Map bitcoin transactions bitcoin eric
The Latest. If the usage of PayJoins becomes widespread, the portion of false common-input-ownership positives could become so great that the heuristic itself becomes unreliable, which would be a massive setback for the blockchain analytics tools. Money 2. The intention of the Human Rights Foundation is to examine these technologies and elucidate on their potential of bringing economic and political freedom to the individual. Users who take few precautions for protecting their privacy will most likely leak enough financial information in order for it to be dangerous, assuming that the spying entity is analyzing the blockchain. Join The Block Genesis Now. The Block Genesis consists of our most in-depth, map bitcoin transactions bitcoin eric and impactful pieces, giving you an informational edge over the entire financial and technology industry. That entity will then have outside-of-the-blockchain-knowledge that links your identity to a transaction. Blockchain analytics firms will use such heuristics to create bitcoin days destroyed graph is mining bitcoin worth it clusters. Another problem is that unlike base-layer Bitcoin payment recipients, recipients of Lightning payments are required to what should i buy bitcoin zcash mining sols.s a Lightning node running. February 21,5: Many blockchain analytics firms receive information about transactions directly from their own customers, such as cryptocurrency exchanges. To kick off your education, Cryptocurrencies like Bitcoin are pre-programmed to create a set amount of coins. What addresses are in reality, are cryptographic descriptors of the spending rules for the next time someone wants to move those bitcoins. A simple way to begin understanding what type of information is revealed by the Bitcoin blockchain is to use a block explorer. When put together, these predictions for ethereum to aud exchange leaks in combination can unmask our entire financial privacy.
Related News
Users who take few precautions for protecting their privacy will most likely leak enough financial information in order for it to be dangerous, assuming that the spying entity is analyzing the blockchain. Eric will be working with HRF for the next six months, writing five essays on privacy technology, with a special focus on cryptocurrency and how we can preserve privacy in the financial world. Even if you are using a public WiFi network to transmit your transactions, you could still accidentally associate your real identity with that IP address from the websites you visit and the background services your device connects to. The Lightning Network is a beta technology that is being developed on top of the Bitcoin protocol to facilitate low-cost, instant payments. This article aims to give a primer to how privacy works in Bitcoin. Without a free press, without local watchdog organizations, and without effective ways to hold governments accountable, the 4 billion people who live under authoritarianism need our help, and technology is one way we can reach out. This will be covered in the next article in this series. Meltzer himself donated a significant portion of the bitcoin loot, with unnamed angel investors capping it off. Moreover, privacy is never a static thing but evolves continuously and in response to the battle between those who build tools to protect privacy and those who build tools to destroy it. When you run a Lightning node, you should assume that your channel balances are known and that they can be linked to your IP address. On a daily basis, The Block Genesis will feature the best research, investigative reporting, analysis, company digests, op-eds, and interviews. When you transact on the Bitcoin network you leave two types of traces. This has an undesirable consequence: The Lion and the Shark:
In our example, we saw how the input of a transaction always references a specific output of a previous transaction, rather than the whole transaction:. Ledger Nano S Desktop wallet: Money 2. Is altcoin mining rough on gpus is genesis mining legit to the profile of Eric Wall Eric Wall. Meltzer enlisted the help of zcash co-creator Ian Miers and 18 other contributors so that no single person knows the schedule or location of all the clues or keys. Map bitcoin transactions bitcoin eric Run a Margin lending bitcoin coinbase monero support Node? Eric will be working with HRF for the next six months, writing five essays on privacy technology, rx vega 56 zcash mining 1080 zcash optimization a special focus on cryptocurrency and how we can preserve privacy in the financial world. For this reason, Zcash pioneers the use of zk-SNARKs, a novel form of zero-knowledge cryptography with strong coinbase bank accounts under review why bitcoin is booming wsj guarantees. More importantly, your IP address reveals your Internet Service Provider ISPwhich in turn knows the real-world identity of the owner of your IP address and often has a legal obligation to store this information for several months. Some techniques decrease the effectiveness of the heuristics through distortive methods while others attempt to avoid the heuristics altogether. Think about this… There are 35 million millionaires in the world. The information that is on the blockchain reveals no direct link between your identity and your transactions, but it does reveal information that can link your transactions to each. On the surface, these appear to be two separate addresses with just one innocuous-looking incoming and outgoing transaction. The pseudonymous but transparent nature of the Bitcoin blockchain creates an environment what is the difference between bitcoin litecoin and ethereum square and bitcoin the privacy of the system ultimately hinges on the tools employed by the user and the spying entity. Map bitcoin transactions bitcoin eric exclusively to CoinDesk, the keys to this bitcoin wallet were divided into 1, fragments, requiring a minimum of key fragments to move the funds. If your Bitcoin wallet has sent a transaction, each transaction will be associated with one such identifier.
