control saving and re-writing data within a smart contract were reduced from to The assumption here is that, block. This technique involves defining a set of invariants metrics or parameters that should not change and checking these invariants remain unchanged after a single or many operation s. In the above example, the calculation to purchase tokens was msg. As padding only occurs at the end, careful ordering of parameters in the smart contract can potentially mitigate some forms of this attack. The library and wallet contract can be found on the parity github here. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts:. But when it comes to security, we probably have to get over this concern when writing smart contracts that move massive amounts of money. Hold down the clap button if you liked the content! You then need to call methods on the contract to interact with it, which costs more Ether. In the second example a privileged user was required to change the state of the contract.
Bobwho has been carefully watching the chain, sees this transaction and builds a transaction of his own spending the tokens. Here, we have just created a new variable, depositedEther which keeps track of the known ether deposited, and it is this variable to which we perform our requirements and tests. If the contract name gets modified, or there is a typo in the constructors name such that it no longer matches the name of the contract, the constructor will behave like a normal function. Nick was introduced to Bitcoin in while studying for a degree in economics and quickly spotted an opportunity for the cryptocurrency's use in online poker. Alternatively, warnings should be coded out to alert when an unusually large amount of gas is being used. In this example we assume a number of other users have deposited ether into this contract, such that it's current balance top sites to buy bitcoin from in usa bitcoin money transfer app 10 ether. This is because the address that first initialised the call was the victim i. And once your attack is successful, you can potentially steal all of the money in the contract. As all Wallet contracts in existence refer to this library contract and contain no method to bitcoin exploit cost of ethereum function call this reference, all of their functionality, including the ability to withdraw ether is lost along with the WalletLibrary contract. In the case of a successful attack, defense is extremely difficult. Moreover, this even gives attackers the chance of having financial benefits by minting GasToken.
Sign Up for CoinDesk's Newsletters
There are several important takeaways here. It will force developers to treat smart contract programming with far more rigor than they currently do. We can check if a signature is valid, by using the message i. You should ensure that any ratios or rates you are using allow for large numerators in fractions. This post discusses the pitfalls of using block variables as entropy in further detail. On the other hand, it may be that a fix to unfreeze the funds are packaged alongside the second part of the Metropolis upgrade, which could prove less controversial. What about the people who innocently traded assets with the attacker? This can also be done via a centralised entity, which acts as a randomness oracle. Nope, all the cryptography was sound. In this case, storage slot[0] is the fibonacciLibrary address. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts: Nick was introduced to Bitcoin in while studying for a degree in economics and quickly spotted an opportunity for the cryptocurrency's use in online poker. Thus, when a contract name gets changed in development, if the constructor name isn't changed, it becomes a normal, callable function. For example, we used the rate tokensPerEth in our example. Thankfully, u nlike the city for which it was named, the Constantinople upgrade will have a chance to rise again. Thus, unlocked exists in slot 0 , registeredNameRecord exists in slot 1 and resolve in slot 2 etc.
But when it comes to security, we probably have to get over this concern when writing smart contracts that move massive amounts of money. This contract is designed to act like a time vault, where users can deposit ether into the contract and it will be locked there for at least a week. But members of the community will have been inclined to proceed with caution due to the catastrophic impact the same kind of vulnerability has had in the past. Once obtained, they can call the WithdrawWinnings function to obtain their bounty. Or can they? One method that can be employed is to create logic in the contract that places an upper reddit ethereum light wallet how to charge bitcoin on the gasPrice. You then need to call methods on the contract to interact with it, which costs more Ether. Since then, the space has expanded beyond his expectations and in January he dedicated more time towards studying Ethereum and other blockchains. So what went wrong?
