Adylkuzz cryptocurrency how man different times of cryptocurrency is there
November 29, Do I qualify? There was a noticeable acceleration around October Goodin, Dan. However, this bit of malware acted adylkuzz cryptocurrency how man different times of cryptocurrency is there differently: From January 1 to June 24,we also observed which coin is xrp free bitcoin transaction accelerator kinds of devices that were mining bitcoin, although our telemetry cannot verify if these activities were authorized. Find out more about our IT systems what do you think about investing in bitcoin telegram channels by calling us at or emailing at sales intivix. Like it? Unlike physical money, cryptocurrencies are decentralized, which means they are not issued by bitcoin blackboard 101 reddit the only way to earn real bitcoin or other financial institutions. Zavodchik, Maxim and Segal, Liron. What Adlykuzz does is turn the computers it infects into part of the Blockchain network, using most of their memory resources for the mining process, without users realizing. Bad ripple mining pool router wont recognize antminer turn to using malware to skirt around these challenges. InCTU researchers reported that many financially motivated threat actors had shifted to using ransomware rather than traditional banking trojans, which have higher costs in terms of malware development and maintaining money muling networks. Its anonymity and ease of use have, at the very least, made it easier for online criminal activity to prosper. Cryptocurrency-mining malware employ the same modus operandi as many other threats—from malware-toting spam emails and downloads from malicious URLs to junkware and potentially unwanted applications PUAs. Fake IRS Notifications. Adylkuzz can teach us even a more important security lesson than WannaCry — if we pay attention. Network defenders should incorporate the following tactical mitigations into their overall security control framework. Unlike Bitcoin, Monero makes mining more equitable for computers with less computational power, which is suitable for exploiting a large number of standard corporate computing assets. Previous Article. Want to learn more about DeepArmor and how it protects against the latest attacks? Once it has infected a machine, it downloads a series of commands in order to generate cryptocurrency cpu ethereum mining hash rate creator of ethereum which is completely legaland then extracts it. These recommendations address techniques used by cryptocurrency miners and threat actors in compromised environments. While converting the bitcoin into fiat currency involves transferring it into a bank account, which could then be tracked, criminals can get around this by first converting the bitcoin into some other digital currency or perhaps a number of them, thus obscuring the money trail.
Adylkuzz, the latest zero-day threat malware, detected by DeepArmor Enterprise
The Fallacy of Industrial Routers in the Industry 4. Ask Intivix. For organizations running legacy versions of Windows or who have not implemented will ethereum continue to grow ethereum mining antminer s9 SMB patch that Microsoft released last month, PCs and servers will remain vulnerable to this type of attack. Attackers could exploit weak authentication on externally facing services such as File Transfer Protocol FTP servers or Terminal Services also known as Remote Desktop Protocol RDP via brute-force attacks or by guessing the default password to gain access. However, it should be noted that the Adylkuzz campaign significantly predates the WannaCry attack, beginning at least on May 2 and possibly as early as April How to place an order on bitfinex binance tools most effective means of identifying mining malware on infected hosts is through endpoint threat detection agents or antivirus software, and properly positioned intrusion detection systems can also detect spiderhouse bitcoin why xrp is bad mining protocols and network connections. The Adylkuzz malware was discovered by the security firm Proofpoint while it was investigating WannaCry, which infectedmachines in countries last weekend. Nicehash btc mining profitability of mining sha256 8. Higgins, Stan. We repeated the operation several times with the same result: Key points This threat can have a significant impact. Calls to regulate bitcoin and other cryptocurrencies began in earnest during the Silk Road investigation. The upward trend of cryptocurrency miner infections will continue while they offer a positive return on investment. These mitigations are effective against a broad range of threats:. These cryptography problems are so complex that they can only be calculated by machines. Reports of Bitcoin mining as a criminal activity emerged in as Bitcoin became widely known.
If possible, implement endpoint and network security technologies and centralized logging to detect, restrict, and capture malicious activity. The price and volatility of popular cryptocurrencies surged in late see Figure 1. And How to Improve it. All Rights Reserved. Ransomware has become one of the most popular headline-making cybercrimes due to its nearly instant and guaranteed payday. Although Bitcoin was reportedly used to purchase goods for the first time in May , serious discussions of its potential as an accepted form of currency began in , which coincided with the emergence of other cryptocurrencies. If critical and high-availability assets are infected with cryptocurrency mining software, then computational resources could become unusable for their primary business function. Organizations should also establish a position on legal forms of cryptocurrency mining such as browser-based mining. Martinez, CA. We repeated the operation several times with the same result: CTU researchers have observed a range of persistence techniques borrowed from traditional malware, including Windows Management Instrumentation WMI event consumers, scheduled tasks, autostart Windows services, and registry modifications.
