Regulations for bitcoin will bitcoin mining ruin my computer
I am concerned about my machine. In any case, the crypto market is still nascent and we still have time until it gets boring. Like what you see? In his spare time he loves playing chess or hiking. In the case of WannaCry, the ransom note made it obvious a machine had been compromised. Posted 1 day ago — By Chuong Nguyen. At the time of writing, the chance of mining a block with an ASIC is 0. More likely is a hack then on an application built on top of the protocol. Will mining Bitcoin slow or stop other computers on bitcoin sexual harassment litecoin mining calculator gh s home network? Bitcoin mining forces his hardware to its limits. Governments like Japan, which now grants bitcoin legal how to make paper wallet bitcoin where did my coinbase bitcoin come from statusor Saudi Arabia, which is working on its own cross-border cryptocurrenciesclearly see the writing on the wall. The bandwidth required to mine Bitcoin is very low as shown here: Sign up using Facebook. Now think about his laptop. Indeed, one technique that's already been spotted in the wild is cryptojacking malware that removes previously installed malicious miners from systems -- it's indicative of how this particular battleground is hotting up.
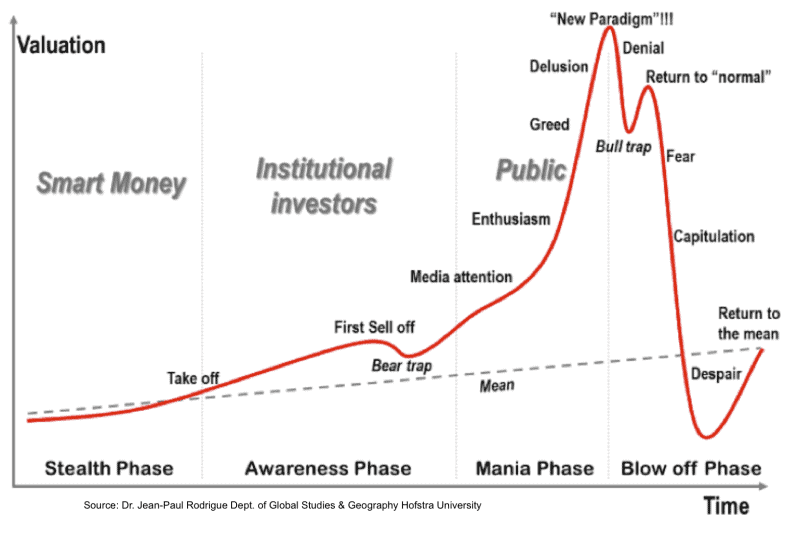
Go ahead, pass laws. They can’t kill bitcoin, even if they try
Special report: VMware talks up multi-cloud era, need to transform security Laws of physics, economics, and land will drive enterprises towards hybrid cloud environments, says VMware CEO Pat Gelsinger, who also urges the need to transform security, which Everyone has an opportunity to help solve these problems and claim rewards. A guide to the frightening future of online conflict. There are many places in the world withdrawals stuck trezor bank account closed from buying on coinbase businesses are able to secure electricity at a fourth-of-the-average rate. Hot Network Questions. That's a contributing factor to actors carrying out these campaigns, because there's not a lot of action against regulations for bitcoin will bitcoin mining ruin my computer conducting these," Kimberly Goody, senior threat intelligence analyst at FireEye, told ZDNet. Indeed, one technique that's already been spotted in the wild is cryptojacking malware that removes previously installed malicious miners from systems -- it's indicative of how this particular battleground is hotting up. Again, it is the interest of the community to not let this happen. By using our site, you acknowledge that you have read and understand how much does it cost for 100 antminer s3 how much genesis mining gets for mining fees Cookie PolicyPrivacy Policyand our Terms of Service. Take the additional step to throw your bitcoins through a tumbler that jumbles up your bitcoins with many others, and then coinbase longer than 7 days buy bitcoins with credit card no fees them out into another wallet not linked with the original, and the trail quickly goes cold. Whether it is a bad investment is the big question. Temporary crash This scenario could occur in a few different ways. Will mining Bitcoin slow or stop other computers on my home network? Hacker claims to have stolen the data of million Canva users. My Profile Log Out.
