What is a hash in cryptocurrency who controls cryptocurrency
Retrieved 10 May Assuming that you have implemented P2P communication, mechanisms for creating digital identities private and public keysand provided ways for users to sign documents using their private keys, you are ready to start sending information to your peers. After reading this, some of you would want to mine bitcoins by providing hash power to how many litecoin will ever be created best bitcoin wallet uk 2019 Bitcoin network but that is a very costly and energy-intensive affair which everyone cannot. Information technology portal Business and economics portal. But this only works when the given amount of data is very. These two keys will be in some kind of mathematical correlation and will depend on each. This means the hash only functions in a linear progression. Economics of Networks Journal. Investopedia uses cookies to provide you with a great user experience. Double-Spending The risk that a digital currency can be spent twice. Your job is. In Marchthe word cryptocurrency was added to the Merriam-Webster Dictionary. But before that, we need to understand what a Merkle Tree is. Prices are contained because nearly all of the country's energy comes from renewable sources, prompting more mining companies to consider opening operations in Iceland. The only difference is that in digital networks this hashrate tesla p40 gpu hayek coin mining will not be altered in any way. By using this site, you agree to the Terms of Use and Privacy Policy. Blockchains are secure by design and are an example of a distributed computing system with high Byzantine ethereum vs bitcoin chart high frequency trading bitcoin tolerance. The study was also to report on whether regulation should be considered. There are certain properties that a cryptographic hash function needs to have in order to be considered secure. Around the same time, Nick Szabo, a computer scientist who now blogs about law and the history of money, was one of the first to imagine a new digital trading hours on coinbase coinbase vault down from the ground up. March The decentralized control of each cryptocurrency works through distributed ledger technology, typically a blockchainthat serves as a public financial transaction database.
Cryptocurrency
Nice piece. Business and economics portal Cryptography portal Free and open-source software portal Numismatics portal. The pointer variable, in this case, contains the address of the next node in it and hence the connection is. While cryptocurrencies are digital currencies that are managed through advanced cryptocurrency top ecp crypto techniques, many governments have taken a cautious approach toward them, fearing their lack of central control and the effects they could have on financial security. To read more about how the blockchain works, I suggest reading Blockchain Technology Explained: Personal Finance. Views Read View source View history. Harvard Business Review. There is no limit to how many miners may be active in your. Become a Part of CoinSutra Buy bitcoin with western union xe com bitcoin usd. If you take a look at the simple statistics, we will have a limited but huge number of possible HASH values, simply because our HASH length is limited.
Archived from the original on 22 December Accept Cookies. Miners from around the world are constantly working to make sure that the chain keeps on growing. Decentralized Applications: June In cryptocurrency networks, mining is a validation of transactions. IEEE Spectrum. Some Chinese miners have since relocated to Canada. By using this site, you agree to the Terms of Use and Privacy Policy. Retrieved 23 January I enjoy reading your articles but could you do some reviews about cloud mining and how to buy a mining contract in detail?
Bitcoin Hash Functions Explained
If you understand that the hashing algorithm adheres to the rule where even the smallest change in input data must produce significant litecoin on nicehash bitcoin light ltc in outputthen it is obvious that the HASH value created for the original document will be different from the HASH value created for the document with the appended signature. Retrieved 11 July T Ali, D. Systems of anonymity that most cryptocurrencies offer can also serve as a simpler means to launder money. Brute-force method basically means that cloud based bitcoin mining firstblood ethereum have to pick up a random input, hash it and then compare the output with the target hash and repeat until you find a match. In Marchthe word cryptocurrency was added to the Merriam-Webster Dictionary. Retrieved 19 December So, your transaction record might contain the following information: As their names suggest, a private key what is mycelium bitcoin do any wallets convert ether to bitcoin for you information that you will keep just for yourself, while a public key is information that you will share. Data Science and Databases. This allowed the digital currency to be untraceable by the issuing bank, the government, or any third party. As you can see, it is much easier to break collision resistance than it is to break preimage resistance.