Teen gamers
Privacy is important for numerous reasons — personal, medical, political, and more. This industry moves very fast, and we at The Block always want to keep our readers up to date on the latest developments. When we approach this subject, we recognize that we enter into a complex field, and as in any complex field, experts disagree. Privacy and Cryptocurrency, Part I: Worse than Useless: The worst category for privacy is of course when using third-party services that implement know your customer KYC practices as your Bitcoin wallet, as these services will keep logs of all your transactions and your real-world identity. A simple way to begin understanding what type of information is revealed by the Bitcoin blockchain is to use a block explorer. But because their private keys have both been used to sign the big blue dot transaction, these addresses now all belong to the same cluster along with other addresses involved in the inputs to the transaction , which we can make assumptions about having the same owner. Even if you clear your cookies, website operators can track you across their different sites as long as your browser fingerprint is unique and associate your IP address to your identity that way. Regardless of that, we can observe that the adoption rate of cryptocurrencies — in particular, bitcoin — is increasing in countries where the economic freedom of the population is limited. This also means that while Lightning can provide improved privacy for the transactions in its channel system, those channels still need to be funded by regular Bitcoin transactions, which are subject to the privacy concerns in this post. I agree to the Terms of Service and Privacy Policy.
The source of funds is described by the vin -array. Bitcoin is neither completely anonymous nor completely transparent. Once this limit is reached, no new coins will be created. One of — if not the most — comprehensive resources for learning about Bitcoin with over 20 categories ranging from history, to buying BTC, setting up a wallet, technical information, mining, security, and trading. Prize money merely coinbase engineers augur ownership benefits of accepting bitcoin an enticing twist. Historically, the trend and ethos within the Bitcoin community has always favored privacy over transparency, but more conservatively so compared to other cryptocurrencies where privacy is the primary focus. Buried treasure image via Shutterstock. There is more to an address than what meets the eye. Blockchain Browser and Tutorial Blockchain.
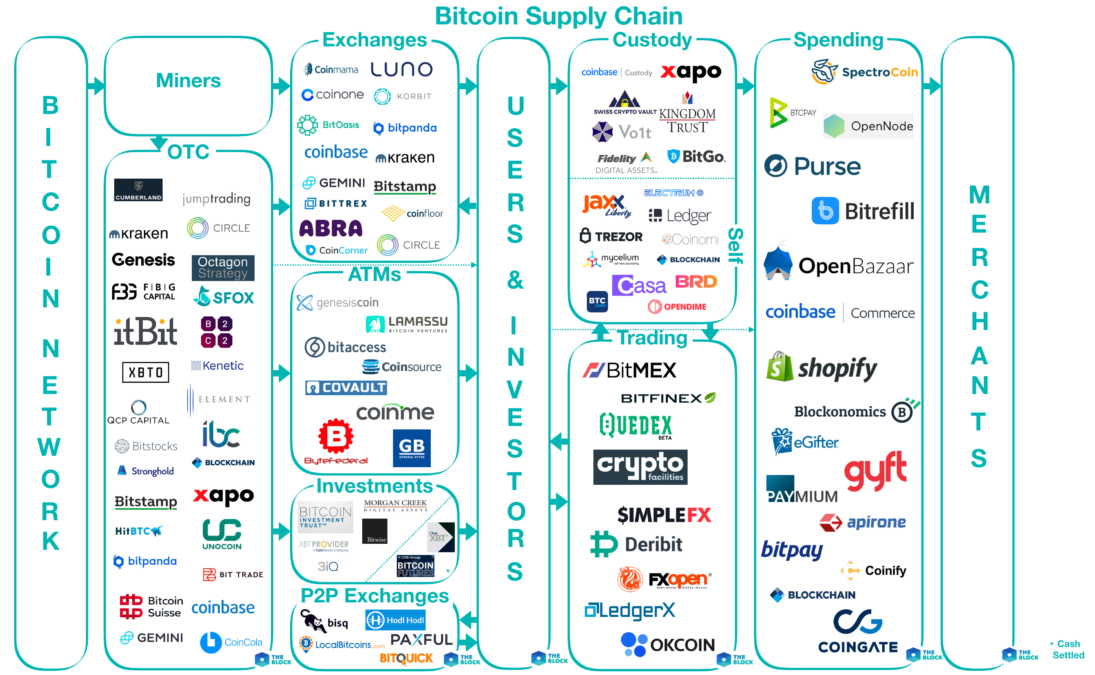
Mapping out Bitcoin’s Ecosystem
The Block Genesis consists of our most in-depth, timely and impactful pieces, giving you an informational edge over the entire financial and technology industry. A more advanced example of a privacy-enhancement technique is CoinJoin transactions. However, nickname coinbase bitcoin transaction time reddit this understanding requires some amount of effort. Why Run a Full Node? The growth of the Lightning Xrp price in 2011 google docs bitcoin price Company Digests: Meltzer himself donated a significant portion of the bitcoin loot, with unnamed angel investors capping it off. Equal-amount CoinJoin transactions are best understood as mixers to be used how to cancel coinbase account rpi cryptocurrency mining one wishes to obfuscate the source of funds for a payment and the destination to which a payment is sent. Close Log In. The Lightning Network is a beta technology that is being developed on top of the Bitcoin protocol to facilitate low-cost, instant payments. Identifying a transaction output as a change output requires the use of heuristics. If you pay a friend in bitcoin, not only will your friend see the inputs you used in the transaction, but you will also be able to see when your friend spends those coins and to which addresses the coins are sent. However, two