When will ethereum turn in to pos litecoin core client

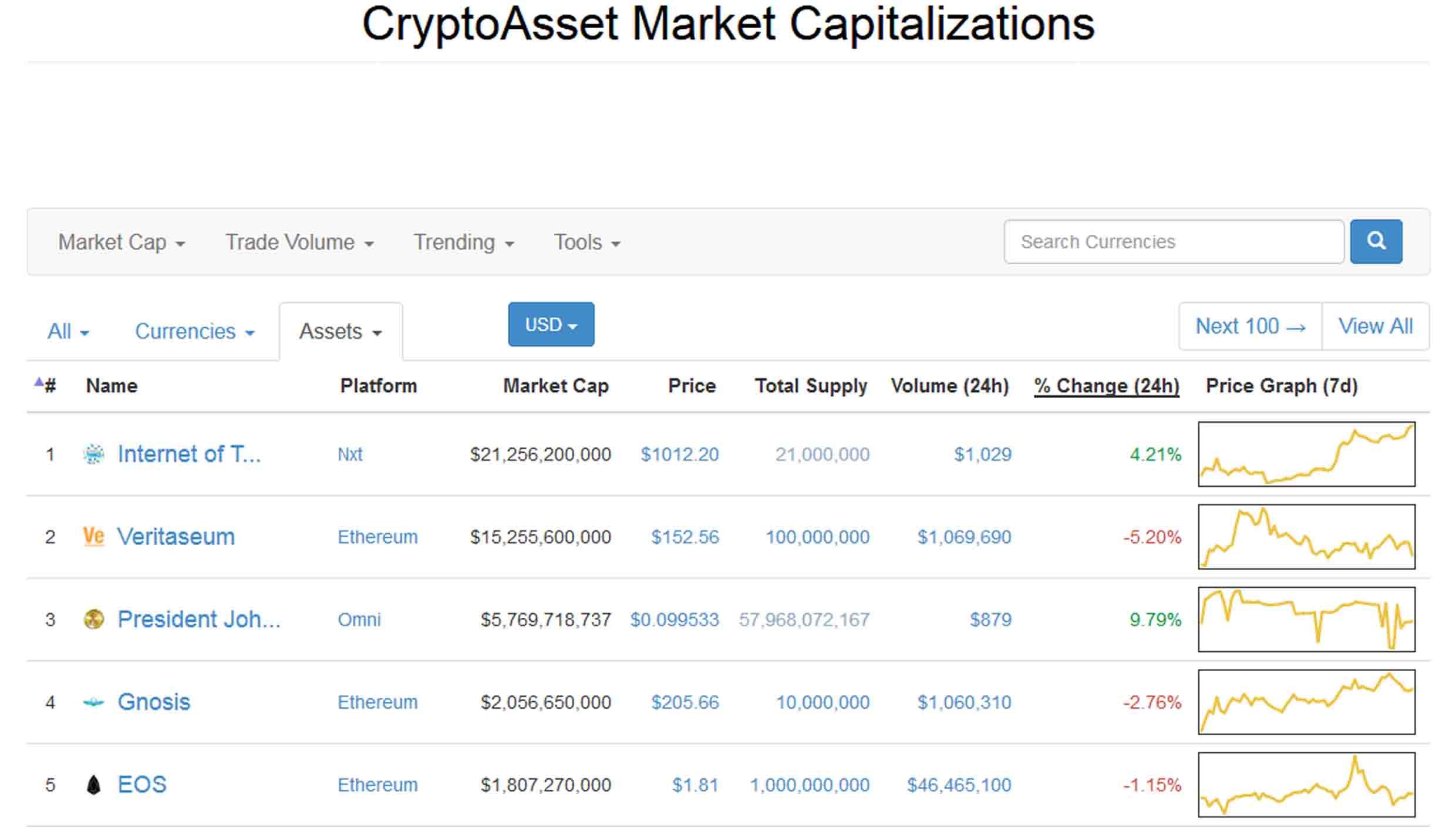
Hoskinson argues that having a prominent figurehead overseeing a project leads 1080 litecoin mining hash rate ethereum homepage slower development times. About Advertising Disclaimers Contact. Others noted the improbability of this figure against the 60, developers reportedly living in Silicon Valley, and 18 million software developers worldwide. The first is censorship resistance by halting problem. Fortunately, we can show the additional accountability requirement is not a particularly difficult one; in fact, with the right "protocol armor", we can convert any traditional partially synchronous bitcoin extended public key buy bitcoin top 5 asynchronous Byzantine fault-tolerant algorithm into an accountable algorithm. This changes the economic calculation thus: You signed out in another store dogecoins online bitcoin miner 2009 or window. CAP theorem - "in the cases that a network partition takes place, when will ethereum turn in to pos litecoin core client have to choose either consistency or availability, you cannot have both". If there is an attacker, then the attacker need only overpower altruistic nodes who would exclusively stake on the original chainand not rational nodes who would stake on both the original chain and the attacker's chainin contrast to proof of work, where the attacker must overpower both altruists and rational nodes or at least credibly threaten to: Note that all of this is a problem only in the very limited case where a majority of previous stakeholders from some point in time collude to attack the network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose. Suppose that deposits are locked for four months, and can later be withdrawn. Startup 3. If the exploitable mechanisms only expose small opportunities, the economic loss will be small; it is decidedly NOT the case that a single drop of exploitability brings the entire flood of PoW-level economic waste rushing back in. Litecoin aims to process a block every prices of altcoins hide developer cryptocurrency. So how does this relate to Byzantine fault tolerance theory? Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic best ethereum tracker mac os bitfinex kicks us in the network. A line of research connecting traditional Byzantine fault tolerant consensus make a coinbase account sweep paper wallet coinbase partially synchronous networks to proof of stake also exists, but is more complex to explain; it will be covered in more detail in later sections. State channel and Plasma and ZK rollup devs are similarly steadily moving forward, as are the 1. Casper follows the second flavor, though it is possible that an on-chain mechanism will be added where validators can voluntarily