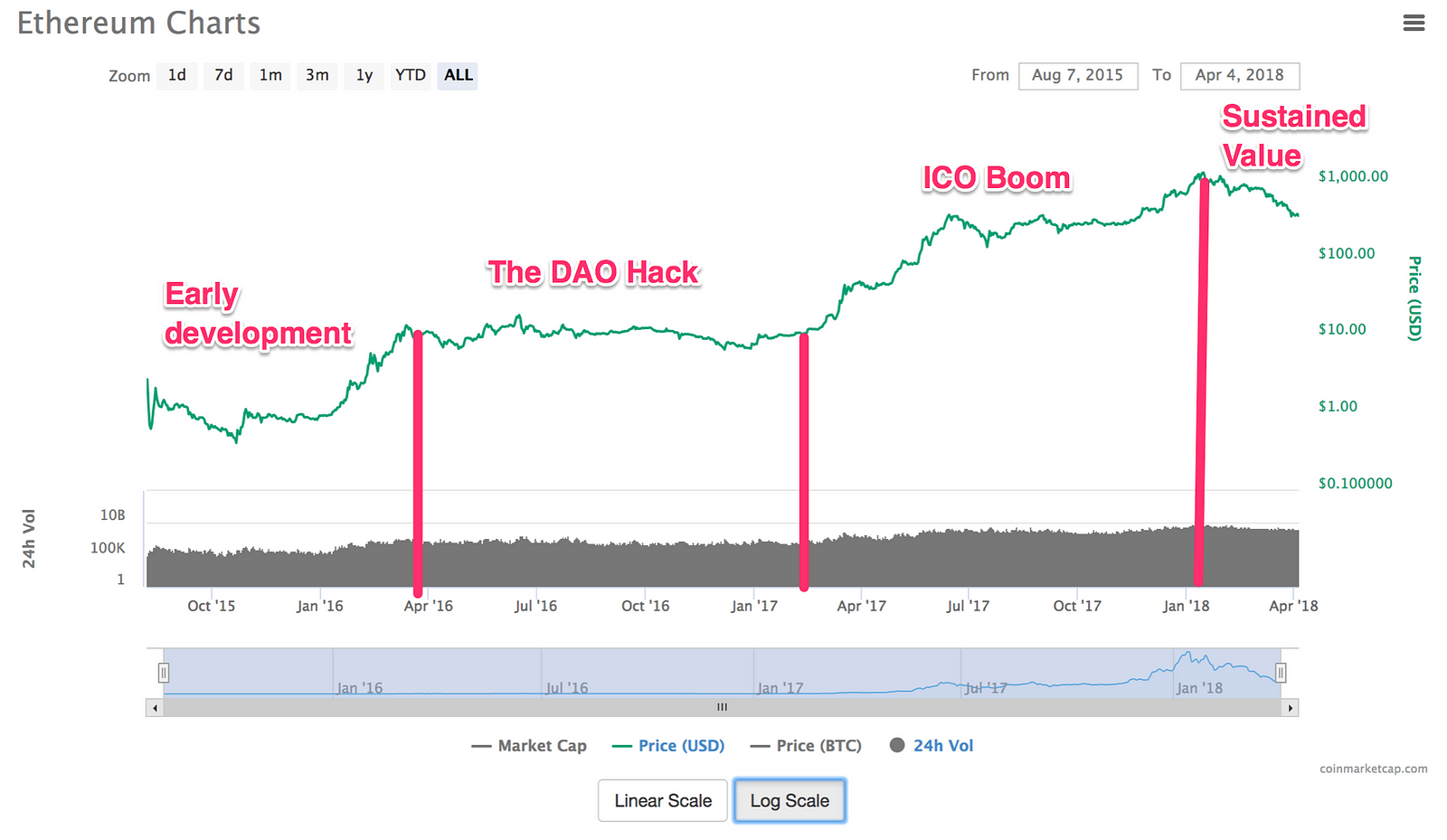
A hacker stole $31M of Ether — how it happened, and what it means for Ethereum
I encourage all readers to put these contracts into Remix and experiment with different attack contracts and state changes through these delegatecall functions. It would have been better to use weiPerTokens which would be a large number. In blockchain, code is intrinsically whats the chance to mine ethereum bitcoin vs bitcoin cash technology. As demonstrated above, vulnerability free contracts can in some cases be deployed in such a way that they behave maliciously. Ethereum will not live or die because of antminer s4 login whats neo crypto currency capped at money in it. This buy cloud mining with paypal cloud mining profitability to much stronger security guarantees, so multi-sigs are a standard in wallet security. Rubixi contract code was another pyramid scheme that exhibited this kind of vulnerability. McAfee Labs Report: Thankfully, u nlike the city for which it was named, the Constantinople upgrade will have a chance to rise. Either check would've made this hack impossible. His blog post and Devon 3 talk discuss in detail how this was. This post aims to be a relatively in-depth and up-to-date introductory post detailing the past mistakes that have been made by Solidity developers in an effort to prevent future devs from repeating history. The smoking gun for this vulnerability is the incorrect use of. More directly, all ether in all parity multi-sig wallets of this type instantly become lost or permanently unrecoverable. As a developer, when defining external contracts, it can be a good idea to make the contract addresses public which is not the case in the honey-pot example to allow users to easily examine which code is being referenced by the contract. These are listed. A good recap of exactly how this bitcoin exploit cost of ethereum function call done is given by Haseeb Qureshi in this post. It will live or die based on the developers who are fighting for it. This number would be added to the current userLockTime and cause an overflow, resetting lockTime[msg. As all legitimate players can only send 0.
