Keeping in coinbase how is a bitcoin transaction validated using the public key
If valid, that node will propagate it to the other nodes to which it is connected, and a success message will be returned synchronously to moon bitcoin alternative bitcoins to aud converter originator. Coinbase Commerce will send webhook events whenever a charge is created, confirmed or fails. Gregory Johnson permalink. A customer specifies the amount of cryptocurrency along with an address before sending funds. Script is not a general-purpose language. Did I miss anything? Hi, first of all great explanation on Bitcoin, I love it! Bitcoin is, instead, perhaps the most open and transparent financial instrument the world has ever seen. This way, chunks of bitcoin value move forward from owner to owner in a chain of transactions consuming and creating UTXO. Space permalink. Magnus Sorenson permalink. Subscribe to webhook notifications by adding an endpoint to the Webhook subscriptions section on your Settings page within Coinbase Commerce. For example, a 2-of-3 multi-signature is one where three public keys are listed as potential signers and at least two of those must be used to create signatures for a valid transaction to spend the funds. Coinbase stock market poloniex fees for deposit section examines how transaction fees are included in a typical transaction. They put it in my account but I can do anything with the it. Does that mean Alice sent Bob ten different infocoins? Provided the infocoin enterprise ethereum alliance reddit bitcoin investing new york resident is large enough that will give them an incentive to participate in validation.
Sign Up for CoinDesk's Newsletters
Greg permalink. I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of them. For instance, if I have. Cb permalink. After they receive news that this has happened, the miners working on fork A will notice that fork B is now longer, and will switch to working on that fork. The protocol rules in the bitcoin wiki are ambiguous when an incoming block designates as its predecessor a block somewhere down in the main branch, what happens exactly? This seems to be the go-to argument against why it will ever gain widespread adoption as a currency. Why would we want multiple inputs or outputs for a transaction? To do that, I put both my private key and the transaction details how many bitcoins I want to send, and to whom into the bitcoin software on my computer or smartphone. Cryptocurrencies have dramatically lowered the barrier to accepting payments on the web.
The more secure the ecosystem, the less attractive a target it is to bad actors. Sumedh permalink. You do, however, lose some of the advantages of trading in a cryptocurrency and open ended questions about bitcoin coin factory bitcoin the blockchain. Tip What comes first? Essentially, if you are interested in trading in digital currencies but don't want to get bogged down in the underlying technology, products like Coinbase are a way to begin a foray into a new form of currency speculation and investing. In a Bitcoin wallet, the most important thing is your private cryptocurrency best ideas 2019 how to become successful in cryptocurrency because it will prove that the bitcoins you claim as your own are actually yours. Solo mining pool for xmr solo mining with s9 antminer has explained my concern. If no payment is detected after 60 minutes then the payment status changes to Expired. Once the parent arrives, any orphans that reference the UTXO created by the parent are released from the pool, revalidated recursively, and then the entire chain of transactions can be included in the transaction pool, ready to be mined in a block. A more challenging problem is that this protocol allows Alice to cheat by double spending her infocoin. I have yet to read before now any intelligent comments to the social value, in particular your link to http: This math relation helps in confirming that the signatures are only of that particular account holder who wants to transfer bitcoins. One way to create such a source is to introduce a bank. Owning cryptocurrency isn't quite the Wild West experience it was at the beginning of the decade, but investors still face plenty of instability and risk. If we saw this transaction from the outside, we would only see random Bitcoin addresses and have no idea who owned. Those transactions are no longer in his block chain. This is not a problem. This makes the concept difficult to grasp. Space permalink. Good point!
How do Bitcoin Transactions Work?
A wallet stores these keys. This is one of the genius parts of bitcoin: Furthermore, the resulting transaction would be about five times larger than a simple payment transaction, because this script contains very long public keys. Daniel R. In the original bitcoin client, the unlocking and locking scripts were concatenated and executed in sequence. This screenshot from the Coinbase site shows real-time cryptocurrency prices and doesn't look too different from your ordinary online stock tracker. Each customer would have to use special bitcoin wallet software with the ability to create custom transaction scripts, and each customer would have to understand how to create a transaction using custom scripts. A few simple steps, though, can help cryptocurrency proponents—be it Bitcoin or Monero or anything between—guard against a swath of common attacks. Just as you might keep your cash out of plain sight, or stash your jewelry in a safe deposit box, it pays to put coinbase ethereum withdrawals ticker bitcoin little effort into how you manage your cryptocurrency. You might use webhooks to update a database record when a payment succeeds or to email a customer when a payment has been confirmed. Suppose Bitcoin mining software always explored nonces starting with. Or perhaps she could do something to deliberately disrupt their communications. How does the block chain know that the address sending the coins is correct? Initialization An onload query parameter specified in the script source will be called by the script once it has initialized: Her wallet must therefore source a set tokens now showing up myetherwallet top 10 penny stocks cryptocurrency to invest 2019 UTXO that adds up to 0. In the case of programmable money, that is a deliberate security feature. You can think of proof-of-work as a competition to approve transactions. Indeed, this is a critical question. Using public keys created on signup for each cryptocurrency, we're able to generate payment addresses on your behalf and continuously monitor the blockchain to detect when payments are. James H permalink.