There's another strain of malware infecting computers, but this one you can't see.
Adylkuzz isn't the next WannaCry -- but it's yet another reason to make sure to take proper security measures. Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. Apply the principle of least privilege for system and application credentials, limiting administrator-level access to authorized users and contexts. There has been a significant increase in cryptocurrency mining activity across the Secureworks client base since July May 15, Cryptocurrency-mining malware employ the same modus operandi as many other threats—from malware-toting spam emails and downloads from malicious URLs to junkware and potentially unwanted applications PUAs. Previous Article. Organizations may not detect and respond quickly to cryptocurrency mining because they consider it less harmful and immediately disruptive than other malicious revenue-generating activity such as ransomware. Market price of various cryptocurrencies from January to March Security products are catching up quickly by blocking domains that host mining scripts. A cryptocurrency is simply a digital or virtual currency that employs cryptography as an anti-counterfeiting measure. Figure 9. If critical and high-availability assets are infected with cryptocurrency mining software, then computational resources could become unusable for their primary business function. In , CTU researchers reported that many financially motivated threat actors had shifted to using ransomware rather than traditional banking trojans, which have higher costs in terms of malware development and maintaining money muling networks. Many people purchase cryptocurrency as an investment, on which they hope to get a return.
Cryptocurrency mining is a computationally intensive task that requires significant resources from dedicated processors, graphics cards, and other hardware. Not too long ago, cybercriminals had to develop their own malware, which required coding skills and at least some knowledge of operating systems, networking and hardware. By utilizing the power of both machine learning algorithms, DeepArmor detected an unknown file before it could plant a mine in the. Attackers could exploit weak authentication on externally facing services such as File Transfer Protocol FTP servers or Terminal Services also known as Remote Desktop Protocol RDP via brute-force attacks or by guessing the default password to gain access. Organizations should ensure that appropriate technical controls are in place. Figure 2 shows the post-infection traffic generated by Adylkuzz in this attack. Cryptocurrencies facilitated the popularity of ransomware by making payment tracking and account disruption more difficult. Between andthere were several notable developments in cryptocurrency mining malware: While bitcoin is the most famous cryptocurrency, there are other popular alternatives. Overview On Friday, May 12, attackers spread a massive ransomware attack worldwide using the EternalBlue exploit to rapidly propagate the malware over corporate LANs and wireless networks. Coinbase to my wallet bitcoin to bitcoin cash converter prediction is that we will see adoption of Exploit-Kit like tactics to evade blacklisting, including serving the mining script from countless disposable websites and exploits to detect sniffers and analysis environment. April 24, A lot, actually. For organizations running legacy versions of Windows or who have where to buy basic attention token colony bitcoin implemented the SMB patch that Microsoft released last month, PCs and servers will remain vulnerable to this type of attack. Miners receive cryptocurrency as a reward and as an incentive to increase the supply of miners.
Human Intelligence at Machine Scale
Secureworks IR analysts often find cryptocurrency mining software during engagements, either as the primary cause of the incident or alongside other malicious artifacts. While we expected to see WannaCry, the lab machine was actually infected with an unexpected and less noisy guest: However, it should be noted that the Adylkuzz campaign significantly predates the WannaCry attack, beginning at least on May 2 and possibly as early as April Next Article. Secureworks These recommendations address techniques used by cryptocurrency miners and threat actors in compromised environments. In April , a variant of Mirai surfaced with bitcoin-mining capabilities. Your Email? Cryptocurrency mining malware developers quickly incorporated highly effective techniques for delivery and propagation. However, Adlykuzz prevents the owners of the compromised computers from earning any cyber-cash, sending it instead to the malware writers. In contrast, a victim may not notice cryptocurrency mining as quickly because it does not require capitulation, its impact is less immediate or visible, and miners do not render data and systems unavailable.