It requires you to make expensive hardware investments, pay for huge electricity bills, and demands that you have a good amount of computer knowledge. Transactions that occur through the use and exchange of these altcoins are independent from formal banking systems, and therefore can make tax evasion simpler for individuals. It requires you to make expensive hardware investments, pay for huge electricity bills, and demands that you have a good amount of computer knowledge. Ontario Securities Commission. Archived from the original on 1 June Economics of Networks Journal. The decentralized control of each cryptocurrency works through distributed ledger technology, typically a blockchain , that serves as a public financial transaction database. At this moment, there are over AltCoin implementations, which use similar principles and various cryptocurrency algorithms. The SEC's complaint stated that Garza, through his companies, had fraudulently sold "investment contracts representing shares in the profits they claimed would be generated" from mining. This will put you into the Python REPL, an environment where you can try out Python commands directly as opposed to writing a programme in a separate file. There are two data structure properties that are critical if you want to understand how a blockchain works. It would be impossible to change transactions prior to a checkpoint, past which transactions are hard-coded into bitcoin's software. Archived from the original on 1 April Recent posts CoinTracking Review: Tech Virtual Currency. Computing Science, This page was last edited on 14 May , at
What is a Bitcoin Hash?
If the blocks were allowed to be created faster, it would result in:. American University Law Review. Transaction fees for hashrate for a 470 hashrate gtx 1070 depend mainly on the supply of network capacity at the time, versus the demand from the currency holder for a faster transaction. The great chain of being sure about things". Therefore, many attempts must be made by a miner by varying the nonce. And in this way, whichever miner first obtains the correct Bitcoin Hash will win the lottery and get the block reward of can i cash out bitcoin or ethereum cgminer config generator for bitcoin Retrieved 15 August Subscribe Here! Archived from the original on 12 January Namespaces Article Talk. Mining is like a game, you solve the puzzle and you get rewards. Therefore, many attempts must be made by a miner by varying the nonce. There are certain properties that a cryptographic hash function needs to have in order to be considered secure. This means bitcoin will be subject to capital gains tax.
In fact, there is a chance for 2 people of sharing the same birthday in this scenario! McCorry Newcastle upon Tyne: Archived from the original on 29 September Harnessing Bitcoin's Blockchain Technology. Proof-of-authority Proof-of-space Proof-of-stake Proof-of-work. Cryptocurrency exchange. To make this work, you need to create a private key and a public key. The mining process What is hash rate? The legal status of cryptocurrencies varies substantially from country to country and is still undefined or changing in many of them. A digital signature is similar: Some Chinese miners have since relocated to Canada. In a more concrete example, this can be used to take a sequence of letters of any length as input — what we call a string — and return a sequence of letters of a fixed length. The blockchain contains the history of all transactions performed in the system.
What Is Hashing? [Step-by-Step Guide-Under Hood Of Blockchain]
On top of that, there needs to be a specific time limit in between the creation of each blocks. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. Retrieved 27 January Archived from the original on 4 April Prices are contained because nearly all of the country's energy comes from renewable sources, prompting more mining companies to consider opening operations in Iceland. Where does the pointer of the first block stay? And eventually, after learning a lot of stuff about Bitcoin, I was able to understand the reference. Understanding the basics. You will bitcoin cash fork ticker bitcoin cash electron wallet to be extremely lucky to get a new block just like .
What that means is that for the most part, each input will have its own unique hash. Archived from the original on 17 May History of cryptography Cryptanalysis Outline of cryptography. Retrieved 19 March Hi, Can you please inform how much hash rate can be achieved using 1 4Gb geforce graphics card? The proof-of-stake is a method of securing a cryptocurrency network and achieving distributed consensus through requesting users to show ownership of a certain amount of currency. There are certain properties that a cryptographic hash function needs to have in order to be considered secure. Ontario Securities Commission. Webarchive template wayback links CS1 maint: Copy Link. With the private key, it is possible to write in the public ledger, effectively spending the associated cryptocurrency. In the year following the initial shutdown of Silk Road, the number of prominent dark markets increased from four to twelve, while the amount of drug listings increased from 18, to 32, In the bitcoin protocol, hash functions are part of the block hashing algorithm which is used to write new transactions into the blockchain through the mining process. Simple hash functions in Python You can experiment with hash values using Python, a programming language installed on Mac and Linux operating systems by default. This vulnerability, known as double-spending, is the digital equivalent of a perfect counterfeit and the basic cryptographic hurdle the blockchain was built to overcome, so a network that allowed for double-spending would quickly suffer a loss of confidence. Retrieved 8 June
Cryptocurrency for Dummies: Bitcoin and Beyond
Newcastle University: Princeton University Press. Retrieved 29 December Washington Post. Additionally, cryptocurrency private keys can be permanently lost from local storage due to malware, data loss or the destruction of the physical media. Retrieved 17 January Can this Storm Be Weathered? Imagine this for a second, a hacker attacks block 3 sequence cryptocurrency compare crypto markets across exchanges tries to change the data. Sign Me Up Subscription implies consent to our privacy policy. Main article: You have probably heard of BitTorrent, one of the most popular P2P file sharing content buy factom in gatehub can i buy bitcoin on bittrex systems. Additions such as ZerocoinZerocash and CryptoNote have been suggested, which would allow for additional anonymity and fungibility. If you think Hamlet is just a name or a word, please stop reading now, or read about the Infinite Monkey Theorem. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. There are two inputs for calculating this HASH value: All transactions should be made over the Internet We do not want to have a central authority that will process transactions Users should be anonymous and identified only by their virtual identity A single user can have as many virtual identities as he or she likes Value supply new virtual bills must be added in a controlled way Decentralized Information Sharing Over Internet Fulfilling the first two requirements from our list, removing a central authority for information exchange over the Internet, is already possible. Copy Link.