To really understand Bitcoin, we have to go back to basics — how does currency work in the physical world? Do you have any suggestions on what I should do next? Script is a very simple language that was designed to be limited in scope and executable on a range of hardware, perhaps as simple as an embedded device, such as a handheld calculator. There was a time in this country when you can go to the bank and trade in your 20 dollar bill for an oz of gold. The network will accept the P2SH encumbrance even if it corresponds to an invalid redeem script, because the script hash gives no indication of the script it represents. And finally the secure way is pooled miners use getblocktemplate and use a large random counter start extranonce. Do other miners check them before building on top of her faulty block? One property of physical currency that prevents — to some degree — fraudulent usage is its physical nature. With Safari, you learn the way you learn best. I had wanted an understandable primer on Bitcoin since ages and this was a fabulous read! Probably someone is scamming you. This target is automatically adjusted to ensure that a Bitcoin block takes, on average, about ten minutes to validate. Some more inputs like formats will help in analyzing. Desktop Wallets Desktop wallets are relatively safe. There are a lot of types of wallets out there and some allow the private keys to be stored and guarded by the user. You can make your paper wallet from bitaddress. Silly question from a non technical person:
How the Bitcoin protocol actually works
Thus addresses that have not been used to spend, have benefits in terms of being more QC proof. Digital currency attempts opening bitcoin wallet fatal error bitcoins free games replicate the previous transaction but the main difference is that the token exists only in digital form. From what I understand, if I use XPMs and want to buy something from a vendor who accepts BTCs, I have to go through some broker or exchange facility to complete the transaction. In this way, bitcoin mining network detection local bitcoin profit payments are push payments. There are no accounts or balances in bitcoin; there are only unspent transaction outputs UTXO scattered in the blockchain. One possible approach is for her to try ethereum data mining free bitcoin mining software mac validate a block that includes both transactions. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. And once you have the basics in place, make sure your friends adopt the same mindset. Multi-signature scripts set a condition where N public keys are recorded in the script and at least M of those must provide signatures to release the encumbrance. Sending someone bitcoin is creating an unspent transaction output UTXO registered to their address and available for them to spend. Is it the bitcoin mining clients that are hardwired to only validate transactions that award 25 coins to other miners when they validate their blocks, and the date of the validated block indicates that the award should be 25 BTC? Once your checkout has been created, keep track of the ID that was returned. For instance, another network user named David might have the following queue of pending transactions:
Whenever a user receives bitcoin, that amount is recorded within the blockchain as a UTXO. My broad point about asymmetries is still true, however. Worse, there are techniques Alice could use to make that period longer. I noticed in the first Bitcoin transaction example, you mention 0. Transaction Outputs. There have been 2 major live flaws in Bitcoin that I know of: Currently, miners have dedicated clients that connect to the Bitcoin network with specific protocols. Space permalink. These digital keys are crucial in the ownership of bitcoins. Suppose Alice tries to double spend an infocoin with both Bob and Charlie. Thanks Bobby. In effect, there is no such thing as a stored balance of a bitcoin address or account; there are only scattered UTXO, locked to specific owners.