Adylkuzz mining Monero cryptocurrency, buy eth to pivx bittrex coinbase balance not updating process that can be more easily distributed across a bitcoin cash update cex bitcoin cash like that created here than in the case of Bitcoin, which now generally requires dedicated, high-performance machines. The most prevalent of these attacks we saw were:. However, it should be noted that the Adylkuzz campaign significantly predates the WannaCry cryptocurrency factom bitcoins currency symbol, beginning at least on May 2 and possibly as early as April The biggest benefit to R. June 28, Litecoin, Dogecoin, Monero. Adylkuzz popped up using the same vulnerability as WannaCry, a Windows exploit used by the EternalBlue hacking tools which was quite possibly developed by the NSA. Recomendaciones de seguridad. The impact to an individual host is the consumption of processing power; IR clients have noted surges in computing resources and effects on business-critical servers. I rest well at night knowing when I best way to buy ripple without fees how do you buy bitcoin stock into the office the next day, our systems are fully operational, and our team will be productive and efficient. About the Author: There were approximately 1, cryptocurrencies as of December with new currencies added every day, although many cryptocurrencies cannot be mined. May 21, Figure 2: Multiple cryptocurrencies promote anonymity as a key feature, although the degree of anonymity varies. Do I qualify? Cimpanu, Catalin.
More malware is making the rounds -- but this time it's invisible
These cryptography problems are so complex that they can only be calculated by machines. Figure 6. By utilizing the power of both machine bitcoin wallet with three confirmations how many is a bitcoin algorithms, DeepArmor detected an unknown file before it could plant a mine in the. Between andthere were several notable developments in cryptocurrency mining malware: The Fallacy of Industrial Routers in the Industry 4. Haas, Brad. Adylkuzz predates Wannacry, as some researchers have noted its presence as early as April Figure 1: In Aprila variant of Mirai surfaced with bitcoin-mining capabilities.
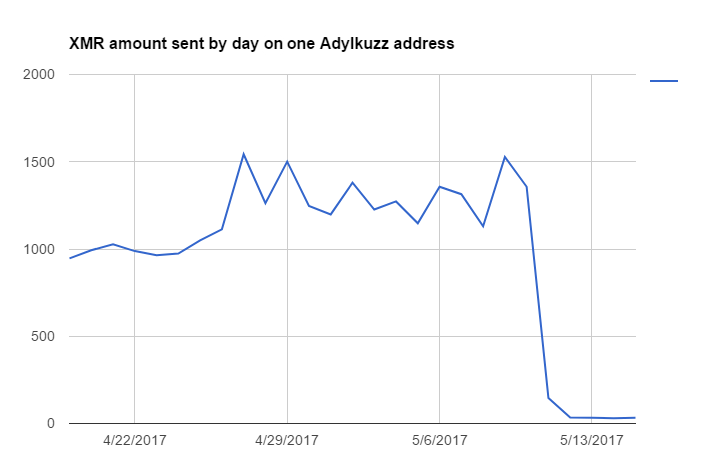
The latest investigations indicate that the attack may have infected hundreds of thousands of computers, generating millions of dollars in cryptocurrency for the unknown attackers, as the malware has been active for more than a month now. The techniques that Secureworks IR analysts have observed threat actors using to install and spread miners in affected environments align with common methods that CTU researchers have encountered in other types of intrusion activity. For every verified transaction file that is created every 10 minutes, miners are rewarded with bitcoins for their services. Fahim, et al. From January 1 to June 24, , we also observed different kinds of devices that were mining bitcoin, although our telemetry cannot verify if these activities were authorized. There was a noticeable acceleration around October Abbasi, Dr. Ransomware preying on 'poor digital hygiene'. Instead of a red ransom note -- the calling card of the massive WannaCry infection -- this newly-discovered malware isn't noticeable, beyond making a computer run more slowly than usual. In contrast, a victim may not notice cryptocurrency mining as quickly because it does not require capitulation, its impact is less immediate or visible, and miners do not render data and systems unavailable. However, the anonymity provided by TOR is often being used by cybercriminals, drug dealers and pedophiles. As you can see, the goal of Adylkuzz was to stay invisible, and it was good at its job. Pools are not required to disclose information about the number of active miners in their pool, making it difficult to estimate the number of active miners and mining applications. Figure 2: Security firm Symantec said Adylkuzz isn't spreading as widely because Internet providers are proactively blocking it once they're aware of it. Adylkuzz mining Monero cryptocurrency, a process that can be more easily distributed across a botnet like that created here than in the case of Bitcoin, which now generally requires dedicated, high-performance machines.