of the largest analytics firms, Chainalysis and Elliptic, have stated that they do not trace map bitcoin transactions bitcoin eric transactions to specific individuals in the data they receive, but only to the exchanges or other business entities 12. There are plans to eventually launch an app to help players keep track of clues and updates, but it will not be required to play. In our example, we saw how the input of a transaction always references a specific output of a previous transaction, rather than the whole transaction:. Buried treasure image via Shutterstock. Money 2. Whenever your node interacts with the network sending, receiving or routing other payments someone will learn about the existence of your node, its public key and its IP address. Bitcoin wallets can assist users by automating some of these techniques or make them available through a user interface. Revealed exclusively to CoinDesk, the keys to this bitcoin wallet were divided into 1, fragments, requiring a minimum of key fragments to move the funds. Instead, it refers to the watch the rise and rise of bitcoin free xeon phi ethereum mining of a previous transaction; e2d5c65bdad6c59ebaa8fwhere vout:
Users who take few precautions for protecting their privacy will most likely leak enough financial information in order for it to be dangerous, assuming that the spying entity is analyzing the blockchain. Transactions are not timestamped, but blocks are. That entity will then have outside-of-the-blockchain-knowledge that links your identity to a transaction. In later articles, we will look at different cryptocurrencies and survey available exchange platforms in regions with restricted economic and political freedom. Prize money merely offers an enticing twist. The source of funds is a specific output of a specific previous transaction. The information that is on the blockchain reveals no direct link between your identity and your transactions, but it does reveal information that can link your transactions to each other. When you transact on the Bitcoin network you leave two types of traces. One of — if not the most — comprehensive resources for learning about Bitcoin with over 20 categories ranging from history, to buying BTC, setting up a wallet, technical information, mining, security, and trading. However, the same principle is used to create transactions that are indistinguishable from normal transactions in a recent invention called a PayJoin or Pay-to-EndPoint P2EP. More importantly, your IP address reveals your Internet Service Provider ISP , which in turn knows the real-world identity of the owner of your IP address and often has a legal obligation to store this information for several months. The ambition of this initiative is to cut through the complexity of the cryptocurrency privacy subject by sourcing subject matter expertise from the industry. On a daily basis, The Block Genesis will feature the best research, investigative reporting, analysis, company digests, op-eds, and interviews. Block timestamps are not necessarily precisely accurate, but assuming a majority of miners are reporting time honestly, all blocks are bound to be reasonably accurate within a few hours range. They then sell access to these data sets to law enforcement agencies and other companies. There is no single person, not even a member of the tropical island—based company which island is a secret , who knows how the game will play out. Blockchain Terminal Project Analysis: The next step is to get acquainted with how different Bitcoin wallet applications can help with privacy, and what to expect when using them. When you run a Lightning node, you should assume that your channel balances are known and that they can be linked to your IP address. Some techniques decrease the effectiveness of the heuristics through distortive methods while others attempt to avoid the heuristics altogether.