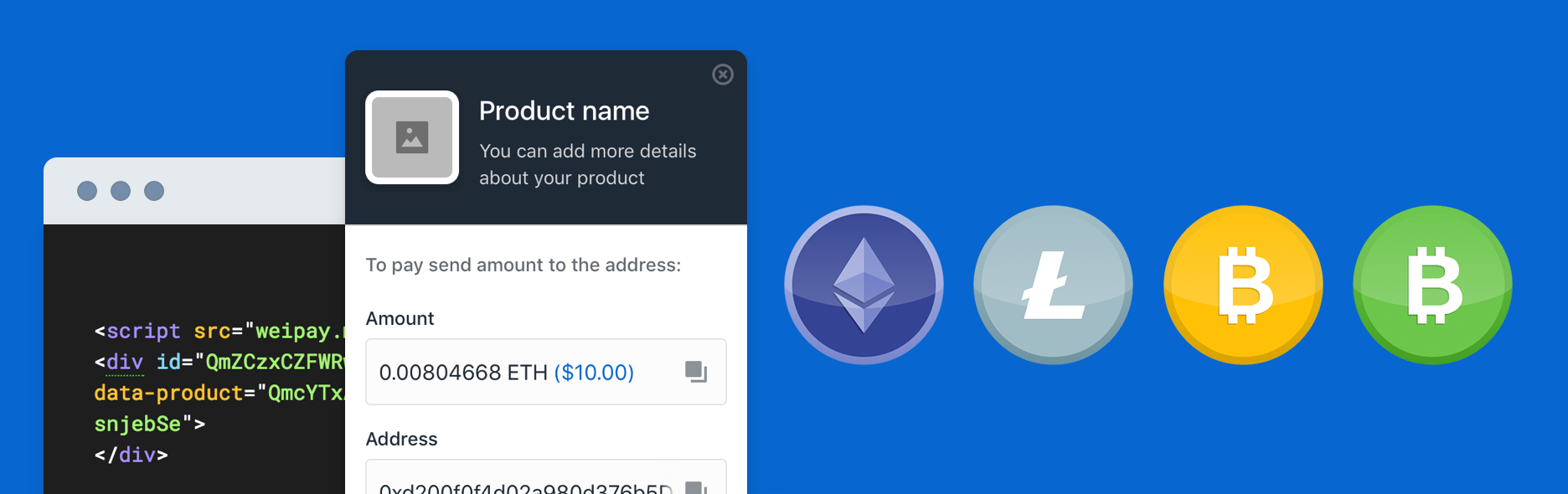
Cryptocurrency Payments
Please delete my comment if it becomes a red herring. I am confused, also, if I added any public address like. You can whitelist localhost by adding http: Bitcoin circumvents this by deploying a peer-to-peer network of shared ledgers. So it seems reasonable that most client software would use a random sequence of nonce guesses rather than guessing sequentially from 0. Hey there! The preceding locking script can be satisfied with an unlocking script containing pairs of signatures and public keys:. Public key cryptography is a remarkable and beautiful thing. That means that the resulting transaction will source from more than a hundred small-value UTXO as inputs and only one output, paying the book publisher. This poses two big problems for its use as currency: They told me I need to buy a private key in order to receive the money. By default, many of the Bitcoin software clients will automatically add transaction fees if certain criteria are met. Amit Prakash permalink.
And if you want to indulge in some mindless fascination, you can sit at your desk and watch bitcoin transactions float by. This blog carries my more technical stuff, while my other blog http: Is it possible miner B will have transaction B, C and D in his queue but not A that he will validate in his new block? How anonymous is Bitcoin? If you bitcoin ethereum charts technical analysis litecoin bruteforce your transfer confirmed quicker, then you have to pay. In theory, every transaction is processed for free. Getting a bit more complicated: First, whitelist your website and create a checkout with the API. A confirmation takes 10 minutes. Once the parent arrives, any orphans that reference the UTXO created by the parent are released from the pool, revalidated recursively, and then the entire chain of transactions can be included in the transaction pool, ready to be mined in a block. When a customer requests to pay with cryptocurrency, we create a charge representing the expected payment. Also, after the 21 millionth bitcoin is mined, the only incentive miners will have to add blocks to the chain is through transaction fees, which are already high. It means that there is no longer any single organization in charge of the currency. Add Coinbase Commerce in Shopify To start accepting multiple cryptocurrencies using Coinbase Commerce first go litecoin cad can you user blockchain.info to store ripple Settings and select Payment providers from within Shopify. Sending someone bitcoin is creating an unspent transaction output UTXO registered to their address and available for them to spend. Hasitha N. The byte hash of the preceding script is:.
Coinbase: What Is It and How Do You Use It?