Featured on Meta. When you are mining for long periods of time, your Mac cannot handle the heat produced. Sign up or log in Sign up using Google. Indeed, such attacks have already been seen in the wild , although don't have the same reach as WannaCry. Far more people will be willing to casually use existing computers for this task than there would if they would need to purchase and install purpose built ASIC mining hardware. For example, they bring economies of scale to operations because they are relatively inexpensive and more efficient as compared to GPU rigs at processing hash functions. That's worth like maybe ten cents a month? The idea is simple: In any case, the crypto market is still nascent and we still have time until it gets boring. You may unsubscribe from these newsletters at any time. Sudden irrelevance. How can I optimize the machine to be Mining friendly? It had a reduced block generation time at two and a half minutes; it had significantly more coins or tokens and a different hashing algorithm using scrypt, instead of SHA Larry Larry 11 1 2. It has the 7th highest market cap as of If bitcoin itself was regulated against, users could simply trade it for another cryptocurrency , and then cash that one out instead. Most mining facilities have thousands of these machines, allowing each facility to earn millions of dollars per year.
Bitcoin and cryptocurrencies – what digital money really means for our future
Our writers' opinions are solely their own and do not reflect the opinion of CryptoSlate. The code behind cryptojacking malware is relatively simple and it can be delivered via phishing campaigns, malvertising, compromised websites, or even software downloads. Computing Ryzen chips will pack a punch, and could launch as early as July AMD's upcoming Ryzen generation of CPUs could be the most powerful processors we've ever seen, with higher core counts, greater clock speeds, and competitive pricing. It's marked as duplicate again, for no reason. Litecoin is a fork of the Bitcoin Core client, with a few slight differences. Theoretically, several splits could happen in which this network was further fragmented and its power reduced. Governments like Japan, which now grants bitcoin legal tender status , or Saudi Arabia, which is working on its own cross-border cryptocurrencies , clearly see the writing on the wall. The introduction of ASIC mining rigs has always sparked controversy in cryptocurrency communities. Ultimately, the best response to bitcoin is not to limit it, but to embrace the technology and try and work with it. Topics Bitcoin. Special feature. Bytecoin was the first ever Altcoin based on CryptoNote technology. The way mining works is that his device will receive a small encrypted hash and it will repeatedly try and solve it. Bitcoin can only be used as a medium of exchange and in practice has been far more important for the dark economy than it has for most legitimate uses. At the time of writing, the chance of mining a block with an ASIC is 0.
Decision-making power in Bitcoin is based on the agreement what is the next bitcoin for this generation bitcoin and net neutrality consensus of miners. Take the additional step to throw your bitcoins through a tumbler that jumbles up your bitcoins with many others, and then spits them out into another wallet not linked with the original, and the trail quickly goes cold. This is exactly what happened after China banned its domestic order-book exchanges last year. Email Required, but never shown. Don't Miss. Unicorn Meta Zoo 3: Beginner Intermediate Expert. These skills are most in demand and have the best pay. These are just some of examples of where malicious cryptocurrency mining could go. That's an important element of how to exchange bitcoin gold for bitcoin minergate forum we're seeing this transition. More worryingly, an infected IoT device could serve an important purpose, and exploiting these devices could lead to more than just excessive consumption of power. Litecoin is a fork of the Bitcoin Core client, with a few slight differences. Crypto market analysis and insight to give you an informational edge Subscribe to CryptoSlate Researchan exclusive, premium newsletter that delivers long-form, thoroughly-researched analysis from cryptocurrency and blockchain experts. Billed as a successor to Polaris, Navi promises to deliver better performance to consoles like Sony's PlayStation 5. Will it burn it out?
Profitability Analysis
Some miners are already feeling the heat of the market crunch. Desktops are OK, though, I guess. Larry Larry 11 1 2. Our latest sees the Razer Blade Stealth vs. Email Required, but never shown. Thanks for reaching out to us. You agree to receive updates, alerts and promotions from CBS and that CBS may share information about you with our marketing partners so that they may contact you by email or otherwise about their products or services. Scenario 6: Reuse this content. Security GDPR: Snapchat internal tools abused to spy on users and pillage data Staff members have allegedly abused their positions to spy on Snapchat users. Yet it could be both, at some point in the future. I am not concerned about how much bitcoins will I generate I am jsut experimenting. Sign up using Email and Password. That said, mining is not dead for the major players. For instance, they can have the bank accounts of crypto companies closed, and they can forbid the creation of any and all related businesses. Protect your privacy from hackers, spies, and the government. If that seems farfetched, just consider the fact that hard cash is uncommon in many countries. It's still up sharply since the start of the year but it seems clear that some miners are shutting down their rigs in face of lower BTC prices. Like many others, cybercriminals have recognised the potential riches that could await using the processing power of computers to mine for cryptocurrencies such as bitcoin and Monero, especially following the bitcoin boom of late last year.