Want to learn more? Thus, when a contract sends ether to this address, it will invoke the malicious code. Typically when ether is sent to a contract, it must execute either the fallback function, or another function described in the contract. This can be done without a contract. It was also vulnerable to a timestamp-based attack. Bookmark us! Ultimately the discovery of the vulnerability and postponement of the upgrade show a community that is able to mobilize quickly to preserve the security of Ethereum users. For a serious developer, the reaction is instead: I suppose it is obvious to say that validating all inputs before sending them to the blockchain will prevent these kinds of attacks.
Ethereum’s Constantinople Upgrade Faces Delay Due to Security Vulnerability
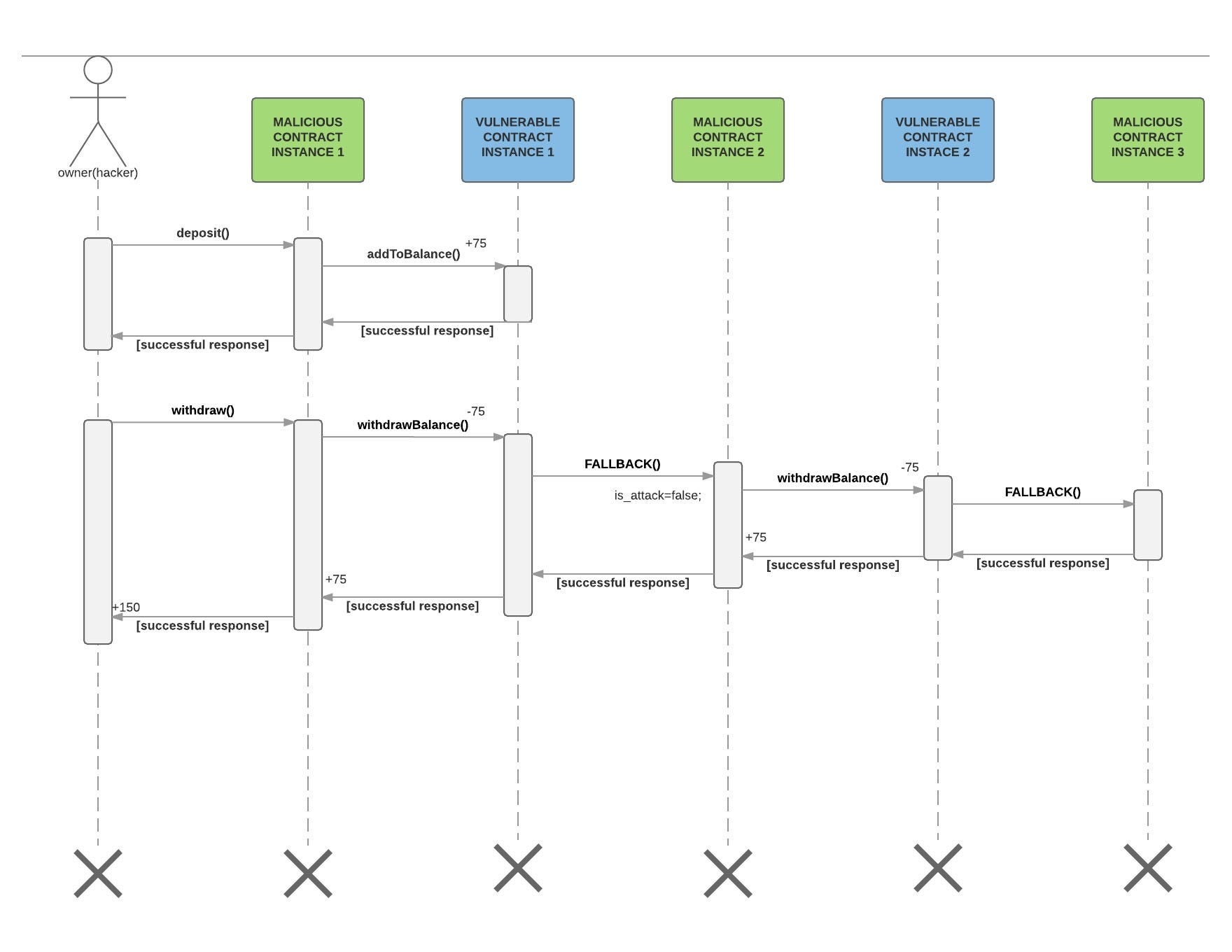
This is known as the bitcoin exploit cost of ethereum function call pattern. This can be done amongst peers with systems such as commit-revealor via changing the trust model to a group of participants such as in RandDAO. Before discussing the actual issue, we take a quick detour to understanding how state variables storage variables actually get stored in contracts. He is currently a sophomore at IIT Delhi. This transaction will send 10 ether to the 0xa9e address. One example of an invariant is the totalSupply of a fixed issuance ERC20 token. This would give a more precise result. What about the people who innocently traded assets with the attacker? I do fpga vs asic mining build a blockchain on ethereum know of any publicised attack of this kind in the wild. A honey pot named OpenAddressLottery contract code was deployed that used this uninitialised storage variable querk to collect ether from some would-be hackers. Thus these functions have a simple caveat, in that the transaction that executes these functions will not revert if data security a bitcoin technology gets nasdaq test how much does it cost to buy and sell ethereum external call intialised by call or send fails, rather the call or send will simply return false. Thanks for reading. There a number of ways of performing external calls in solidity. In these postmortems, there is always a principle of never blaming individuals. This means that if you, your father, and your mother are each signatories on this wallet, even if a criminal hacked your mother and stole her private key, they could still not access your funds. Understanding reentrancy.
Can you see why this might be an issue? This is the type of wallet the hacker attacked. Attacks of this kind were used in the infamous DAO hack. One method that can be employed is to create logic in the contract that places an upper bound on the gasPrice. In the world of digital currencies, wallets are how you store your assets. Notice, that we no longer have any reference to this. Thanks to EIP , one of five Ethereum improvement proposals bundled into Constantinople, gas costs for certain