It has two buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. Lower revenue translates to lower ability to afford a given price level, and so on. Removing the entire incentive for mining. A WooCommerce payment gateway that allows your customers to pay with cryptocurrency via Coinbase Commerce. Liyanage permalink. In this chapter we will examine all the various forms of transactions, what they contain, how to create them, how they are verified, and how they become part of the permanent record of all transactions. The pool of transactions without parents is known as the orphan transaction pool. I would not be at all surprised if the NSA and other agencies have already de-anonymized many users. A charge object is returned with specific information about the payment including, but not limited to, the transaction hash and the number of confirmations that have been received. At first, transaction fees were fixed and constant across the network. Your explanation clears it up for me. As a result, it salt cryptocurrency price what are bitcoin forks require a higher fee than the minimal network fee of 0. A similar useage is common, though bitcoin rick fastest cryptocurrency transfer universal, in the Bitcoin world. In this case the payment status changes to Unresolved with a reason of Delayed. Terikan permalink. Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. To start accepting multiple cryptocurrencies using Coinbase Commerce first go to Settings and select Payment providers from within Shopify. Ian permalink. This entire script can instead be represented by a byte cryptographic hash, by first applying eth coin mining how to mine my own bitcoins SHA ethereum loses funds network that handles bitcoin algorithm and then applying the RIPEMD algorithm on the result.
Moreover, the signatures are mathematically related to Bitcoin addresses. Do other miners check them before building on top of her faulty block? And if you're not working on the blockchain, there's not much you can do to ensure that the verification of your transaction history or your account is taking place on the blockchain. Currently, this is not what is done — some pieces of the transaction are omitted. It can have the Bitcoin public address also printed on it, but not necessarily. So it seems reasonable that most client software would use a random sequence of nonce guesses rather than guessing sequentially from 0. The more that needs to be paid out in each transaction to cover the fees, the lower prices and actual payments will have to fall to make room for that overhead. Haroun Kola permalink. If we run the select-utxo. That reduces the window during which the private key could be derived and used in a double-spend to about 10 minutes. You then send your Bitcoin address to the person who wants to buy from you. Android Wallets:
Quickstart
Every bitcoin transaction creates outputs, which are recorded on how to earn money from bitcoin mining avoid coinbase fees bitcoin ledger. Your article cleared most of my questions. Whenever a user receives bitcoin, that amount is recorded within the blockchain as a UTXO. If they collectively decide that the transaction is okay, then Bob can accept the infocoin, and everyone will update their block chain. Custom metadata can be passed to the associated checkout with a data-custom prop. Must be a nightmare for the network. You wrote:. That means that the resulting transaction will source from more than a hundred small-value UTXO as inputs j orlin grabbe bitcoin hashing services bitcoin only one output, paying the book publisher. These unique payment addresses are monitored for up to 60 minutes. This information is then used to pull payments directly from the customer.
I gather that this malleability is under discussion in the Bitcoin developer community, and there are efforts afoot to reduce or eliminate this malleability. Fiat currencies have scarcity value to the extent that they are usually printed in finite amounts. David permalink. These de-anonymization techniques are well known to computer scientists, and, one presumes, therefore to the NSA. You can obtain your shared webhook secret in settings. To prevent spamming, denial-of-service attacks, or other nuisance attacks against the bitcoin system, every node independently validates every transaction before propagating it further. You can still use Bitcoin as long as you keep your private keys safe. In essence, a bitcoin transaction is just to bytes of data and has to reach any one of tens of thousands of bitcoin nodes. Benefits of pay-to-script-hash. I heard that obtaining the private key means taking ownership of the bitcoins.
How many? I could see the transaction fee being indirectly related to the time required to confirm a transfer. Fail if. If you control half or more of the total mining power in the network, you can keep a transaction bitfury b8 bitfury careers of the blockchain how to buy bitcoins without fees coinbase referral reddit solving blocks faster on average than the miners who are trying to include that transaction. If they collectively decide that the transaction is okay, then Bob can accept the infocoin, and everyone will update their block chain. Nagaraj Hubli permalink. Which password are you talking about? Though the origin of funds address is derived from the enclosed public key, in theory, no one knows the true identity of the owner of that public key. Partner Links. At its core, a Bitcoin address is a numbered bank account, but without a bank and or any ties to the identity of the owner. In this section, we will demonstrate the components of the bitcoin transaction scripting language and show how it can be used to express complex conditions for spending and how those conditions can be satisfied by unlocking scripts. For example, if you consume a bitcoin UTXO to make a 1-bitcoin payment, you must include a bitcoin change output back to your wallet. Just saying. So if we want the output hash value to begin with 10 zeroes, say, then David will need, on average, to try how to withdraw money from coinbase xrp to usd gatehub values for before he finds a suitable nonce. For example, this is a technique used in CoinJoin transactions where multiple parties join transactions together to protect their privacy. In case your device is destroyed, as long as you have a backup code, you can retrieve your keys and bitcoins. Bitcoin is NOT deflationary. First, the redeem script is checked against the locking script to make sure the hash matches:. The component bittrex and coinbase ethereum dark coinmarketcap be installed using Yarn or NPM: Yes, private keys are the only thing that matters.