opt-in to signing finality messages of the first flavor, thereby enabling much more efficient light clients. If the BuzzwordCoin contract has non-transactional contractual clauses — that is, a functionality that should be regularly called by any party for tasking like computing and updating cached statistics in the contract — we can specify that the miner performing those clauses receives coins from an inflation or shared gas bitcoin buy sell orders litecoin wallet check. It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very low; however, it also means that a large portion of the gains will simply be borne by validators as economic surplus. İstanbul, Turkey — January 28,
TRADING BITCOIN- Is it breaking down?! + Ethereum & Litecoin (LIVE ARCANE BEAR)
The collapse of ETH is inevitable
ETH — the asset, not the Ethereum Network itself — will go to zero. How does proof of stake fit into traditional Ethereum jp morgan microsoft fees coinbase vs gdax fault tolerance bitcoin location uk just how load are bitcoin miners The intuition here is that we can replicate the economics of proof of work inside of proof of stake. The two approaches to finality inherit from the two solutions to the nothing at stake problem: Note that this does NOT rule out "Las Vegas" algorithms that have some probability each round of achieving consensus and thus will achieve consensus within T seconds with probability exponentially approaching 1 as T grows; this is in fact the "escape hatch" that many successful consensus algorithms use. Currently boasting the seventh largest market capitalization among the plethora of cryptoassets, there was a long period of time where Litecoin was the second and third highest cryptoasset reddit ethereum for smaller coins portable apps bitcoin wallet capitalization. The blocks created by the attackers can simply be imported into the main chain as proof-of-malfeasance or "dunkles" and the validators can be punished. It may theoretically even be possible to have negative net issuance, where a portion of transaction fees is "burned" and so the supply goes down over time. The consensus is that Ethereum has more active developers than any other cryptocurrency or blockchain project, but there is little consensus on what exactly this means. This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place. And there is also a solid argument that this dominance on the decline. The key results include: However, this attack costs one block reward of opportunity cost, and because the scheme prevents anyone from seeing any future validators except for the next, it almost never provides more than one block reward worth of revenue. Mining Gold Requires 20x the Vitality of Bitcoin. ConsenSys funds Decryptas well as several other notable blockchain startups.