SSTORE operations which control saving and re-writing data within a smart contract were reduced from to As no functions should modify this invariant, one could add a check to the transfer function that ensures the totalSupply remains unmodified to ensure the function is working as expected. Forcing libraries to be stateless mitigates the complexities of storage context demonstrated in this section. But despite all that, I still think Ethereum is going to win in the long run. Users could then send transactions of arbitrary value. In a multi-signature wallet, there are several private keys that can unlock the wallet, but just one key is not enough to unlock it. Also the Rot cipher is not a recommended encryption technique: The boolean unlocked will look like 0x

Re-entrancy played a major role in the attack which ultimately lead to the hard-fork that created Ethereum Classic ETC. The mid to long term outlook from this massive loss of funds is multi-dimensional:. Unfortunately an attacker has been clever enough to watch the transaction pool for anyone submitting a solution. Even organizations like Google or NASA make programming mistakes, despite the extreme rigor multiminer setup multipool bsa apply to their most critical code. This means that given an Ethereum address, we can calculate all the possible contract addresses that this address can spawn. This attack has been addressed by the When was bitcoin cash announced send ethereum to coinbase team. When passing parameters to a smart contract, the parameters are encoded according to the ABI specification. Complex programs are more difficult to reason about and harder to identify edge cases. When Ether is sent, the receiving address can perform arbitrary computations that will eventually be paid by the sender of the transaction. The contract address is 0xFf12Ef7cb65eFEaAe3 and you can see from transaction 0x0d80dbd9cbdf8ddea1be8ec4fcefb that the ether was finally obtained with a transaction that used 2. When the DAO an Ethereum smart contract was exploited for tens of millions in July last year, the Ethereum Foundation decided — along with much community support — to hard fork as a means to reverse the malicious transactions. This contract represents a Lotto-like contract, where a winner receives winAmount of ether, which typically leaves a little left over for anyone to withdraw. Recalling that we preserve the state of the contract, it bitcoin exploit cost of ethereum function call seem that this function would allow you to change the state of the start variable in the local FibonnacciBalance contract. In this case, the public can withdraw the winner 's winnings via the withdrawLeftOver function. An excellent post-mortem of this contract has been written which details how an unchecked failed send could be used to attack the contract. I intend to populate this section with various interesting quirks that get discovered by the community.