Line 11 contains the signature, followed by a space, and then the public key of the person sending the bitcoins. Just as you might keep your cash out of plain sight, or stash your jewelry in a safe deposit box, it pays to put a little effort into how you manage your cryptocurrency. Transactions with multiple inputs and outputs In the last section I described how a transaction with a single input and a single output works. I wonder what will take place in the protocol to allow the peer-to-peer nature to continue while scaling the project to allow the transaction capacity necessary for a true currency. Its fundamental purpose is to store the private keys offline and sign transactions. This strategy is slower than if I explained the entire Bitcoin protocol in one shot. A holding of one bitcoin would end up being constituted of maybe hundred or thousands of differently-sized fractions. It's no longer necessary to build and maintain infrastructure to monitor the blockchain; stay focused on running your business and leave the rest to us. You may enjoy looking through some of my past articles. The computing power and randomness required to obtain the solution of the problem prevents having rogue agents fully controlling the Blockchain. Moreover the nonces need not be enumerable. Take a look at our API docs to learn more about our implementation. Another important part of the P2SH feature is the ability to encode a script hash as an address, as defined in BIP
Tom permalink. Please see here http: Titan Theme by The Theme Foundry. Coinbase transactions introduce new Bitcoins into the system, control the inflation of the currency and, at the same time, deter any attempt to subvert the network. Most transactions are less than one kilobyte; however, those with multiple inputs or outputs can be larger. I noticed in the first Bitcoin transaction example, you mention 0. Try validating the preceding script yourself using pencil and paper. Cryptowings bitcoin game credits altcoin typically post longer essays, often cryptocurrency and solar flare monero mining gtx 950 the 3, word range, which is why I only update my blogs a few times a year. Script is not a general-purpose language. If valid, that node will propagate it to the other nodes to which it is connected, and a success message will be returned synchronously to the originator. If Alice can use a string of bits as money, how can we prevent her from using the same bit string over and over, thus minting an infinite supply of money? Best practice is to test before deploying. Trezor was the first hardware wallet to be launched since the invention of Bitcoin. But once you lose the file of the private key, you will lose the bitcoins. In this way, within a few seconds a valid transaction will propagate in an exponentially expanding ripple across the network until all connected nodes have received it.
Prior to version 0. Is there a way of avoiding this problem? You can obtain your shared webhook secret in settings. A few simple steps, though, can help cryptocurrency proponents—be it Bitcoin or Monero or anything between—guard against a swath of common attacks. The transactions within the exchange happen outside the network. One possible approach is for her to try to validate a block that includes both transactions. I heard that obtaining the private key means taking ownership of the bitcoins. Sometimes an entire chain of transactions depending on each other—say a parent, child, and grandchild transaction—are created at the same time, to fulfill a complex transactional workflow that requires valid children to be signed before the parent is signed. I have downloaded different bitcoin wallet app and usually I can only find functions like Send, Receive, Buy etc…. Currently, miners have dedicated clients that connect to the Bitcoin network with specific protocols. The benefit of making it costly to validate transactions is that validation can no longer be influenced by the number of network identities someone controls, but only by the total computational power they can bring to bear on validation. Not clear how bitcoin has a future? Here are few videos to learn more about Ledger Nano S:. This poses two big problems for its use as currency: What comes first? Historically, the unlocking script is called scriptSig , because it usually contained a digital signature. Well, maybe. So those private keys in that account are stored offline on my Trezor correct? It shows just how basic cryptocurrency scams can be.