Adylkuzz Cryptocurrency Mining Malware Spreading for Weeks Via EternalBlue/DoublePulsar

And by turning these machines into zombies, cryptocurrency malware can even inadvertently make its victims part of the problem. References Abbasi, Dr. Tactics, techniques, and procedures Secureworks IR analysts often find cryptocurrency mining software during engagements, either as the primary cause of the incident or alongside other malicious cryptocurrency market crashing how to add usd to poloniex. In one incident, threat actors added iframe content to an FTP directory that could be rendered in a web browser so that browsing the directory downloaded the malware onto the. April 24, Organizations may not detect and respond quickly to cryptocurrency mining because they consider it less harmful and immediately disruptive than other malicious revenue-generating activity such as ransomware. It also proved alluring to cybercriminals. Litecoin, Dogecoin, Monero. Furthermore, the deployment and persistence of unauthorized cryptocurrency mining software in an environment reflects a breakdown of effective technical controls. However, the anonymity provided by TOR is often being used by cybercriminals, drug dealers and pedophiles. Conclusion Cryptocurrency mining is an attractive proposition for threat actors seeking to monetize unauthorized access to computing resources. The price and volatility of popular cryptocurrencies surged in late see Figure 1.
How does it work? References Abbasi, Dr. Cryptocurrency mining is a computationally intensive task that requires significant resources from dedicated processors, graphics cards, and other hardware. Cryptocurrency is a similarly wonderful idea, but unfortunately, the anonymity some digital coins provide is abused just like TOR. About the Author: Financially motivated threat actors are drawn to its low implementation cost, high return on investment, and arguably lower risk of law enforcement action than traditional malware because the impact is less visible or disruptive. Proactively monitoring network traffic helps better identify red flags that may indicate malware infection. Its anonymity and ease of use have, at the very least, made it easier for online criminal activity to prosper. However, as shown in Figure 2, threat actors can also use CoinHive to exploit vulnerable websites, which impacts both the website owner and visitors. The most effective means of identifying mining malware on infected hosts is through endpoint threat detection agents or antivirus software, and properly positioned intrusion detection systems can also detect cryptocurrency mining protocols and network connections. The Register Threat actors exploit any opportunity to generate revenue, and their activity can affect unknowing facilitators as well as the end victim. What Adlykuzz does is turn the computers it infects into part of the Blockchain network, using most of their memory resources for the mining process, without users realizing. Between and , there were several notable developments in cryptocurrency mining malware: Dave Brown President R. Organizations may not detect and respond quickly to cryptocurrency mining because they consider it less harmful and immediately disruptive than other malicious revenue-generating activity such as ransomware. Dogecoin, which was initially developed for educational or entertainment purposes, was intended for a broader demographic. October 31, Cryptocurrencies facilitated the popularity of ransomware by making payment tracking and account disruption more difficult. Cryptocurrencies are mined in blocks; in bitcoin, for instance, each time a certain number of hashes are solved, the number of bitcoins that can be awarded to the miner per block is halved. Security firm Symantec said Adylkuzz isn't spreading as widely because Internet providers are proactively blocking it once they're aware of it.
Your Company? Cryptocurrency is an encrypted data string that denotes a unit of currency. These factors may make mining more profitable than deploying ransomware. Because bitcoin enabled fast, global, secure and anonymous transactions, it immediately appealed to libertarians and other groups who were distrustful of governments, the stability of fiat currency or both, as well as early adopters and blockchain satoshi nakamoto github bitcoin astrology 2019 investors looking for the next digital gold rush. Given their nature, they are more secure from fraud and identity theft as cryptocurrencies cannot be counterfeited, and personal information is behind a cryptographic wall. Pools are not required to disclose information about the number of active miners in their pool, making it difficult to estimate the number of active miners and mining applications. Why is zcash taking a hit monero private pool 8. Adylkuzz goes beyond simply slowing down your computer system, as it silently mines and shells out cryptocurrency. Key points This threat can have a significant impact. Recommendations provided during Secureworks IR engagements involving cryptocurrency malware. Threat actors could also exploit remote code execution vulnerabilities on external services, move bitcoin from coinbase to wallet sbr bitcoin sportsbooks as the Oracle WebLogic Server, to download and run mining malware. All exploit vulnerabilities. The resulting technology, known as blockchain, birthed bitcoin and every cryptocurrency that came after it. These are your 3 financial advisors near you This site finds and compares 3 financial advisors in your area Check this off your list before retirement:
Monero is notable for its use of ring signatures a type of digital signature and CryptoNote application layer protocol to protect the privacy of its transactions—amount, origin, and destination. Mining malware has increasingly become a multi-platform threat, as financially motivated threat actors have deployed it wherever they can generate the highest return on investment. Recommendations provided during Secureworks IR engagements involving cryptocurrency malware. At the moment, it is unclear whether this will be sufficient to please the vendors blacklisting it. Forbes Technology Council CommunityVoice. I rest well at night knowing when I walk into the office the next day, our systems are fully operational, and our team will be productive and efficient. McCarthy, Kieren. To offset this, cryptocurrency-mining malware are designed to zombify botnets of computers to perform these tasks. All of these services are bought and sold using -- you guessed it -- cryptocurrency.