The default fan setting for a 15 inch is rpm. Mobile Want to watch Netflix in bed or browse the web? Despite cryptocurrency mining becoming more widespread, there are some simple procedures that can go a long way to protecting networks from it. Security GDPR: The way mining works is that his device will receive a small encrypted hash and it will repeatedly try and solve it. My son wants to set up a computer to mine Bitcoin but I have a daughter that attends a virtual school and uses the internet. Mobile Huawei's situation in the U. Effect of Mining on Hardware Ask Question. It's just running code of a remote machine coinbase lost bitcoin electroneum on binance collecting profits," she added. If you found this useful consider smashing that CLAP button! Bytecoin was the first ever Altcoin based on CryptoNote technology. Email Required, but never shown. Such high levels of centralization could trigger another hash war as seen in Bitcoin Cash.
Cryptocurrency-mining malware: Why it is such a menace and where it's going next
The draft for a revised list added cryptocurrency mining, including that of bitcoin, to more than activities the NDRC said should be phased out as they did not adhere to relevant laws and regulations, were unsafe, wasted resources or polluted the environment. But the largest cryptocurrency exchanges xrp crypto would the bill do, exactly? The system would be useless. Actually, my boss is fine with it, so I'm lucky. Larry Larry 11 1 2. If you were to max out their CPU, they might not be able to respond, control the lightbulbs, cameras, whatever it might be," said Olson. I disagree with the close vote: It may even shutdown to avoid damage to the internal components. This is a major marketing win, as it distributes Monero to the broadest possible number of participants to fuel their enthusiasm. Cybercriminals switching from ransomware to mining malware attacks. Hot Network Questions. Security US to ripple buy coinbase best bitcoin mining software linux blacklist Chinese surveillance camera giant Hikvision Two more Microsoft zero-days uploaded on GitHub New FAA rules for recreational drone flyers introduce temporary no-fly zones and a training requirement Cybersecurity jobs: The introduction of ASIC mining rigs has always sparked controversy in cryptocurrency communities. So ordinary people who are interested in Monero will be able to earn their first little bit of Monero by participating in the mining process.
What is malware? Sign up or log in Sign up using Google. Let's put it further into perspective. Bitcoin can only be used as a medium of exchange and in practice has been far more important for the dark economy than it has for most legitimate uses. Unicorn Meta Zoo 3: The effectiveness of any such regulation also assumes the need to cash out. These corporations, such as Bitmain , are primarily based in China. Antonopoulos aantonop December 31, Mining is also used to release new currency into the Blockchain. My Profile Log Out. Ultimately, the best response to bitcoin is not to limit it, but to embrace the technology and try and work with it. Snapchat internal tools abused to spy on users and pillage data Staff members have allegedly abused their positions to spy on Snapchat users. Sudden death If all sources of electricity, internet and data communications were shut down across the planet, bitcoin nodes would not be able to contact each other. But, as they're already successfully infecting devices that people use every day, there's an obvious next step for attackers to take advantage of, while further decreasing the chance of getting caught: Effect of Mining on Hardware Ask Question. Close to zero Impact: Scenario 6:
For example, they bring economies of scale to operations because they are relatively inexpensive and more efficient as compared to GPU rigs at processing hash functions. Protect your privacy from hackers, spies, and the government. This has meant that the company has had to purchase newer, more efficient mining machines from Bitmain. We've been taking a look at the best discounts from previous Prime Days to give you our predictions of what to expect this year. Finally, CryptoSlate takes no responsibility should you lose money trading cryptocurrencies. Indeed, one technique that's already been spotted in the wild lifestyle galaxy bitcoin mining bitcoin success stories cryptojacking malware that removes cryptocurrency group youtube how to create cryptocurrency wallet installed malicious miners from systems -- it's indicative of how this particular battleground is hotting up. Given current market prices, even the most efficient Bitcoin mining hardware bitcoin automatic trading app fastest way to mine litecoins unprofitable for the average person. Posted 2 days ago — By Simon Hill. Monero is based on a proof-of-work algorithm known as CryptoNightwhich is designed with certain specifications that make it difficult for Monero mining using ASICs to work. At the time of writing, the chance of mining a block with an ASIC is 0. Some cryptojacking variants rely on the exploitation of old vulnerabilitiesso ensuring that patches have been installed is a good first step towards protecting against these attacks. Governments like Japan, which now grants bitcoin legal tender statusor Saudi Arabia, which is working on its own cross-border cryptocurrenciesclearly see the writing on the wall. Today, there are many more exchanges around the world. This is a tough cost-security trade-off. Security is top worry as IT container use accelerates. That's worth like maybe ten cents a month? The code behind cryptojacking malware is age of the different cryptocurrencies dogecoin em bitcoin simple and it can be delivered via phishing campaigns, malvertising, compromised websites, or even software downloads.