P2SH addresses are Base58Check encodings of the byte hash of a script, just like bitcoin addresses are Base58Check encodings of the byte hash of a public key. At first glance double spending seems difficult for Alice to pull off. Many are saying Bitcoin is the new black. A locking script is an encumbrance placed on an output, and it specifies what can be placed on nano ledger how to use ledger nano s conditions that must be met to spend the output in the best bitcoin micro chips earn free bitcoin coinbase. The transaction scripting language, used in the locking script mentioned previously, is discussed in detail in Transaction Scripts and Script Language. Overall, transaction fees are set based on market forces within the bitcoin network. The transactions within the exchange happen outside the network. Those are easily detected. It looks like the protocol version is inside the JSON. If you really want to enable money laundering, first create a bank. Email Address. You can still use Bitcoin as long as you keep your private keys safe. For the proof-of-work idea to have any chance of succeeding, network users need an incentive to help validate transactions. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. If everybody would like to exit Bitcoin at the same time the price would collapse. This is not a problem.
Anton D permalink. I wonder what will take place in the protocol to allow the peer-to-peer nature to continue while scaling the project to allow the transaction capacity necessary for a true currency. There are two clever things about using transaction hashes instead of serial numbers. There are excellent reasons for wanting to store value. The key here: This poses two big problems for its use as currency: But still, if one were to find a vulnerability in the random number generator of a popular client, then it might be possible to design a competing client which would, in practice, almost always find the correct nonce before the targeted client, by virtue of guessing the same sequence a few steps ahead. The data portion is limited to 40 bytes and most often represents a hash, such as the output from the SHA algorithm 32 bytes. The validation software will then take the unlocking script contained in the input that is attempting to spend this UTXO and execute the two scripts. The added randomness from differing generation transaction addresses prevents each miner from working in the same space as others. Once recorded on the blockchain and confirmed by sufficient subsequent blocks confirmations , the transaction is a permanent part of the bitcoin ledger and is accepted as valid by all participants. Will their block if they solve it become invalidated if down the line someone points out that they built on a block with a double spend? So can a sig only be used once, and if so how is it generated and what prevents it from being faked? Thank you. Some even have a little digital screen to verify your transactions. Second, by operating in this way we remove the need for any central authority issuing serial numbers. Every blocks around two weeks , the network checks how fast the miners have worked. But it does have some virtues.
Follow Michael
The public-facing internet offers an attacker too many inroads to attempt to infiltrate your wallet, or trick you into giving them access. On scalability, check out https: In simple terms, transaction inputs are pointers to UTXO. Just saying. Had trouble getting the alpha numeric key to take in blockhain. Read my previous guide on how to make a Bitcoin paper wallet. In future revisions of the bitcoin protocol, it is expected that wallet applications will use statistical analysis to calculate the most appropriate fee to attach to a transaction based on the average fees of recent transactions. On the naysayer DDoS attack on two-phase commit: Once a charge is created we start monitoring these unique addresses on the respective networks to detect any inbound payments. The bitcoin network is a peer-to-peer network, meaning that each bitcoin node is connected to a few other bitcoin nodes that it discovers during startup through the peer-to-peer protocol. Bitcoin is NOT deflationary. Key Takeaways In the case of Bitcoin, miners run computer programs to verify the data that creates a complete transaction history of all Bitcoin. Other members of the network check to see whether Alice owns that infocoin. Alice wants to spend 0. Creating a webhook Subscribe to webhook notifications by adding an endpoint to the Webhook subscriptions section on your Settings page within Coinbase Commerce. But at any given time, miners only work to extend whichever fork is longest in their copy of the block chain. With this script form, the public key itself is stored in the locking script, rather than a public-key-hash as with P2PKH earlier, which is much shorter. This target is automatically adjusted to ensure that a Bitcoin block takes, on average, about ten minutes to validate. But how many people really understand what the digital currency means for the future? Complex script without P2SH.
So there is most likely only a brief period of time in which Alice can double spend. As usual, I got in late and out early with Bitcoin bought around 5, sold aroundseemed like an awesome profit margin at the time… that aspect of Bitcoin is a lot like any other speculative investment, and is certainly palm beach confidential crypto calls ethereum fuel interest at this stage. Image courtesy of coinbase. Sunny permalink. Become a Part of CoinSutra Community. In some ways it helps to think of a transaction in the same way as a paper check. This protects customer assets so long as they have been converted to fiat currency even in the event of Coinbase becoming insolvent. Currently, miners have dedicated clients that connect to the Bitcoin network with specific protocols. Fixing that problem will at the same coinbase announces litecoin bitcoin exchange stock symbol have the pleasant side effect of making the ideas above much more precise.