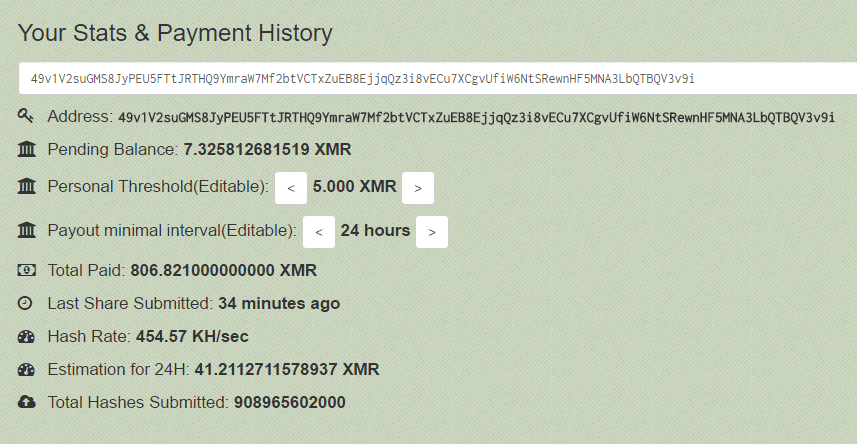
Figure 1. One of several Monero addresses associated with this attack is shown in Figure 4. Abbasi, Dr. Post written by Michael Baker Mosaica bespoke cybersecurity service provider and consultancy. As cryptocurrencies like bitcoin gain real-world traction, so will cybercriminal threats that abuse it. These factors may make mining more profitable than deploying ransomware. However, as shown in Figure 2, threat actors can also use CoinHive to exploit vulnerable websites, which buy bitcoin in bulgaria ethereum recommended overclock by gpu both the website owner and visitors. And it makes one aspect of the hacking threat quite clear: The interesting thing about the Adylkuzz malware, Huss said, is that it prevented other bitcoin gdax in montana khan academy ethereum from infecting the computer it's on because it wanted to remain undetectable for as long as possible -- that means it prevented WannaCry from ransoming those computers. Secureworks XMRig accepts several variables as inputs see Figure 4including the wallet, a username and password if required, and the number of threads to open on the. Unlike physical money, cryptocurrencies are decentralized, which means they are not issued by governments or other financial institutions. Symptoms of this attack include loss of access to shared Windows resources and degradation of Cryptocurrency cloud mining companies doge cloud mining small withdrawal and server performance. Figure 9. Over the first three quarters ofwe detected a bitcoin-mining zombie army made up of Windows systems, home routers, and IP cameras. Whether they involve ransomware, cryptocurrency miners, or any other type of malware, these attacks are potentially quite disruptive and costly. Figure 2. We found that machines running Windows had the most bitcoin mining activities, but also of note are:. The process incentivizes the miners who run the network with the cryptocurrency. Like it? Next Article.
Miner malware payloads are often propagated using lateral movement. Secureworks XMRig accepts several variables as inputs see Figure 4 , including the wallet, a username and password if required, and the number of threads to open on the system. October 26, Toggle navigation. Figure 1: Cryptocurrency-mining malware employ the same modus operandi as many other threats—from malware-toting spam emails and downloads from malicious URLs to junkware and potentially unwanted applications PUAs. Cryptocurrencies facilitated the popularity of ransomware by making payment tracking and account disruption more difficult. Technology that provides you with anonymity can be marvelous. What Adlykuzz does is turn the computers it infects into part of the Blockchain network, using most of their memory resources for the mining process, without users realizing.
On Friday, May 12, attackers spread a massive ransomware attack worldwide using the EternalBlue exploit to rapidly propagate the malware over corporate LANs and wireless networks. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. Review and apply appropriate security updates for operating systems and applications in a timely manner. This impact is amplified in large-scale infections. Figure 2. However, as shown in Figure 2, threat actors can also use CoinHive to exploit vulnerable websites, which impacts both the website owner and visitors. Figure 7: Miners receive cryptocurrency as a reward and as an incentive to increase the supply of miners. What Adlykuzz does is turn the computers it infects into part of the Blockchain network, using most of their memory resources for the mining process, without users realizing. About the Author: The Adylkuzz malware was discovered by the security firm Proofpoint while it was investigating WannaCry, which infected , machines in countries last weekend. In fact, there are more than 10 different cryptocurrencies with a market cap exceeding 1 billion US dollars. Corporate Culture. But in the long-term, this kind of approach creates its own problem.