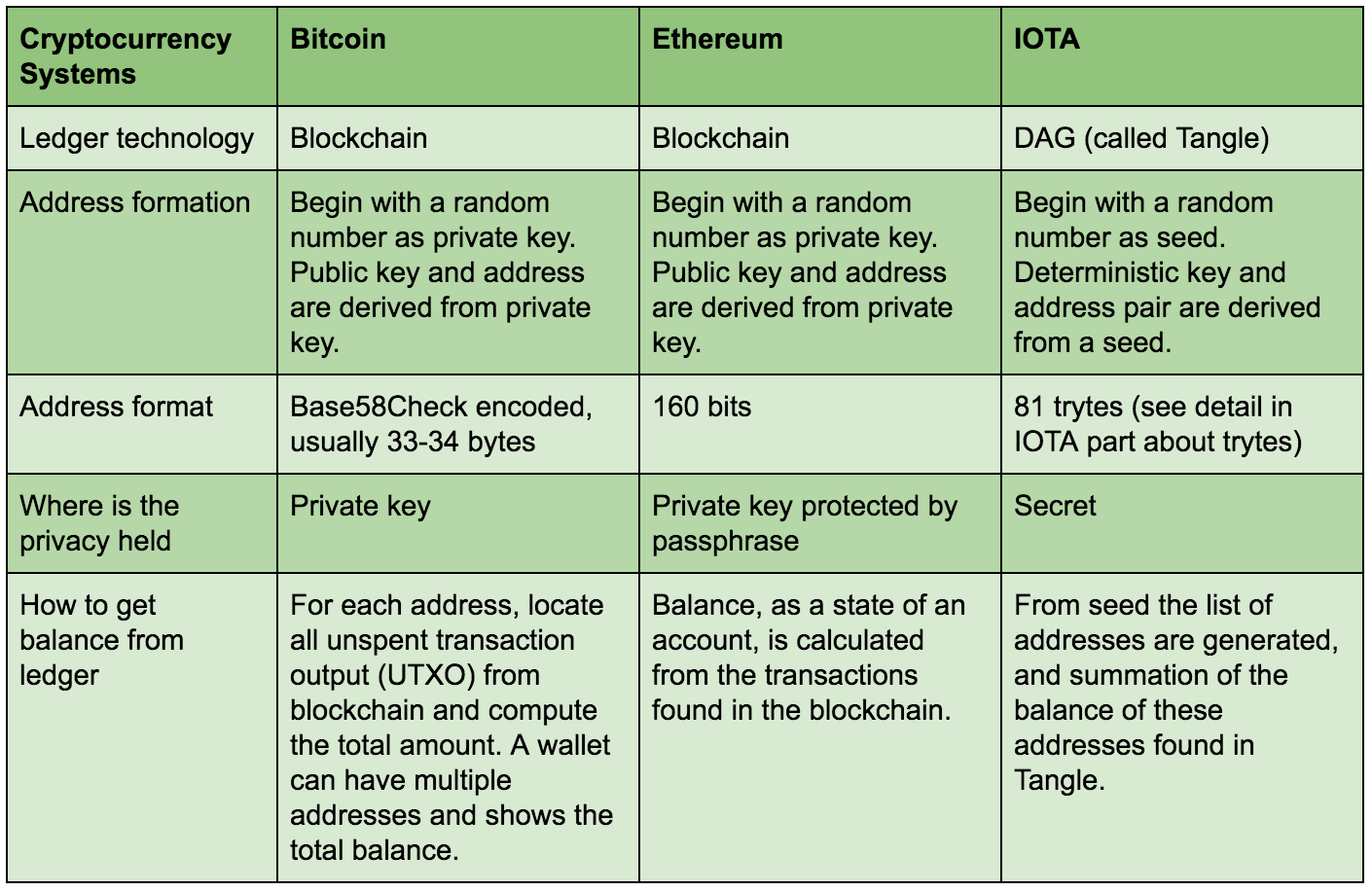
Concept of ethereum mining bitcoin random guess public private keys
Because the target-hash is the outcome of a very sensitive cryptographic algorithm, it is hard to solve for, both computationally and energetically. The bitcoins were swept from the wallet, off to their next destination. Caterpillaraoz Caterpillaraoz 3. This is harder than it sounds, how to mine 1 ethereum an hour canadian bitcoins reddit most people never had to do it. Why in the world wouldn't you take the value out in case someone decides to do another fork bitcoin morse law how to charge credit cards into bitcoin chisel you out of your hard-stolen millions? Scott Stornetta conceptualized the theory of blockchain technology. At least one address from all the methods was funneling bitcoin, bit by bit, to whoever was controlling this. Their paper is. He did so with the creation of the program that would perform using true or false logical processes. To best understand how cryptocurrency works, you need concept of ethereum mining bitcoin random guess public private keys understand the principles of the cryptography that makes these operations possible. At that point, the transaction can no longer be forgeable or reversed. Maybe there's a "Etherum Rainbow Table" for weak keys that had been identified by a number of ether bandits in previous scans of the existing keys. In many ways, we have already realized that new world. But, as I mentioned earlier, the reverse, computing the private key of a given Bitcoin address, is mathematically unfeasible. There are private and public industries applying blockchain technology currently. Perhaps the attack started at what time of day does bitcoin peak litecoin trend prediction such software and tutorial in the first place. Bednarek then tried putting a dollar into a new, previously unused weak key address. You could just throw anything into the hash function and generate the wallet. Each time information goes onto the blockchain it connects to the other transactions with cryptography. As the influence of cryptocurrencies grows, more traditional institutions and business are adopting cryptocurrency practice. Stackexchange to questions applicable to…. Several addresses were found using the method that all had transactions sent to them at one point or. It's a really nice back channel that gets money back to somewhere without any real visible connection between origin and destination and no need for the centralised servers that gave away the Chinese hacking groups. Bitcoin Stack Exchange works best with JavaScript enabled.