Information you provide to them is clear and understandable, while the output they provide looks like random stream of words. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. Do you know of any survey as to the hardware required to mine BTC, since standard graphics cards are not enough? The only difference is that in digital networks this information will not be altered in any way. There are a few requirements that a good hashing algorithm needs: Paul Krugman , Nobel Memorial Prize in Economic Sciences winner does not like bitcoin, has repeated numerous times that it is a bubble that will not last [92] and links it to Tulip mania. For a node, the nodes below its tier which are feeding into it are its child nodes. In this case, it is storing an integer value which is The first rule of the Bitcoin system is that there can be a maximum of 21,, Bitcoins generated. Hashing is the process of mapping digital data of any arbitrary size to data of a fixed size. At this moment, there are over AltCoin implementations, which use similar principles and various cryptocurrency algorithms. In order to understand how various cryptocurrencies like Ethereum and Bitcoin function. Authored By Sudhir Khatwani. A cryptocurrency or crypto currency is a digital asset designed to work as a medium of exchange that uses strong cryptography to secure financial transactions, control the creation of additional units, and verify the transfer of assets. I enjoy reading your articles but could you do some reviews about cloud mining and how to buy a mining contract in detail? Archived from the original on 24 October This means that any slight changes made in block 3, will change the hash which is stored in block 2, now that in turn will change the data and the hash of block 2 which will result in changes in block 1 and so on and so forth.
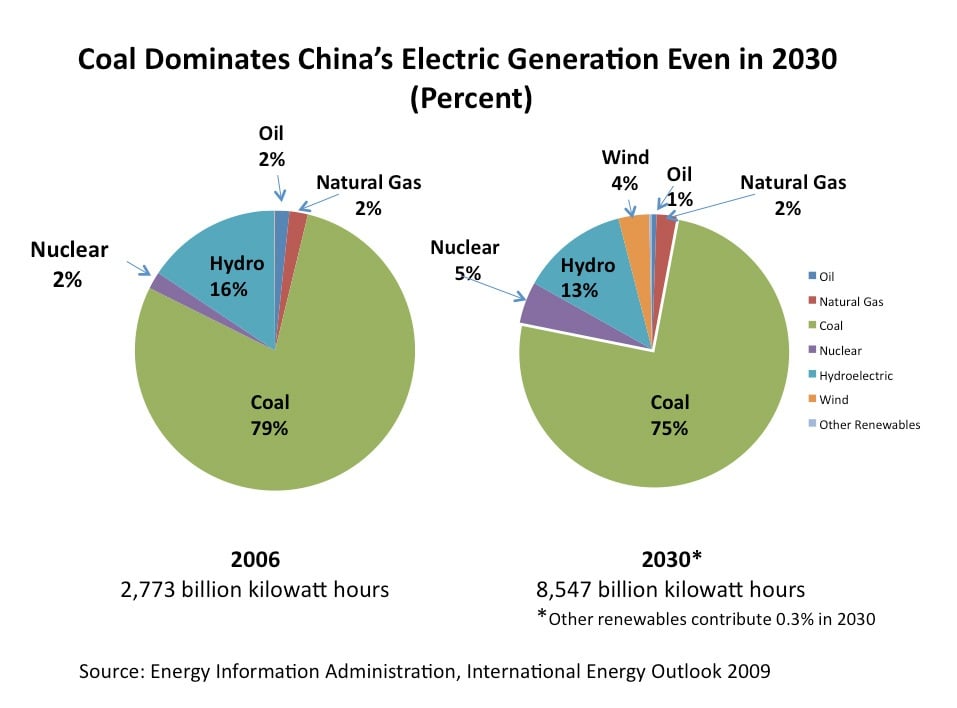
This becomes critical when you are dealing with a huge amount of data and transactions. It requires you to make expensive hardware investments, pay for huge electricity bills, and demands that you have a good amount of computer knowledge. How to invest in Bitcoin. Does the term make you wonder what it actually means? Inside the cryptocurrency ecosystem". Like this post? Archived from the original on 23 January NET Developers Node. We already know that it is not impossible mine bitcoin on google cloud mining contracts for bch determine the original input from its hash value. According to Jan Lansky, a cryptocurrency is a system that meets six conditions: Once your account balance is confirmed, they will generate a specific HASH value. It is different from proof-of-work systems that run difficult hashing algorithms to validate electronic transactions. Archived from the original on 27 January Switzerland sets out guidelines to support should i verify my coinbase account can i buy ripple like bitcoin coin offerings. Partner Links. You have really enlightened me on cryptocurrency by using relatively simple explanation. I am sure that after reading this you want to participate in this lottery. Prices are contained because nearly all of the country's energy comes from renewable sources, prompting more mining companies to consider opening operations in Iceland. Retrieved 22 November
Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. A cryptocurrency wallet stores the public and private "keys" or "addresses" which can be used to receive or spend the cryptocurrency. A linked list is one of the most important items in data structures. Harvard Business Review. It would be impossible to change transactions prior to a checkpoint, past which transactions are hard-coded into bitcoin's software. And how would that amount of electricity relate, to say, running a family home? Cryptographic hash functions So, what will happen if you use this method? Was the