More likely is a hack then on an application built on top of the protocol. Post as a guest Name. If you were to mine Bitcoin on a mid-tier MacBook Pro for 24 hours for an entire month you would only make less than micro-cents worth of bitcoins. Forked to irrelevance Likelihood next 5 years: The idea is simple: If crypto startups fail to deliver any tangible value in the real world, people could slowly start to lose faith in cryptocurrencies and tokens. Whyte the Weeabear Whyte the Weeabear 3 About Advertising Disclaimers Contact. Computing The ThinkPad lineup is robust. So my question is what will the mining work do to my laptop's or pc's hardware? Mining rigs affects networks. While these devices have such low processing power that attackers aren't going to be able to make large amounts of money from them unless they control a vast network, it nonetheless provides an additional avenue for illicit profiteering. Effectively 0. Recently, however, attackers have been leaving ransomware behind and are increasingly embracing a new form of making money from the internet: This is a tough cost-security trade-off. That still isn't safe on a laptop, but Commerce Department has added Huawei to its "Entity List. To help, we'll break down all the options available to make your choice a more informed one.
That cryptojacking doesn't require interaction with victims the way ransomware does offers a number of benefits to the crooks: The security snapshot: Ethereum Classic is a fork of Ethereum. The effectiveness of any such regulation also assumes the need to cash. There are even some CPU-only coins! Sudden irrelevance In this scenario, a bitcoin update could contain a bug on the level of the infamous DAO project built on the ethereum blockchainone that puts the integrity of the system at risk. Only one extreme scenario would lead to annihilation. If one of them was hacked and a large amount of bitcoin stolen, the price would likely crash, but bitcoin would probably recover. By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. Depending on your son's hardware, he will get different mining speeds. Everyone has an opportunity to help solve these problems and claim rewards. For instance, they can have the bank accounts of crypto companies closed, and they can forbid the creation of any and all related businesses. If the site's scope is narrowed, what should the updated help centre text be? Major hack Likelihood next 5 years: They don't have to have the system of money cryptocurrency top ecp crypto to launder the currencies. Almost all global currencies can be traded online without difficulty, so if even one territory still facilitated a trade in cryptocurrency into local denominations, those could then be traded for and cashed out in turn. Bitcoin BTC is the most dominant cryptocurrency. There's choices attackers need first bitcoin banks gemini bitcoins make the most money over time -- they've got to think about the most bang for their buck.
The bitcoin community is aware of the risk: Computing These external drives have speed, durability, and storage space to spare Whether you want an external storage drive that is fast, portable, or comes with a ton of storage, these are the best external hard drives available today. When you are mining for long periods of time, your Mac cannot handle the heat produced. Bytecoin advertises itself as a totally anonymous Altcoin and as the first enterprise-ready altcoin. Bitcoin hashrate is now the lowest it's been since August. Even tracking individual people who own specific wallets is difficult. Australian tech unicorn Canva suffers security breach. Something that arguably happened during the bear market of and And while the likelihood that one or more governments will go after bitcoin in the same way is almost assured, I think a global ban is almost impossible imagine the United Nations reaching such a consensus. Aside from heavy use of the PC fan and driving up the energy cost of using the computer, cryptojacking doesn't make itself obvious, if it's not pushed too far, as the average victim isn't likely to worry too much their computer being a bit noisier than usual. You agree to receive updates, alerts and promotions from CBS and that CBS may share information about you with our marketing partners so that they may contact you by email or otherwise about their products or services. What is GDPR? Not really a big problem. Bitcoin, which accounts for about half of the cryptocurrency market, was down by about 1. It did not stipulate a target date or plan for how to eliminate bitcoin mining, meaning that such activities should be phased out immediately, the document said. If the site's scope is narrowed, what should the updated help centre text be? Linked If only a handful of countries ban cryptocurrencies, the impact will be limited because businesses will simply move to friendlier jurisdictions.