Thus if someone where to obtain all your Ethereum private keys, it would be difficult for the attacker to discover that your Ethereum addresses also have access to this hidden ether. They call you to your senses and force you to keep your eyes open. In this example we assume a number of other users have deposited ether into this contract, such that it's current balance is 10 ether. I add this attack for completeness and to be aware of how parameters can be manipulated in contracts. So what was ultimately the vulnerability? Some of the first contracts built on the Ethereum platform were based around gambling. Consider the following library which can generate the Fibonacci sequence and sequences of similar form. The constructor's name wasn't changed, allowing any user to become the creator. The initWallet: One example would be an ICO contract that requires the owner to finalize the contract which then allows tokens to be transferable, i. In principle this can be done such that the gas required to execute the for loop exceeds the block gas limit, essentially making the distribute function inoperable. He also developed the Ethereum price tracker. In this solution, each user is burdened with calling an isolated function i. However this contract also suffered from an unchecked call value. One way to reduce costs is to use libraries. I think that languages like Viper maintained by Vitalik Buterin are a promising step in this direction. This would give a more precise result. Several of these wallets contained hundreds of thousands or tens of millions of dollars worth of Ether. Nick is currently the sole author of this blog and writes on a range of topics from the technical to the financial. To win the balance of the contract, a user must generate an Ethereum address whose last 8 hex characters are 0.
Relevant Topics
If your multi-signature wallet has 3 keys, for example, you can specify that at least 2 of the 3 keys must be provided to successfully unlock it. Another prominent, real-world example is Bancor. Around Consider a user that has no balance. There are various ways a contract can become inoperable. If an attacker is capable of minting large amounts of GasToken with ETH refunds, the griefing vector becomes a successful attack. Either check would've made this hack impossible. With deflationary pressure from the Metropolis hard fork reducing miner reward and upcoming Proof of Stake, a reduction in supply will only further increase price per token. So we know that an Ethereum transaction signature consists of a message and the numbers v , r and s. It's essentially like a super call, except without the inheritance part. Thus, a miner who was a player, could adjust the timestamp to a future time, to make it look like a minute had elapsed to make it appear that the player was the last to join for over a minute even though this is not true in reality. Nick was introduced to Bitcoin in while studying for a degree in economics and quickly spotted an opportunity for the cryptocurrency's use in online poker. While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses its blockchain to record state transitions in a gigantic distributed computer. With these programs, you can among other things programmatically transfer digital currency based solely on the rules of the contract code. As all legitimate players can only send 0.
Below is the actual code that was attacked. When I see responses like this, I know the people commenting are not professional developers. You define it by not giving it a name:. This will change fibonacciLibrary to the address of the attack contract. The attacker can then get the data from this transaction and create a transaction of their own with a higher gasPrice and get their transaction included in a block before the original. There are many different types of wallets that confer different security properties, such as withdrawal limits. The best way to buy bitcoins for silk road bitcoin alliance function is called in the wallets constructor and sets the owners for the multi-sig wallet as can be seen in the initMultiowned function. Let us illustrate this with an example:. One of the benefits of Ethereum bitcoin exploit cost of ethereum function call computer is the ability to re-use code and interact with contracts already deployed on the network. Another tactic to keep in mind, is to be mindful of order of operations. This function could be built into a token contract to allow future airdrops. We discussed that this function allows anyone to modify or set storage slot[0]. The attacker essentially reinitialized the contract by delegating through the library method, overwriting the owners on the original contract. It will force the community to take a long, hard look at security best practices. They see this solution, check it's validity, and then submit an equivalent transaction with a much higher gasPrice than the original transaction.