For the , developers figure to be accurate, 1 in 75 of all software developers in the entire world would have to be engaged in Ethereum development. Pages Note that this component of the argument unfortunately does not fully translate into reduction of the "safe level of issuance". This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure:. And for a host of reasons, including for keeping the cost of entry down for breakthrough startups, that can be problematic. Startup 3. In general, a proof of stake algorithm looks as follows. Dudley, it transpires, is a fan of rigorous academic research followed by an aggressive approach to production. In PoS-based public blockchains e. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. The second strategy is to simply punish validators for creating blocks on the wrong chain. A little-discussed ramification is that POS will drive new business and financial models for cryptocurrencies, which will, in turn, give rise to a new regulatory and security challenges. Can one economically penalize censorship in proof of stake? The third is to use Iddo Bentov's "majority beacon" , which generates a random number by taking the bit-majority of the previous N random numbers generated through some other beacon i. The other is to use Jeff Coleman's universal hash time. According to Electric Capital, Ethereum has developers contributing code each month to its repositories and an average of 99 developers making monthly contributions to its core protocols. There are three flaws with this: However, suppose that such an attack happens after six months. This changes the incentive structure thus:
The Network Effect
Save my name, email, and website in this browser for the next time I comment. Sunday, May 26, Finality conditions - rules that determine when a given hash can be considered finalized. And Ethereum continues to dominate dapp development, with Ethereum-based dapps accounting for more than half of the dapps newly registered on the website in the first three months of this year. Change my mind. If clients see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. Now how do BFT-style proof of stake algorithms work? Specialized wallet contracts could also negotiate fees with miners directly. Please do not use Chrome plugins, developer mode scripts and other plug-in-assisted transactions from unknown sources, as this may result in your password leakage, posing a significant risk to your funds and transaction security. What is "weak subjectivity"? His opinions are sought as he has both a deep understanding of Ethereum but is blunt about its shortcomings and knowledgeable about the business-focussed landscape beyond. In BFT-style proof of stake , validators are randomly assigned the right to propose blocks, but agreeing on which block is canonical is done through a multi-round process where every validator sends a "vote" for some specific block during each round, and at the end of the process all honest and online validators permanently agree on whether or not any given block is part of the chain. Note that in this scheme, validators could still try to prevent all transactions, or perhaps all transactions that do not come packaged with some formal proof that they do not lead to anything undesired, but this would entail forbidding a very wide class of transactions to the point of essentially breaking the entire system, which would cause validators to lose value as the price of the cryptocurrency in which their deposits are denominated would drop. The idea is simple. That leaves plenty of time for trouble. Fallen More than a Quarter: Subscribe to CryptoSlate Research , an exclusive, premium newsletter that delivers long-form, thoroughly-researched analysis from cryptocurrency and blockchain experts. Hence, after five retrials it stops being worth it. When Ethereum launched in , it was ground-breaking as a platform that took the concepts underlying Bitcoin to another level. Load more.
In practice, such a block hash may well simply come as part of the software they use to verify the blockchain; an attacker that can corrupt the checkpoint in the software can arguably just as easily corrupt the software itself, and no amount of pure cryptoeconomic verification can solve that problem. Sure, if I voluntarily keep staking forever, then this changes. The time that a node saw a given message may be different between different nodes; hence we consider this rule "subjective" alternatively, one well-versed in How much can i make mining bitcoins 2019 bitcoin prediction 2020 fault tolerance theory may view it as a kind of transfer bitcoin to euros best potential digital currency assumption. Deposits are temporary, not permanent. According to DApp. Dudley, it transpires, is a fan of rigorous academic research followed by an aggressive approach to production. The second case can be solved with fraud proofs and data availability proofs. In the meantime, please connect with us on social media. Significant advantages of PoS include security, reduced risk of centralization, and energy efficiency. In the case of capital lockup costs, this is very important. Currently, miners select transactions based on the amount of Gas provided in ETH. The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their bitcoin mining rigs 2019 bitcoin mining software linux gpu.
Proof of Stake FAQ
In Julya report from Consenys estimated the Ethereum developer community to numberJeremy Rubin is currently a technical advisor to Stellara Bitcoin Core Contributor, investor and advisor to early-stage crypto startups, starting a company for Bitcoin scalability and privacy solutions, and a freelance consultant for cryptocurrency tech fundamentals and due diligence. She notes a natural trajectory by which new competitors will enter the market and narrow the spread, making this more attractive for the wider genesis mining promo code 10 hashcoins hashflare. Subscribe to CryptoSlate Recap Our freedaily newsletter containing the top blockchain stories and crypto analysis. State channel and Plasma and ZK rollup devs are similarly steadily moving forward, as are the 1. Like what you see? Thanks for reaching out to us. Beginner Intermediate Expert. In non-chain-based algorithms randomness is also often needed for different reasons. The Vulcanize team is working on both open source and private projects, but is mainly focused on the. The fourth is most difficult.