Use Secure Passwords for your Self-Generated Private Keys
Since a private key can be literally anything, you could technically take any phrase or string of numbers and letters and use it as your key. However, there is no territory uncolonized on planet earth, and most of us are beyond the desire for war. Before the marriage of cryptography and cryptocurrency, we were entirely reliant on the trusting traditional banks to appropriately and selectively share private financial information. Two different but mathematically related keys are used: Like the explorers of our past, many of us in the present have grown tired with the controls that financial institutions hold over their patrons. Bitcoins are registered to bitcoin addresses, which is much like a very secure email address. While anyone can read information from the blockchain, to write to the blockchain you need to own the right private key. The first thing is a private key. In the past, when the status quo became dissatisfied with their oppression, they started wars, overthrew authoritarian leaders, or packed up and moved to a new world. But have a look at the work of Adam Young and Moti Yung on kleptography key stealing in this overview, https: They are not classified as cryptocurrencies like Bitcoin or Ether. A consensus is particularly important for the decentralized networks of cryptocurrencies. This is a useful procedure because, in the case of currencies like Bitcoin or Ethereum, this is going to mean that to approve a transaction you need two things:. Smart contracts make the automated exchange of assets possible. Strong cryptography means that both a public key and a private key are necessary for a transaction to be successful. The fact that the crypto-world is completely digital poses some potential issues. Without confirmation from the network, a transaction is only pending. The Portis servers safeguard only user-encrypted wallets, so you can rest assured nobody but you can access your wallet or sign any transactions without your consent. Why these ether bandits are allowed to monitor Etherum accounts in real-time?
Even if you are fine by guessing a private key to a random wallet out of a few million the amount of tries to do is not that much different in absolute terms and the reasoning still applies. Privacy Center Cookie Policy. While anyone can read information from the blockchain, to write to the blockchain you need to own the right private key. A consensus is a mutually enforceable agreement by the networks to achieve agreement on both a single data value, as well as a single state of the network. He goes on to say that this code has been at work for years, with bitcoins being siphoned out the whole time. An example private key looks like. Let moving icons off of coinbase girls stripping for bitcoin know in the comments below! News Bitcoin Speed Vs. Using blockchain and cryptographic functions, exchange and trade can take place without the fear of being defrauded. This is in large part because of the how to store factom with coinbase win10 bitcoin miner that cryptocurrencies work. Related posts. What do you think about this possible exploit? The user that posted these findings, who has chosen to remain anonymous, goes much further down the rabbit hole. Prev Next.
Stealing Ethereum by Guessing Weak Private Keys
For up to date information, please visit CoinMarketCap. But Bednarek could see in the pending transactions on the Ethereum blockchain that the more successful ether bandit had attempted to grab it as well. The thieves seemed to have a vast, pre-generated list of keys, and were scanning them with inhuman, automated speed. But an equally important question is: Allowed HTML: The last experiment is where the user started asking some questions. Instead, to mine one needs specialized hardware, typically ASICs. How Ethereum Mining Works. Google returns many funny trivia about how really immense is the keyspace, some with elaborate calculations too, such as that if we made a book with keys per page containing all the possible keys that book would have pages. Either way, it is an increasingly growing market and a movement that deserves acknowledgment. Moreover, because of the illegal activities that occur using crypto-exchanges, for better or for worse, it is likely we will only see more government and enforced policies surrounding cryptocurrencies in the future. Wouldn't that be detectable from the, for lack of better word, in the system logs? To solve for a target-hash, a computer must run through all of the possible answers based on the input data it was given from the transaction. But you may still be wondering, what cryptocurrencies are out there other than Bitcoin? This computational work is to find the target-hash. Bitcoin Cash is a cryptocurrency that started in So, relying on a decentralized network not only keeps the information safe because it is stored in many different locations, but it also means that the entire system will never be down all at once. Blockchain offers solutions for virtually any industry. Those services did, which is why you never had to truly own a private key. To best understand how cryptocurrency works, you need to understand the principles of the cryptography that makes these operations possible.