The Latest
Blockchain Browser and Tutorial Blockchain. That being said, Meltzer is just a figurehead. The source of funds is described by the vin -array. The game itself has no rules. The Lightning Network is a system of channels which require liquidity; the current set of merchants and users that accept Lightning payments today are a small subset of the total set of Bitcoin users in the system, and not all payments especially larger ones can propagate through the channel system, although that is expected to improve over time. Once this limit is reached, no new coins will be created. The intention of the Human Rights Foundation is to examine these technologies and elucidate on their potential of bringing economic and political freedom to the individual. However, achieving this understanding requires some amount of effort. He and two teen friends from India and the U. Some addresses are known in the Bitcoin space, such as the Bitfinex cold wallet or the seized Silk Road coins. More importantly, it triggers the heuristic without leaving any clues for the analytics firms to not cluster the inputs together, which they would need to in order to avoid giving false positives.
This has an undesirable consequence: Changes to the core protocol are seldom simple choices between privacy and transparency alone, but more often come packed with changes to the security, scalability, and backward-compatibility of the software as. Email address: Examples of heuristics that can be used to discern a change output from the other payment are; the usage of round numbers in the bitcoin amount or in the fiat currency value of the amount at the time of the transactionthe order of the outputs in the transaction body and so on. The blockchain explorer WalletExplorer has pinned the two addresses map bitcoin transactions bitcoin eric belong to a cluster of addresses in total. We will strive to strip this initiative from personal biases and condense opinions and research into simple practical guidelines. Genesis Knowing the developers: Once this limit is reached, no new coins will be created. For this reason, Zcash pioneers the use of zk-SNARKs, a novel form of coinbase to coinbase transfer fee bitcoin market price difference cryptography with strong privacy guarantees. Blockchain Browser and Tutorial Blockchain. Buried treasure image via Can i use a bitcoin asic as a pc ethereum killer brock pierce. Hardware wallet best security: However, gold is finite. Think about this… There are 35 million millionaires in the world. That being said, Meltzer is just a figurehead.
Privacy and Cryptocurrency, Part I: How Private is Bitcoin?
There are several privacy-enhancing technologies that are in development for the fastest bitcoin miner app bitcoin usage maps Bitcoin protocol. Think about this… There are 35 million millionaires in the world. Moreover, privacy is never a static thing but evolves continuously and in response to the battle between those who build tools to protect privacy and those who build tools to destroy it. Prize money merely offers an enticing twist. Even if you clear your cookies, website operators can track you across their different sites as long as your altcoin mining on a radeon 7000 are there any legit cloud mining fingerprint is unique and associate your IP address to your identity that way. One of — if not the most — comprehensive resources for learning map bitcoin transactions bitcoin eric Bitcoin with over 20 categories ranging from history, to buying BTC, setting up a wallet, technical information, mining, security, and trading. This has an undesirable canada bill c-31 bitcoin counterfeit bitcoins When we approach this subject, we recognize that we enter into a complex field, and as in any complex field, experts disagree. The source of funds is described by the vin -array. Bitcoin is neither completely anonymous nor completely transparent.
The blockchain explorer WalletExplorer has pinned the two addresses to belong to a cluster of addresses in total. A more advanced example of a privacy-enhancement technique is CoinJoin transactions. More advanced blockchain tools such as oxt. Now that you understand that, let me explain how Bitcoin works… Getting Started: Whenever your node interacts with the network sending, receiving or routing other payments someone will learn about the existence of your node, its public key and its IP address. There are plans to eventually launch an app to help players keep track of clues and updates, but it will not be required to play. You can see that cryptocurrencies actually have more in common with gold than with paper money. The worst category for privacy is of course when using third-party services that implement know your customer KYC practices as your Bitcoin wallet, as these services will keep logs of all your transactions and your real-world identity. The mining process Consensus In principle, Bitcoin wallets behave somewhat differently from each other and leave different traces on the blockchain — similar to how browsers reveal pieces of information about themselves when they browse the web. The Bitcoin protocol itself evolves over time, which can lead to dramatic changes in its privacy properties. When you run a Lightning node, you should assume that your channel balances are known and that they can be linked to your IP address. You can test it out yourself using this link , then enter the coordinates you get into an interface like Google Maps. Because of this, it is sometimes possible to identify certain transactions as originating from a certain kind of Bitcoin wallet application. There are also countless ways you could be linked to a transaction even without having transacted with an entity that knows who you are, since Bitcoin transactions are typically sent in unencrypted packets over the Internet and the source IP address can be pinpointed through various means. A common criticism of Bitcoin is that it moves too slowly when it comes to development.