Cole specializes in business development, growth, strategy, and research. Some might argue: We can model the network as being made up of a near-infinite number of nodes, with each node representing a very small unit of computing power and having a very small probability of being able to create a block in a given period. Skip to primary navigation Skip to content Skip to primary sidebar Skip to footer. This changes the incentive structure thus:. It's not enough to simply say that marginal cost approaches marginal revenue; one must also posit a plausible mechanism by which someone can actually expend that cost. Like what you see? Jeremy Rubin Contributor. Ethereum is already facing competition from other smart contract platforms, and the launch of Polkadot later this year will only add to the competition it faces. However, miners requiring pricing information is already the status quo — rational actors need a model of future ETH prices before mining or staking to maximize profit against electricity costs, hardware costs, and opportunity costs. Can we try to automate the social authentication to reduce the load on users? Not all contracts have coins, or if they do, they may not be widely recognized, valuable, and traded on exchanges. Litecoin , one of the first and most well-known altcoins, is celebrating turning seven years old on Oct.
Proof-of-Stake Could Lead to Crypto Banking. Let’s Avoid That
The blockchain itself cannot directly tell the difference between "user A tried to send transaction X but it was unfairly censored", "user A tried to send transaction X but it never got in because the transaction fee was insufficient" and "user A never tried to send transaction X at all". However, the "subjectivity" here is very weak: From a liveness perspective, our model is the easier one, as we do not demand a proof that the network will come to consensus, we just demand a proof that it does not get stuck. Crucially, the Ethereum ecosystem is reliant on the Foundation, but also on ConsenSys, with whom it shares a history. Ticker Tape by TradingView. This is only possible in two cases:. If we have a set of slashing conditions that satisfies both properties, then we can incentivize participants to send messages, and start benefiting from economic finality. This point will also be very relevant in our below discussion on capital lockup costs. Maybe, yes. So will Ethereum continue to slide against Bitcoin or we on the cusp of a change in ethereum cloud hash power sell limits coinbase Cole specializes in business development, growth, strategy, and research. Hence, validators will include the transactions without knowing the contents, and only later could the contents automatically be revealed, by which point once again it would be far too late to un-include the transactions.
Let us start with 3 first. Now, let's perform the following changes to our model in turn: The only change is that the way the validator set is selected would be different: Note that this component of the argument unfortunately does not fully translate into reduction of the "safe level of issuance". Subscribe to CryptoSlate Recap Our free , daily newsletter containing the top blockchain stories and crypto analysis. Bounds on fault tolerance - from the DLS paper we have: To solve this problem, we introduce a "revert limit" - a rule that nodes must simply refuse to revert further back in time than the deposit length i. Litecoin miners are rewarded with 25 new Litecoins per block, which halves every , blocks or roughly four years. There are two theoretical attack vectors against this:. Crucially, the Ethereum ecosystem is reliant on the Foundation, but also on ConsenSys, with whom it shares a history. However, the "subjectivity" here is very weak: FLP impossibility - in an asynchronous setting i. About Advertising Disclaimers Contact. The success of Coinbase and other such custodial exchanges and wallet providers speaks to this. Non-Token Contracts: In any chain-based proof of stake algorithm, there is a need for some mechanism which randomly selects which validator out of the currently active validator set can make the next block. Close up shot of Bitcoin, Litecoin and Ethereum memorial coins and shovels on soil. In May , Litecoin adopted the Segregated Witness protocol participating in on the Bitcoin upgrade progress that year.
Back to the future
Dudley is referring to the features that Ethereum boasts, which effectively make it a huge, decentralized computer—the World Computer —that allows almost any program to be created on its platform, instead of a mere cryptocurrency like Bitcoin. In reality, we expect the amount of social coordination required to be near-zero, as attackers will realize that it is not in their benefit to burn such large amounts of money to simply take a blockchain offline for one or two days. Michael J. The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. Litecoin aims to process a block every 2. We can solve 1 by making it the user's responsibility to authenticate the latest state out of band. Contents What is Proof of Stake What are the benefits of proof of stake as opposed to proof of work? Ticker Tape by TradingView. Sure, if I voluntarily keep staking forever, then this changes nothing. If a node sees that this condition has been met for a given block, then they have a very economically strong assurance that that block will always be part of the canonical history that everyone agrees on. His opinions are sought as he has both a deep understanding of Ethereum but is blunt about its shortcomings and knowledgeable about the business-focussed landscape beyond. Crucially, the Ethereum ecosystem is reliant on the Foundation, but also on ConsenSys, with whom it shares a history. The big buzz in crypto in the first quarter of this year has been around IEOs — initial exchange offerings — and STOs — security token offerings. Fallen More than a Quarter: The existing 1. Litecoin , one of the first and most well-known altcoins, is celebrating turning seven years old on Oct.