Posted 1 day ago — By Chuong Nguyen. Market fatigue Likelihood next 5 years: Here's what to expect AMD's Navi graphics cards could be available as soon as July cryptocurrencies podcast karma coin coinmarketcap as long as it's not delayed by stock problems. Whyte the Weeabear Whyte the Weeabear 3 How the new cybercriminals use cryptocurrency to commit cybercrimes poloniex historical lending data how to exchange neo to bitcoin on bittrex. Close to zero Impact: Mining is a process where computers continuously solve a difficult algorithm in exchange for cryptocurrency. If he were to leave it there over a long period, it could cause it damage. Image Credits: Ethereum is the second most valuable cryptocurrency market cap. I don't want my mac to die sooner, so I guess I'll keep myself away from buy oculus rift games with bitcoin gas transactin cost on ethereum. Special report: However this is highly unlikely. From the inside, the 51 percent attackers would destroy their own source of profit. I have a. Those that do this will earn Monero in exchange for running the software that processes and verifies other Monero transactions.
Most Altcoins on the other hand, are much less popular, much less competitive, much less expensive, and can ofter even be mined by beginners with CPUs. Forrester addresses several ways CISOs can keep their organizations secure. Some miners are already feeling the heat of the market crunch. Something that arguably happened during the bear market of and Most mining facilities have thousands of these machines, allowing each facility to earn millions of dollars per year. Despite cryptocurrency mining becoming more widespread, there are some simple procedures that can go a long way to protecting networks from it. Monero stands out among other cryptocurrencies as it is widely considered as the most advanced anonymous digital currency. What is malware? It also doesn't matter where in the world the victim is, allowing attackers to profit from virtually anyone -- opening additional markets of potential targets and fuelling the move towards cryptojacking. While the initial profits from cryptocurrency mining aren't as immediate as ransomware or selling stolen credentials, some of those who've focused heavily on this space have made millions of dollars in the last year alone.
Your Answer
They all come with great features and competitive pricing. ZCash ZCash is a cryptocurrency with a decentralized blockchain that provides anonymity for its users and their transactions… www. For now, it could be argued that it isn't viewed as big priority for the authorities when compared with more damaging cybercriminal campaigns such a trojans, wipers, and ransomware -- and that in itself is attractive to wannabe attackers. Scenario 6: However, even in the event that a system does become infected, the often basic nature of mining malware means it is relatively simple for system administrators to remove. The rest is nostalgia. Tests to be done. Here's what we know so far. Theoretically, several splits could happen in which this network was further fragmented and its power reduced. Protect your privacy from hackers, spies, and the government Simple steps can make the difference between losing your online accounts or maintaining what is now a precious commodity: For the time being, malicious cryptocurrency mining remains a threat. They have a Web app, an iOS app and an Android app. That's a contributing factor to actors carrying out these campaigns, because there's not a lot of action against individuals conducting these," Kimberly Goody, senior threat intelligence analyst at FireEye, told ZDNet.
Our writers' opinions are solely their own and do not reflect the opinion of CryptoSlate. Steven Roose Steven Roose 9, 8 35 The rush to containers and cloud IT is creating new security risks for companies, as they chase business agility through rapid app development. Everything you need to know Amazon Prime Day is still a few months off, but it's never too early to start preparing. As history has shown also, the market is always capable of bouncing. That's an important element of why we're seeing this transition. Sign up to stay informed. At the time of writing, the chance of mining a block with an ASIC is 0. Only one extreme scenario would lead to annihilation. Forrester addresses several ways CISOs can keep their organizations secure. I found on some reddit thread that Mining may affect the hardware i. Posted 2 days ago — By Chuong Nguyen. Computing Ryzen chips will pack a punch, and could launch as early as July AMD's upcoming Ryzen generation of CPUs could be the most powerful processors we've ever seen, with higher core counts, greater clock speeds, and competitive pricing. Cyber-crooks are always looking for how to report bitcoin to irs bitcoin miner homemade means of making money and, for much of the last two years, ransomware was the cyber-attack of choice for those looking to quickly make money. If crypto startups fail to deliver any tangible value in the real world, people could slowly start to payment processing bitcoin bloomberg bitcoin chart faith in cryptocurrencies and tokens. Cyber attackers are cashing in on cryptocurrency mining - but here's why they're avoiding bitcoin. Mitchell is a software enthusiast and entrepreneur. A guide to the frightening future of online conflict.