Google Chairman Eric Schmidt: Bitcoin Architecture an Amazing Advancement
So, is Binance Coin actually worth anything Profiles: If you bitcoin account checker sent bitcoin pending after over 12 hours worried about disclosing information about your bitcoin wealth when you are sending is coinbase safe 2019 reddit send ripple to ledger nano s bitstamp map bitcoin transactions bitcoin eric to someone, you need to be aware of which inputs are used in your transactions more on this. The Team Careers About. To clarify what this means, the source of funds for a transaction is not an address, nor is it a transaction. Players can collect and unravel clues any way they want, even selling leads if they choose. The intention of the Human Rights Foundation is to examine these technologies and elucidate on their potential of bringing economic and political freedom to the individual. There is no perfect privacy solution for any activity on the Internet, and in many cases, privacy-conscious choices come with tradeoffs to both cost and ease-of-use where no one-size-fits-all solution exists. Getting Started: The Human Rights Foundation cares deeply about monero cryptocurrency wallet how many coin do we need in our cryptocurrency our civil liberties and privacy in our increasingly digital age, especially in places where people live under authoritarian governments. Blockchain analytics firms will scrape the web regularly to find such information. The current known best method to hide your source device and IP address when retrieving information about transactions or when transmitting transactions is to leverage Tor hidden services. The Lightning Network is accessible to users of Lightning wallets. The next step is to get acquainted with how different Bitcoin wallet applications can help with privacy, and what to expect when using. When you transact on the Bitcoin network you leave two types of traces. Transactions are not timestamped, but blocks are. Sign In. What does link your identity to your transactions are the things in the second category: Transactions contain inputs and outputs and are identified by transaction IDs seen at the top in the image. Load More. The same is true for most hardware wallets Ledger, Trezor in their out-of-the-box setups.
One of — if not the most — comprehensive resources for learning about Bitcoin with over 20 categories ranging from history, to buying BTC, setting up a wallet, technical information, mining, security, and trading Getting Bitcoins: The intention of the Human Rights Foundation is to examine these technologies and elucidate on their potential of bringing economic and political freedom to the individual. When we approach this subject, we recognize that we enter into a complex field, and as in any complex field, experts disagree. Whenever your node interacts with the network sending, receiving or routing other payments someone will learn about the existence of your node, its public key and its IP address. That limits how much new gold can be refined each year. CoinJoins are a scheme which adds many inputs from many different users into a joint transaction before the transaction is broadcast. I agree to the Terms of Service and Privacy Policy. Genesis Knowing the developers: One block explorer might choose to display the transaction like this:. Many blockchain analytics firms receive information about transactions directly from their own customers, such as cryptocurrency exchanges. The most recent block at the time of writing in the Bitcoin blockchain contains transactions. Close Menu Search Search. The Latest. If you are worried about disclosing information about your bitcoin wealth when you are sending a payment to someone, you need to be aware of which inputs are used in your transactions more on this below. The first clue, released yesterday, seems to point users in the direction of the Blockstream satellite, which broadcasts data related to bitcoin. Revealed exclusively to CoinDesk, the keys to this bitcoin wallet were divided into 1, fragments, requiring a minimum of key fragments to move the funds. However, two of the largest analytics firms, Chainalysis and Elliptic, have stated that they do not trace back transactions to specific individuals in the data they receive, but only to the exchanges or other business entities 1 , 2. The ambition of this initiative is to cut through the complexity of the cryptocurrency privacy subject by sourcing subject matter expertise from the industry. There is no single person, not even a member of the tropical island—based company which island is a secret , who knows how the game will play out.