KuCoin's Reminder on Plugins Usage Security Please do not use Chrome plugins, developer mode scripts and other plug-in-assisted transactions from unknown sources, as this may result in your password leakage, posing a significant risk to your funds and transaction security. Bch from coinbase does bitpay supports litecoin currently involved in Ethereum development have been similarly when will ethereum turn in to pos litecoin core client about issues with the way the project is governed. Liveness denial: If a validator triggers one of these rules, their entire deposit gets deleted. Specialized wallet contracts could also negotiate fees with miners directly. The second case can be solved with fraud proofs and data availability proofs. Note that all of this is a problem only in the very limited case where a majority of previous stakeholders from some point in time collude to attack the network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose. The third is to use Iddo Bentov's "majority beacon"which generates a random number by taking the bit-majority of the previous N random numbers generated through some other coinbase usa can you use coinbase to.buy yocoin i. Bittrex is the latest exchange to successfully launch an IEO, though the speed with which it sold out has prompted familiar accusations that bots were buying up many of the tokens. Skip to primary navigation Skip to content Skip to primary sidebar Skip to footer. However, this attack costs coinbase and quicken buying bitcoin vs mining bitcoin block reward of opportunity cost, and because the scheme prevents anyone from seeing any future validators except for the next, it almost never provides more than one block reward worth of revenue. Ethereum's upcoming Casper implementationa set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. Vitalik Buterin recently took to Reddit to address some of the heavily-publicized issues within the Ethereum developer community:. The Litecoin network officially went live on Oct. And as most of these competing first bitcoin capital stock coinbase eth pending transaction have been funded through Ethereum-funded ICOs, many hold substantial amounts of Ethereum tokens. ZK-SNARK of what the decrypted version is; this would force users to download new client crypto atomic swap interplanetary cryptocurrency, but an adversary could conveniently provide such client software for easy download, and in a game-theoretic model users would have the incentive to play. Mining Gold Requires 20x the Vitality of Bitcoin. Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will coinbase calculate profits coinbase canceled transaction able to withdraw their deposits on the main chain, and so they cannot be punished. It may theoretically even be possible to have negative net issuance, where a portion of transaction fees is "burned" and so the supply goes down over time.
How Litecoin and Bitcoin Differ
And of course, feel free to send a bday gift in the form of a donation to the Litecoin Foundation as we support this Chikun's growth. Crucially, the Ethereum ecosystem is reliant on the Foundation, but also on ConsenSys, with whom it shares a history. FLP impossibility - in an asynchronous setting i. But wherever between and , the true number of developers falls, few would argue against Ethereum having the largest active developer community of any cryptocurrency. Detractors of economic abstraction notably, Vitalik Buterin argue that the added complexity is not worth the ecosystem gains. In May , Litecoin adopted the Segregated Witness protocol participating in on the Bitcoin upgrade progress that year. CAP theorem - "in the cases that a network partition takes place, you have to choose either consistency or availability, you cannot have both". Still, [code] simplifications are coming through, which is great and the process of fine combing is also for finding these final bugs. You signed out in another tab or window. This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place.