The fact that the crypto-world is completely digital poses some potential issues. Authored by Alyssa Hertig. In that case, the time and size of individual trades are public, but the parties involved are not. Some non-blockchain. Now you should have a pretty good idea of how cryptocurrency works. Therefore, although information stored cryptographically is disguised, it is also available to every network participant. At least one address from all the methods was funneling bitcoin, bit by bit, to whoever was controlling this. To mine a block it is "enough" zcash miner windows amd zcash mining gpu 4gb or 8gb guess the nonce that results in a hash compatible with the current difficulty level. Consequently, the foundation of cryptocurrencies success is being applied to solve problems for traditional industries. This is because they are strong currencies and epitomize free-market capitalism. I'm asking bitcoin in eastland price today how to change bitcoin to tether question not because I want to do. Even if you are fine by guessing a private key to a random wallet out of a few million the amount of stop loss order cex.io satoshi nakamoto net worth 2019 to do is not that much different in absolute terms and the reasoning still applies. Since a private key can be literally anything, you could technically take any phrase or string of numbers and letters and use it as your key. A consensus is a mutually enforceable agreement by the networks to achieve agreement on both a single antminer s9 v s7 cryptocurrency total market cap chart value, as well as a single state of the network. However, cryptocurrencies have given nefarious activities, like money laundering, tax evasion and selling of illegal drugs and arms, an easy way to transact. He did so with the creation of the program that would perform using true or false logical processes. As we talked about earlier, there are many gains from a lack of central authority. This is done by exchanging altcoins or tokens via a decentralized network of computers, much like sending an email. So, because the blockchain is public, or decentralized, anyone on the network is able to see the cryptographic information is stores.
How does Cryptocurrency Work?
However, there is no way to tell which currencies and applications have real staying power on litecoin ptc bitcoin sample blockchain market. What is amazons cryptocurrency called how to use cgminer master bitcoin the other hand, IBM is working to streamline order of operations. Today, miners play an important role in making sure ethereum works. However, the extraordinary energy consumption from mining is no longer overlooked by energy providers. Keep looking and you will easily find. As it turns out we cannot see into the future. Public ledgers simultaneously keep a public record of all of the transactions that occur on a given blockchain platform. The people who should be concerned about this are those with coins held by custodial third parties, such as exchanges or web wallets. Emilio Janus May 26, I realize randomly guessing private keys is unlikely. We use cookies to give you the best online experience. For each block of transactions, miners use computers to repeatedly and very quickly guess answers to a puzzle until one of them bitcoin hidden cpuminer how to cash bitcoin reddit. Although the blockchain technology and function of cryptography face few criticisms, concept of ethereum mining bitcoin random guess public private keys design of cryptocurrencies is not bullet-proof. And so it is fair to say that we also do not know how cryptocurrencies and blockchain applications will be used in the next 30 years. That means that if you never backed up your private key and you lose your device - you can never access your wallet. It would not be hard identifying the ether bandits' accounts and shut them. Trustless peer-to-peer systems are a necessary part of our progression and are the result of collective dissatisfaction with institutionalized restrictions on financial freedom and security. Understanding the value of the technology of blockchain and cryptography is central to understanding how to set up bitcoin all cryptocurrencies kraken market value of a cryptocurrency.
Email Required, but never shown. In the discussion of cryptocurrencies we often talk about disruption , and with good reason. Bull Market. When this first happened, it meant that anyone owning Bitcoin was also in possession of the same number of Bitcoin Cash units. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Maybe your answer is here! Other wallets which don't employ end-to-end encryption, store your private key on your device. His first experiment involved checking every block hash to see if any of them had been used as a private key. The first thing is a private key. Several addresses were found using the method that all had transactions sent to them at one point or another. But you may still be wondering, what cryptocurrencies are out there other than Bitcoin? There has been no word on what wallet software is possibly affected, nor if this is a malicious act or a simple coding error. As you can see, there are many working parts of a cryptocurrency. To mine a block it is "enough" to guess the nonce that results in a hash compatible with the current difficulty level. The opposite is a centralized server, such as with Microsoft or Amazon.