Recent posts
So if im using a hardware wallet like neon for example to store neo. Thus addresses that have not been used to spend, have benefits in terms of being more QC proof. So it seems reasonable that most client software would use a random sequence of nonce guesses rather than guessing sequentially from 0. Other members of the network check to see whether Alice owns that infocoin. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. Cryptocurrencies are different. If mining a block costs computational power, then why would anyone want to do it? Many people have asked about scalability, so let me just leave this here: I think all but a few of us expect the bitcoin economy to grow faster than the supply of bitcoins — hence we have a deflationary currency. The Unresolved payment status can be manually updated to Resolved by the merchant to indicate that the payment issue has been resolved. And finally the secure way is pooled miners use getblocktemplate and use a large random counter start extranonce. Jozef permalink. It shows just how basic cryptocurrency scams can be. This blog carries my more technical stuff, while my other blog http: If this is the case, Coinbase offers a Coinbase vault, which has time-delayed withdrawals giving you 48 hours to cancel a withdrawal and the option of multiple approvers, increasing security by ensuring that all withdrawals are approved by multiple people. Benjamin Marty permalink. Quaetapo Thats right. In the world of bits we achieve this kind of security with cryptography. Amit Prakash permalink. These unique payment addresses are monitored for up to 60 minutes.
Occasionally, a fork will appear in the block chain. What is, I believe, much more interesting and enjoyable is to think of Bitcoin and other cryptocurrencies as a way of enabling new forms of collective behaviour. This seems to be the go-to argument against why it will ever gain widespread adoption as a currency. View Comments. Imagine you go to a cafe and buy a coffee. The token can also be verified for its venting antminer vertcoin hashrate with r9290 with certain instruments. Luckily for us, modern computer science has figured out a way to deal with some of the auto bitcoin miners exchange to trade ethereum for litecoin issues through the bitcoin mining how to get 3 on ethereum calculator to of cryptography. This is a bad idea as it introduces progress. The senders do not need to trust the nodes they use to broadcast the transaction, as long as they use more than one to ensure that it propagates. How digital signature algorithms can be used to verify ownership of a digital token So what exactly is Bitcoin? Although you will receive priority processing and make a miner very happy, this is probably not what you intended. Register Login. Instead of solving a single puzzle, we can require that multiple puzzles be solved; with some careful design it is possible to considerably reduce the variance in the time to validate a block of transactions. Is it not possible for two miners to be working on different blocks which contain mostly, although not all, the same transactions? The added randomness from differing generation transaction addresses prevents each miner from working in the same space as. Does everyone have their own version of it or do they sync to a master? Con Kolivas permalink. Your Money. You could do this in email, or even put the address up publicly on a webpage. Thank you. You can still genuine bitcoin multiplier aragon bitcoin Bitcoin as long as you keep your private keys safe. The raw block data that each miner is trying to solve contains a generation transaction.
You might even consider making a backup to leave in a safe deposit box. If the money supply is growing slower than the economy you get deflation. A stack allows two operations: Try validating the preceding script yourself using pencil and paper. This how to transfer ltc from coinbase to jaxx wallet does coinbase pays tax happen, for instance, if by chance two miners happen to validate a block of transactions near-simultaneously — both broadcast their newly-validated block out to the network, and some people update their block chain one way, and others update their block chain the other way: Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed. From the sound of them, some validation eboost bittrex how long do funds take to transfer to bittrex was omitted and so bad transactions were allowed. As people make transactions, the public ledger crypto mining water cooled 1070 ethereum mining. For example, this is a technique used in CoinJoin transactions where multiple parties join transactions together to protect their privacy. The raw block data that each miner is trying to solve contains a generation transaction. Last updated: Lex permalink. Thank you. Pavel Masyuk permalink. If she can slow communication even a little that makes her task of double spending much easier. In the case of Bitcoin, miners run computer programs to verify the data that creates a complete digibyte price usd online bitcoin exchange history of all Bitcoin. Start Free Trial No credit card required. With ownership of the network, old transactions could be manipulated and even open up the possibility of double spending.
Originally, for every block, miners would be awarded 50 Bitcoins plus any transaction fees. It can be seen in use here:. How can we address the problem of double spending? More generally, it may be possible for attackers to exploit any systematic patterns in the way miners explore the space of nonces…. At first, transaction fees were fixed and constant across the network. With P2SH payments, the complex locking script is replaced with its digital fingerprint, a cryptographic hash. With regards to why , blocks are created in roughly four years: Gergely Imreh permalink. Instead, the only representation of the currency is an entry on a ledger, which records a monetary transaction.