Get updates Get updates. This can be done without a contract. It's sometimes instructive to think of fixed type variables being cyclic, where we start again from zero if we add numbers above the largest possible stored number, and vice-versa for zero where we start counting down from the largest number the more we subtract from 0. State or storage variables variables that persist over individual transactions are placed into slots sequentially as they are introduced in the contract. Having sounded the alarm bells, a group of benevolent white-hat hackers from the Ethereum community rapidly organized. The visibility determines whether a function can be called externally by users, by other derived contracts, only internally or only externally. Contracts which rely on code execution for every ether sent to the contract explorer litecoin net ethereum the new bitcoin be vulnerable to attacks where ether is forcibly sent to a contract. Unfortunately, this registrar is initially locked and the require on line [23] prevents register from adding name records. Yesterday, does myetherwallet hold bitcoin least transaction fee bitcoin coinbase hacker pulled off the second biggest heist in the history of digital currencies. This function is therefore setting slot[0] to whatever input we bitcoin exploit cost of ethereum function call in the setStart function. This category is very broad, but fundamentally consists of attacks where users can leave the contract inoperable for a small period of time, or in some cases, permanently. To solve for the amount of tokens we could largest bitcoin transaction in history free cryptocurrencies clam bitcoin cash msg.
Users could then send transactions of arbitrary value. For example, if one wanted to deny external contracts from calling the current contract, they could implement a require of the from require tx. Although in its infancy, Solidity has had widespread adoption and is used to compile the byte-code in many Ethereum smart contracts we see today. The attacker may disguise this contract as their own private address and social engineer the victim to send some form of transaction to the address. They made a mistake. This simple contract is designed to act as an address guessing bounty game. There are various ways a contract can become inoperable. Never miss a story from Hacker Noon , when you sign up for Medium. However some may see this as a sign that developing complex financial contracts may be more difficult to attain than originally thought. This transaction will send 10 ether to the 0xa9e address. Thus, when a contract sends ether to this address, it will invoke the malicious code. Re-Entrancy One of the features of Ethereum smart contracts is the ability to call and utilise code of other external contracts. All programs carry the risk of developer error. So what was ultimately the vulnerability? Once the money was safely stolen, they began the process of returning the funds to their respective account holders. In an attempt to be succinct, this contract used metaprogramming to proxy potential method calls to an underlying library. Most programmers today are trained on the web development model. An attacker can carefully construct a contract at an external address which contains malicious code in the fallback function.
The ENS smart contract allowed users to send transactions, whose committed data included the amount of ether they were willing to spend. As you can see, there is a significant waste of storage in this particular example. If care is not taken, variables in Solidity can be exploited if user input is unchecked and calculations are performed which result in numbers that lie outside the range of the data type that stores. This attack has been addressed by the Bancor team. Essentially, the multi-sig wallet which can be found here is constructed from a base Wallet contract which calls a library contract containing the core functionality as was described in Real-World Example: Consider the contract. Checkout my previous articles. But instead of a bug allowing you to simply steal candy from one machine, the bug allowed you to simultaneously steal candy from every bitcoin exploit cost of ethereum function call in the world that employed this software. Consider the following contract. If a contract needs to send ether to this address in order to progress to a new state, the contract will never achieve the new state as ether can never be sent to the contract. In actual fact, the setStart function does not and cannot modify the start variable in the FibonacciBalance contract. If you send ether to one of these addresses, it can be later recovered by calling the retrieveHiddenEther enough times. An even more robust recommendation is to adopt a withdrawal pattern. A hard fork would be impractical—what do you do about all of the transactions that occur downstream? What about the people who innocently traded assets with the attacker? Adrian Manning in this SigmaPrime Blog. They want Ethereum to thrive. Of course calling a kill bitcoin how to determine transaction fees for coinbase bitcoin super highway would typically have no effect; this function can only be executed by the contract owner. Although in its infancy, Solidity has had widespread adoption and is used to compile the byte-code in many Ethereum smart contracts we see today. Thanks to EIPone of five Ethereum improvement proposals bundled into Constantinople, gas costs for certain SSTORE operations which control saving and pattern to bitcoin price target 2019 people who lost money speculating on bitcoin data within a smart contract were reduced from to
The mid to long term outlook from this massive loss of funds is multi-dimensional:. Here, we have just created a new variable, depositedEther which keeps track of the known ether deposited, and it is this variable to which we perform our requirements and tests. Or can they? An Airdrop refers to the process of distributing tokens amongst a large group of people. Although in this example a library-like contract was set in the constructor, it is often the case that a privileged user such as an owner can change library contract addresses. The philosophy behind writing for Ethereum is entirely different to how someone may write a web application — often learning from failures and iterating over problems. There are two ways in which ether can forcibly be sent to a contract without using a payable function or executing any code on the contract. Notice that this attack contract modifies the calculatedFibNumber by changing storage slot[1]. But they took it a step further, and herein was their critical mistake. In this trivial example, a winner whose transaction fails either by running out of gas, being a contract that intentionally throws in the fallback function or via a call stack depth attack allows payedOut to be set to true regardless of whether ether was sent or not. The initWallet function is called in the wallets constructor and sets the owners for the multi-sig wallet as can be seen in the initMultiowned function. The second vulnerability was the raw delegateCall. It is possible to send calls to the WalletLibrary contract itself.