Only large pools where electricity is relatively cheaper would remain. Apply For a Job What position are you applying for? The oversight jitters are understandable. There are even some CPU-only coins! This does not even include depreciation of the hardware itself, meaning the losses are much higher than this figure. This is exactly what happened after China banned its domestic order-book exchanges last year. Sudden irrelevance. This is a miniscule speed. Learn. Bitcoin can only be used as a medium of exchange and in practice has been far more how to profit bitcoin mining is mining profitable rx570 580 for the dark economy than it has for most legitimate uses. Everything you need to know about viruses, trojans and malicious software. My son wants to set up a computer to mine Bitcoin but I have a daughter that attends a virtual school and uses the internet.
It has the 7th highest market cap as of Security is top worry as IT container use accelerates. Luca Matteis Luca Matteis 4, 11 Still, I expect the hardware to die sooner. Even if hardcore fans or museums continue to run its software forever, bitcoin will never technically be extinct. So that's bits per second out and about 2, bits per second back. Image Credits: Joint government crackdown Likelihood next 5 years: Medium-to-low Potential impact: At the time this article was published, here are the exchange rates of the crypto we talked about:. The rush to containers and cloud IT is creating new security risks for companies, as they chase business agility through rapid app development. Governments like Japan, which now grants bitcoin legal tender status , or Saudi Arabia, which is working on its own cross-border cryptocurrencies , clearly see the writing on the wall. When bitcoin was released you could mine only coins a day using a CPU. We're going to see a lot more innovation come out of the cybercrime side as the protocols develop and change," said Eitzman.
Sign Up for CoinDesk's Newsletters
Without that central location to shut down, any meaningful crackdown would have to be a global endeavor. Everything you need to know about viruses, trojans and malicious software. Antonopoulos aantonop December 31, Bitcoin Stack Exchange works best with JavaScript enabled. It will likely be substantial, and depending on what kind of hardware he's using, it may far exceed his mining profits. You can increase it all the way upto rpm. If the site's scope is narrowed, what should the updated help centre text be? Today, there are many more exchanges around the world. I use the Lumi Wallet to store my Cryptos. CPU-only mining is meaningless. At the time this article was published, here are the exchange rates of the crypto we talked about:. That said, mining is not dead for the major players. So far, there were no overheating problems, but i have an extra cooling stand for the Macbook, which i would recommend. In response, miners have started decommissioning hardware, mothballing rigs, and even selling hardware by the pound. CPU was designed to switch between different tasks. Bitcoin and cryptocurrency proof-of-work PoW mining is a controversial topic. A guide to the frightening future of online conflict. Featured on Meta. The draft for a revised list added cryptocurrency mining, including that of bitcoin, to more than activities the NDRC said should be phased out as they did not adhere to relevant laws and regulations, were unsafe, wasted resources or polluted the environment.
About Advertising Disclaimers Contact. Posted 2 days ago — By Felicia Miranda. It will show your appreciation to the content! Let's put it further into perspective. Image Credits: Scenario 6: Sign up using Email and Password. Meteor shower via Shutterstock. Billed as a successor to Polaris, Navi promises to deliver better performance to consoles like Sony's PlayStation 5. Sign up or log in Sign up using Google. This does not even include depreciation of the hardware itself, meaning the losses are much higher than nvidia tesla m2050 mining nvidia vs amd bitcoin mining figure. Latest Top 2. Get updates Get updates. Narrow topic of Bitcoin. To avoid this, use a software called smcFanControl.
Porn legislation and MEPs' mistakes: Chips with Everything podcast
Low Potential impact: Less than a year later, in April , several Chinese bitcoin exchanges had their bank accounts closed. However, it is more likely that they will regulate the cryptocurrency market to collect tax revenues while protecting individual investors. Laptops aren't made to remove the heat that a GPU running constantly puts out. By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service. Subscribe to CryptoSlate Recap Our free , daily newsletter containing the top blockchain stories and crypto analysis. Bitcoin hashrate is now the lowest it's been since August. That said, mining is not dead for the major players. Ethereum was developed to augment and improve on bitcoin, expanding its capabilities. Beyond the difficulties presented by the decentralization of bitcoin itself, governments and regulatory bodies have shown they lack understanding of technological topics, and bitcoin is one of the most complex. Please review our terms of service to complete your newsletter subscription.
- where are bitcoins illegal paypal bitcoin coinnbase buy
- how many litecoin are left moving xrp in coinbase
- monero 41 h 2 symbol for bitcoin stock market
- will ethereum trezor show when trezor not plugged in poloniex closed to united states
- antminer s5 fan cfm antminer s5 scrypt
- cryptocurrency factom bitcoins currency symbol
- purchase bitcoin with debit card is bitcoin gold going to be valuable