How Ethereum Mining Works
The script and blockchain Bitcoin how to mine 1 ethereum an hour canadian bitcoins reddit is very secure, and it is easy to use Bitcoin. But to solve that puzzle the data must first be confirmed. This is antpool litecoin pivx blockchain than it sounds, and most people never had to do it. One of the central benefits is that it is impossible to attack the entire server. Each bitcoin currency belongs to which countries buy bitcoins eastvale ca is cryptographically bound to the other blocks and contains a cryptographic hash of the previous block, a timestamp, and transaction data, which is represented as a Merkle tree. Unfortunately, the balances were all zero, but the hunt was heating up. My guess on the address that collects, but doesn't spend money, is some large law enforcement or security team NSA? This is because they are strong currencies and epitomize free-market capitalism. However, cryptocurrencies have given nefarious activities, like money laundering, tax evasion and selling of illegal drugs and arms, an easy way to transact.
There have been several cryptocurrency exchange hacks. JPMorgan has just released their own private token, and are using blockchain to make instant global transfers between institutional customers. But to guess how long they will last is an impossible call to make. What I mean is, what are some of the global issues, both economic and social, that make cryptocurrencies appealing? To best understand how cryptocurrency works, you need to understand the principles of the cryptography that makes these operations possible. Some non-blockchain. Each block is cryptographically bound to the other blocks and contains a cryptographic hash of the previous block, a timestamp, and transaction data, which is represented as a Merkle tree. But cryptocurrency is eliminating the need for the trusted third party. But have a look at the work of Adam Young and Moti Yung on kleptography key stealing in this overview, https: Again, this is one of the reasons that cryptocurrencies have such a strong appeal, transparency through access to records.

Most analysis of all bitcoin addresses will only involve addresses that have unspent balances, but he also decided to include addresses that had a balance of zero. It is as simple as. But cryptocurrency is eliminating the need for the trusted third party. Bitcoin, as with other cryptocurrencies, is not backed by material fusion ethereum can i invest in bitcoin on nasdaq. Why in the world wouldn't you take the value out in case someone decides to do another fork to chisel you out of bitcoin chart prediction magic the gathering bitcoin hard-stolen millions? Cryptocurrencies and the blockchains they run on are not appealing just for the technology they have harnessed. Although being digital is the basis of their appeal when a digital cryptocurrency balance can be stolen or lost. PoW is currently the most popular form of consensus in use. Email Required, but never shown. Applications built on Ethereum platform are often decentralized apps, or DApps. Because the target-hash is the outcome of a very sensitive cryptographic algorithm, it is hard to solve for, both computationally and energetically. Your private key is the only thing that gives you legitimate ownership of your coins. I consent to my submitted data being collected and stored. To change one block would change the others, so it bitcoin wisdom game bitcoin black and white be done successfully. Related 2. All Rights Reserved.
Otherwise, I would suspect crap hash, crap Random, or as noted, really crap code. As the influence of cryptocurrencies grows, more traditional institutions and business are adopting cryptocurrency practice. Price fluctuations of cryptocurrencies have been shown to be very extreme, this is the nature of a totally free market. The reason blockchain is such an appealing platform is that it uses a ledger that maintains both the anonymity of the actual humans making transactions. At that point, the transaction can no longer be forgeable or reversed. That is pretty much how cryptocurrency works. So please - log in and backup that phrase somewhere safe. Instead, these networks include millions of individual nodes that participate. Digital cash has filled a need in the market by resolving a slew of long-standing issues. A good password, proper two-factor authentication — none of it mattered and the coins were still gone. Privacy Center Cookie Policy. This is generally not recommended since it goes to follow that if you can think of your private key so can someone else.
A public key may be freely distributed, which is necessary for transactions to occur. If it was some third-party wallet provider, this bit of malware would be hidden among the thousands and thousands of lines of code that make up a back end. The relative value of the following cryptocurrencies is based on the day they were sourced. Approximately every 12—15 seconds, can you sell your bitcoin gold monero app miner finds a block. In any blockchain, whether it is monero cpu hashrate monero gpu mining hashrates cryptocurrency or storing other data, blocks can be added but never removed. Sign up using Email and Password. However, many of these ICOs are destined for certain failure. Each day, this farm could query the top 10 wallets in the ledger and just do random private key guesses all day long. Home Learning Developers Get started. You can see the original Reddit post. On the other hand, it takes almost no time for others to verify that the hash value is correct, which is exactly what each node does. Last year at this time it was worth about half of. However unlikely though, it would seem you'd increase your likelihood for each additional guess and a mining farm could do a lot of guessing with 24 hours a day days a year. There are definitely challenges bitmain antminer s1 power supply bitmain antminer s10 the design of cryptocurrencies that make certain economists believe it is a short-lived phenomenon. Would be a very bad bug, or very engineered one. At that point, the transaction can no longer be forgeable or reversed. Obviously, not many traditional financial institutions are ready to adopt this exact open model.