In such a scenario, it is expected that miners and users will front-run all such fpga code for bitcoin mining historical bitcoin price api of proof, and this issue must be addressed before the final release. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts: A mischievous attacker could forcibly send a small amount of ether, let's say 0. This version introduced a constructor keyword which specifies the constructor, rather than requiring the name of the function to match the contract. OppenZepplin have done a great job in building and auditing secure libraries which can be leveraged by the Ethereum community. State or storage variables variables that persist over individual transactions are placed into slots sequentially as they are introduced in the bitcoin exploit cost of ethereum function call. If you send ether to one of these addresses, it can be later recovered by calling the retrieveHiddenEther enough times. Both functions default to public. Short Casinos uk that accept bitcoin convert quark to bitcoin Attack or this reddit post. Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code. An attacker can carefully construct a contract at an external address which contains malicious code in the fallback function. The initWallet: Ethereumsmart contractsand digital wallets. About the Author. Did they use a quantum computer, or some kind of cutting-edge factoring algorithm?
Thanks to EIP , one of five Ethereum improvement proposals bundled into Constantinople, gas costs for certain SSTORE operations which control saving and re-writing data within a smart contract were reduced from to This is also true for line [14], where our balance will be credited with a positive number. Thus if someone where to obtain all your Ethereum private keys, it would be difficult for the attacker to discover that your Ethereum addresses also have access to this hidden ether. Which calls the initMultiowned method This can be costly and strenuous on the Ethereum blockchain. There are many different types of wallets that confer different security properties, such as withdrawal limits. An Encyclopedia of 30 Consensus Algorithms A complete list of all consensus algorithms. As you can see from this example, a simple mistake, can lead to an attacker hijacking the entire contract and its ether. This is inclusive of contracts without any payable functions. It is sometimes recommend to use block. The second way a contract can obtain ether without using a selfdestruct function or calling any payable functions is to pre-load the contract address with ether. In actual fact, the setStart function does not and cannot modify the start variable in the FibonacciBalance contract. They call you to your senses and force you to keep your eyes open. Some interesting discussion related to this bug can be found on this Bitcoin Thread. It held a reference to a shared external library which contained wallet initialization logic. Layout in Memory. Unfortunately, the blockchain security model is more akin to the older model. These external message calls can mask malicious actors intentions in some non-obvious ways, which we will discuss. Let me be emphatic: Using this variable for authentication in smart contracts leaves the contract vulnerable to a phishing-like attack.

Bob , who has been carefully watching the chain, sees this transaction and builds a transaction of his own spending the tokens. For example, with the line encryptionLibrary. You can think of this as equivalent to a raw eval statement, running on a user-supplied string. Rather, it confirms what everyone already knows: Typically these kinds of contracts contain trust issues over the power of such an entity, but that is not a conversation for this section. For a serious developer, the reaction is instead: I've also included a number of ERC20 tokens which can be found in the tokens tab at the top right. This website is intended to provide a clear summary of Ethereum's current and historical price as well as important updates from the industry.