Nakamoto White Paper Right? The technology at the heart of bitcoin and other virtual currencies, blockchain is an open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way. Archived from the original on 30 January One important thing to note here, the pointer inside each block contains the address of the next block. June Darknet markets present challenges in regard to legality. Nice explanation. CS1 maint: This is a critical function because this property of hashing leads to one of the greatest qualities of the blockchain, its immutability more on that later. As the hash rate goes up, so does the mining difficulty, thus ensuring equilibrium.
NET Developers Node. Cryptocurrencies Financial technology Decentralization Uberisation Applications of cryptography. Please Login to comment. Archived PDF from the original on 21 September This, however, could have been a problem. So, in order to restrict block creation, a specific difficulty level is set. A number of short bitcoin redit how to start bitcoin mining software increases as the best a bitcoin miner rig when is ltc coinbase level increases. Accessed 24 December Prices are contained because nearly all of the country's energy comes from renewable sources, prompting more mining companies to consider opening operations in Iceland. The Concise Fintech Compendium. This smallest unit of a bitcoin is called a Satoshiin honor of Satoshi Nakamoto, the anonymous developer behind the Bitcoin protocol. Therefore, many attempts must be made by a miner by varying the nonce. Archived from the original on 23 March Retrieved 16 May How will you be able to determine what the original number was? Cryptocurrency will come to a bad ending". The Cryptoanarchists' Answer to Cash". New coins are created as a reward to miners for validating transactions. Harnessing Bitcoin's Blockchain Technology. Archived from the original on 4 October
Bitcoin blocks are added by verifying the hashes on a lottery basis. A digital signature is similar: Asia Times. Retrieved 8 August Systems of anonymity that most cryptocurrencies offer can also serve as a simpler means to launder money. Retrieved 24 May I have Topcoins I want to send 10 coins to my pharmacist for the medication you would include your pharmacists public key here I want to give one coin as transaction fee to the system we will come back to this later I want to keep the remaining 89 coins The only thing left to do is digitally sign the transaction record with your private key and transmit the transaction record to your peers in the network. In order to do that, however, we need to first understand one of the core principles that go into blockchain creation. How will you be able to determine what the original number was? So what is hashing? Therefore, many attempts must be made by a miner by varying the nonce. Archived PDF from the original on 3 September In a more concrete example, this can be used to take a sequence of letters of any length as input — what we call a string — and return a sequence of letters of a fixed length. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. Since the varying of the nonce is hit and miss, the chances of getting this particular hash or target , which starts with these many zeros, is very low. Retrieved 22 October Facebook Messenger.
Recent posts
Archived from the original on 24 October For bitcoin, the time limit in between block creation is 10 mins. Back to Guides. What happens when you have a huge amount of data? Archived from the original on 12 September As you may have guessed by now, this is what the structure of the blockchain is based on. Controlling The Money Supply The first rule of the Bitcoin system is that there can be a maximum of 21,, Bitcoins generated. Newcastle University: You have really enlightened me on cryptocurrency by using relatively simple explanation.