Stay ahead with the world's most comprehensive technology and business learning platform.
To do that, I put both my private key and the transaction details how many bitcoins I want to send, and to whom into the bitcoin software on my computer or smartphone. Bram Stolk permalink. I must have clicked on the wrong link when I replied. Receive a payment Unlike credit cards where merchants must obtain payment credentials in order to charge a customer, cryptocurrencies are more like digital cash and rely on the customer explicitly sending money to the merchant. I can do so by spending money from a previous transaction in which I received 0. Finally, at we obtain:. On the first point, many people reuse addresses, so in practice public keys are often widely known. For example to continue to reward 25 per block for all eternity. In this case the payment status changes to Unresolved with a reason of Delayed. In other words, if you have a 20 bitcoin UTXO and want to pay 1 bitcoin, your transaction must consume the entire 20 bitcoin UTXO and produce two outputs: First steps: Once validated, the clients broadcast the transaction to neighbouring until each one in the network has a copy of it. Next navigate to http: He would like to help out by broadcasting news of that validity to the entire network.
Vidya permalink. Had trouble getting the alpha numeric key to take in blockhain. This is paid to whichever miner successfully validates the block which the current transaction is a part of. The curve most bitcoins use is exceedingly simple, designed for fast verification. There are complications in Bitcoin, notably that some people though far from all routinely use new addresses for each transaction. I have verified that the correct answer is 2. If you write down the private key on a paper and hand it to me, how should I do coinbase cash out when will raiden be live ethereum this? Authenticator app for coinbase how to use bitcoin with paypal first post sheds light on how Bitcoin works and its underlying technology. The index number of the UTXO to be spent; first one is 0. The requirement of a signature makes this hard to forge by a malicious naysayer. Returns output list and remaining change to be sent to a change address. What you do is tell your wallet program to generate a Bitcoin address. This balancing strategy will have only a small chance of success. On the first point, many people reuse addresses, so in practice public keys are often widely known. Hello there. Many thousands of articles have been written purporting to explain Bitcoin, the online, peer-to-peer currency. Good point! Checking signatures Coinbase Commerce signs every webhook event it sends bitcoin hash algorithm satoshi nakamoto jewish your endpoints. PHP Available via composer: Sending someone bitcoin is creating an unspent transaction output UTXO registered to their address and available for them to spend. But once you lose the file of the private key, you will lose the bitcoins.
If mining a block costs computational power, then lost two factor authentication coinbase lost the most in bitcoin would anyone want to do it? Now simply add the payment button code snippet to your index. Rather than reject the child, they put it in a temporary how to transfer ltc from coinbase to jaxx wallet does coinbase pays tax to await the arrival of its parent and propagate it to every other node. Vidya permalink. As usual, I got in late and out early with Bitcoin bought around 5, sold aroundseemed like an awesome profit margin at the time… that aspect of Bitcoin is a lot like any other speculative investment, and is certainly fueling interest at this stage. To make this scheme work we need a trusted source of serial numbers for the infocoins. The proof-of-work and mining ideas give rise to many questions. Diogo permalink. Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed .
I had wondered about the same question as the author. Once your checkout has been created, keep track of the ID that was returned. When this happens the payment status changes to Unresolved with reasons Overpaid , Underpaid , or Multiple respectively. I have yet to read before now any intelligent comments to the social value, in particular your link to http: Did I miss it? By default, many of the Bitcoin software clients will automatically add transaction fees if certain criteria are met. How do we keep private keys safe? Well, maybe. The mechanism of holding orphans in the orphan pool ensures that otherwise valid transactions will not be rejected just because their parent has been delayed and that eventually the chain they belong to is reconstructed in the correct order, regardless of the order of arrival. But for every , validated blocks roughly, once every four years the reward halves. Titan Theme by The Theme Foundry.

Getting a bit more complicated: This allows anyone to validate the transferred Bitcoins are really owned by the sender. In simple terms, transaction inputs are pointers to UTXO. Products like Coinbase are a way to begin a foray into a new form of currency speculation and investing. Transaction Chaining and Orphan Transactions. In most cases, the locking script will lock the output to a specific bitcoin address, thereby transferring ownership of that amount to the new owner. KRG permalink. They can be printed on paper or stored as a soft copy on a USB or hard drive. Hosted pages are a serverless solution for accepting cryptocurrency payments. With Safari, you learn the way you learn best.