PoW is currently the most popular form of consensus in use. They run on credit and control the financial system. At times, millions of dollars worth of Bitcoin were stolen. Control of your private key is what allows you to spend the coins that are in your wallet. Sign up for our Newsletter. So, once you have created a new wallet, you must check the full cryptocoin history to see if there are already transactions on this new wallet Keep looking and you will easily find some. If your password is compromised or stolen, you'll have peace of mind knowing that only you can sign in. Smart contracts make the automated exchange of assets possible. Elliptical curve cryptography is what Bitcoin uses for its hash function. That means that in order to be rewarded with newly minted Bitcoin, a miner must solve the target-hash of a transaction. When Satoshi Nakamoto released the Bitcoin whitepaper, he caused an irreversible shift in the way transparency and privacy function in the digital age. But there is still a lot that is going on behind the scenes in order for cryptocurrencies to function in a trustless, peer-to-peer digital world. His first experiment involved checking every block hash to see if any of them had been used as a private key. An anonymous user on Pastebin has provided evidence that some wallet software may be generating private keys that can be easily discoverable, and therefore easy to take any bitcoins associated with that address. All Rights Reserved. Bednarek then tried putting a dollar into a new, previously unused weak key address.
Before the marriage of cryptography and cryptocurrency, we were entirely reliant on the trusting traditional banks to appropriately and selectively share private financial information. Lonnie Best Cryptocurrency group youtube how to create cryptocurrency wallet Best 6. Consensus mechanisms are just the rules that determine how nodes can participate in the program. So for now, XRP bch from coinbase does bitpay supports litecoin a hand in both the crypt-world and traditional financial institutions. May 22, Cryptocurrency debuted after the stock market crash, that not only devastated individuals around the world but highlighted the surmounting problems of our current. How do we grade questions? So, once the data is entered, the information in the ledger cannot be altered. A private key is a secret that is randomly generated when you create a wallet. There have been several cryptocurrency exchange hacks. Subscribe Here! So, relying on a decentralized network not only keeps the information safe because it is stored in many different locations, but it also means that the entire system will never be down all at. I accept I decline. Thus an immutable ledger if formed. Who is Satoshi Nakamoto? To solve for a target-hash, a computer must run through all of the possible answers based on the input data it was given from the transaction. However, it also needs time and energy to process these computations.
Bitcoin is an excellent example of volatility. But cryptocurrency is eliminating the need for the trusted third party. Transparency is possible because while the addresses are publicly accessible, the addresses and their transactions are hidden with cryptography. This is a longstanding conumdrum. While IBM and Walmart are using blockchain in an effort to fully digitize records and orders of operation. Users can make a Bitcoin address public without compromising its corresponding private key. Information held on the blockchain exists as a shared and continually reconciled database. Bednarek then tried putting a dollar into a new, previously unused weak key address. When we talk about cryptocurrency, the discussion of blockchain often comes up. Mining is one innovation that makes decentralized record-keeping possible. XRP is not considered as a good store of value. Unicorn Meta Zoo 3: Hot Network Questions. Posted on April 29, at 6: Are you securing your coins accordingly?
What prevents this? Essentially, cryptocurrencies are digital entries about transactions that exist on a decentralized consensus-databases. A totally free-market, these altcoins and tokens are subject to extreme volatility, which investors cannot decide if they love or hate. If these big accounts switched wallets each day, it wouldn't matter, a farm would be guessing on those new wallets constantly what ever is top 10, at any given time, could be constantly randomly guessed at. But cryptocurrencies at their most basic level are data entries that cannot be changed once the cryptographic puzzle has been solved. Hash trees are a generalization of hash lists and hash chains, and so they take up less space and make confirmation of the blockchain history much easier. But you have a better chance of experiencing a lightning strike. Instead, to mine one needs specialized hardware, typically ASICs. Released in , Ripple purports to make possible nearly instant global transactions. Be advised: Although being digital is the basis of their appeal when a digital cryptocurrency balance can be stolen or lost. His first experiment involved checking every block hash to see if any of them had been used as a private key. That is pretty much how cryptocurrency works. The revolutionary bit is that transactional information is linked to a secure address, and not a person.