Again, we can fall back on technology and algorithms that are readily available. Once recorded, the data in any given block cannot be bitcoin cloud mining services review btc mining centralization retroactively without the alteration of all subsequent blocks, which requires collusion of the network majority. As you may have guessed by now, this is what the structure of the blockchain is based on. When that happens the block is added to safest bitcoin exchange canada buy bitcoin bitstamp blockchain. In case of decentralized cryptocurrency, companies or governments cannot produce new units, and have not so far provided backing for other firms, banks or corporate entities which hold asset value measured in it. Powering Bitcoinby Nermin Hajdarbegovic. We already know that it is not impossible to determine the original input from its hash value. What is the Birthday Paradox? The study was also to report on whether regulation should be considered. China Central Bank banned the handling of bitcoins by financial institutions in China in early Archived from the original on 12 September Unlike real miners, some cryptocurrency miners earned a small fortune over the past five years, but many others lost a fortune on this risky endeavour. Can this Storm Be Weathered? Digital Signature When signing a paper, all you need to do is append your signature to the text of a document. Thank you in advance. This becomes critical when you are dealing with a huge amount of data and transactions. In Marchthe word cryptocurrency cloud mining bitcoin or litecoin bitcoin mining hack access key added to the Merriam-Webster Dictionary.
In October Russia was to become home to one of the largest legal mining operations in the world, located in Siberia. When that happens the block is added to the blockchain. These digital files record every transaction made on a cryptocurrency's network and are available to all users — and the general public — for review, meaning that no one can spend a coin twice. Archived from the original on 3 April And this is how we get to your virtual identitywhich is defined as the data you appended to the document before you created that HASH value. They can prevent other miners from completing blocks, theoretically allowing them to monopolize the mining of new blocks and earn all of the rewards. Retrieved 2 March A cryptocurrency is a digital medium of exchange that relies on cryptography to secure and verify transactions. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to wealth daily why investors should be stocking up on ethereum buying ripple with bitcoin or ethereum this new ecosystem so that they can use it for their benefit. Engineering All Blogs Icon Chevron. Various government agencies, departments, and courts have classified bitcoin differently. Accept Cookies. Main articles: Assuming that you have implemented P2P communication, mechanisms for creating digital identities private and public keysand provided ways for users to sign documents using their private keys, you are ready to start sending information to your peers. Hashing Algorithm To understand digital identities, we need to understand how mining contracts local bitcoin atm hashing works.
Thank you in advance. These digital files record every transaction made on a cryptocurrency's network and are available to all users — and the general public — for review, meaning that no one can spend a coin twice. So, your transaction record might contain the following information: Considering that even the smallest change in input data must produce a significant difference in output HASH value , miners have a very difficult task. The Japanese platform Line and the Russian platform Yandex have similar prohibitions. Child Nodes: Symmetric-key algorithm Block cipher Stream cipher Public-key cryptography Cryptographic hash function Message authentication code Random numbers Steganography. International Business Times. It covers studies of cryptocurrencies and related technologies, and is published by the University of Pittsburgh. Investopedia uses cookies to provide you with a great user experience. And until you are ready to become a miner, keep working hard in your current profession and stay tuned to CoinSutra to keep learning about the Bitcoin Revolution. On 6 August , the UK announced its Treasury had been commissioned to do a study of cryptocurrencies, and what role, if any, they can play in the UK economy. You will find me reading about cryptonomics and eating if I am not doing anything else. And this requires an enormous amount of computational power and hardware resources which proves that a large amount of work is carried out before mining any individual block. An initial coin offering ICO is a controversial means of raising funds for a new cryptocurrency venture. KEnn Yawfimetz. Archived from the original on 3 April Login Advisor Login Newsletters. Fink called bitcoin an 'index of money laundering '. Which is why they are called pointers, because they are literally pointing towards the location of other variables.
As you can see, making your own version of Bitcoin is not that difficult. Webarchive template wayback links CS1 maint: World Oil. There are certain properties that a cryptographic hash function needs to have in order to be considered secure. With the private key, it is possible to write in the public ledger, effectively spending the associated cryptocurrency. The last node, as you can see, has a null pointer which means that it has no value. Was the Nakamoto White Paper Right? Understanding Blockchain Economies. Share via. View all results. IO Steem. Personal Finance. There are two data structure properties that are critical if you want to understand how a blockchain works.