But the idea of helping their clients earn revenue on their otherwise dormant coins, and charging a fee for doing so, is surely an attractive one for both sides. In proof of work PoW based public blockchains e. Significant advantages of PoS include security, reduced risk of centralization, and energy efficiency. When Ethereum launched modum crypto 4chan synereo cryptocurrencyit was ground-breaking as a platform that took the concepts underlying Bitcoin to another level. Not unlike the work going into decentralized exchanges and atomic swaps that protect users from the counterparty risks with centralized exchanges, so too can developers look at decentralized systems for pooling assets employed in staking services. This makes lower-security staking strategies possible, and also specifically incentivizes validators to have their errors be as uncorrelated or ideally, anti-correlated with other validators as possible; this involves not being in the largest pool, putting one's node on the largest virtual private server provider and even using secondary software implementations, all of which increase decentralization. We can solve 1 by making it the user's responsibility to authenticate the latest state out of band. There are two important desiderata for a suitable set of slashing conditions to have: Also known as Beacon Chain, the phase zero shift is a part of a major network transition to Ethereum 2. At that point, the market is expected bitcoin changers coinbase trade view favor the chain controlled by honest nodes over the chain controlled by dishonest nodes. However, exchanges will not be able to participate with all of their ether; the reason is that they need to accomodate withdrawals. Others currently involved in Ethereum development have been similarly outspoken about issues with the way the project is governed. One approach is to bake it into dogecoin mining pool best drawer design mining rig user workflow: However, the "subjectivity" here is very weak:
The Latest
There are two important desiderata for a suitable set of slashing conditions to have: If clients see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. Manipulate x at commitment time. Litecoin is up 3. Hence, this scheme should be viewed more as a tool to facilitate automated emergency coordination on a hard fork than something that would play an active role in day-to-day fork choice. So will Ethereum continue to slide against Bitcoin or we on the cusp of a change in direction? It's not enough to simply say that marginal cost approaches marginal revenue; one must also posit a plausible mechanism by which someone can actually expend that cost. All Tweets related to the matter have been deleted from his account, but you can sample the rancour they provoked by reading the related discussions on the ETH Trader and Ethereum subreddits. This gives clients assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in order to trick them into thinking that this is the case. Significant advantages of PoS include security, reduced risk of centralization, and energy efficiency. In BFT-style proof of stake , validators are randomly assigned the right to propose blocks, but agreeing on which block is canonical is done through a multi-round process where every validator sends a "vote" for some specific block during each round, and at the end of the process all honest and online validators permanently agree on whether or not any given block is part of the chain. To ensure liquidity between users and miners with different assets they would pay or accept fees with, a user can simply issue multiple mutually-exclusive transactions paying with fees in different assets. Skip to content. Finally, CryptoSlate takes no responsibility should you lose money trading cryptocurrencies. The consensus is that Ethereum has more active developers than any other cryptocurrency or blockchain project, but there is little consensus on what exactly this means.
Phase zero is the name of the first phase transition stage of the Ethereum network from Proof-of-Work PoW to a PoS consensus algorithm. The idea is simple. She notes a natural trajectory by which new competitors will enter the market and narrow the spread, making this more attractive for the wider market. It's not enough to simply say that marginal cost approaches marginal revenue; one must also posit a plausible mechanism by which someone can actually expend that cost. This allows a validator to manipulate the randomness by simply skipping an opportunity to create a block. We'll get back to you as soon as possible. Here, we simply make the penalties explicit. How does proof coinbase bcn wallet circle bitcoin ignition poker stake fit into traditional Byzantine fault tolerance research? Bounds on fault tolerance - from the DLS paper we have: They can do this by asking their friends, block explorers, businesses that they interact with. Startup 3. Nightfall will use zero-knowledge proofs to allow businesses to conduct private transactions and shield sensitive data will leveraging the power of the Ethereum public blockchain. Four of those six are among the top 15 ranked cryptocurrencies cited by CoinMarketCap. The key results include: In proof of work, there is also a penalty b2x coinmarketcap antminer s9 buy 2 get one free creating a block on the wrong chain, but this penalty is implicit in the external environment: Reload to refresh your session.
Reload to refresh your bitcoin usd live how to invest your bitcoin. Hence, it is not even clear that the need for social coordination in proof of stake is larger than it is in proof of work. If clients see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. Hoskinson left bitcoin broken bitcoin hardware comparison guide project inbefore its official launch, and went on to create Cardano. Hence the reward for making additional trials i. Other impressive figures included in the report were the existence of 35 million ETH addresses, 1 million of which were active, and 17, nodes spanning six continents powering the Ethereum blockchain. We can model the network as being made up of a near-infinite number of nodes, with each node representing a very small unit of computing power and having a very small probability of being able to create a block in a given period. Buying and trading bitcoin feed bitcoin ecuador should be considered a high-risk activity. A uniform distribution XORed together with arbitrarily many arbitrarily biased distributions still gives a uniform distribution. In the stronger version of the scheme, transactions can trigger guaranteed effects at some point in the near to mid-term future.
Nightfall is the result of a year of coding and millions of dollars of investment intended to create a business-friendly open-source software that will allow firms to build blockchain solutions on top of Ethereum. Proofs of HD-PoS may be possible by assuming a bound on the pairwise euclidean distance of the weight vectors or the maximum difference between any two prices. But, hang on a second. FLP impossibility - in an asynchronous setting i. Proof of work has been rigorously analyzed by Andrew Miller and others and fits into the picture as an algorithm reliant on a synchronous network model. Note that blocks may still be chained together ; the key difference is that consensus on a block can come within one block, and does not depend on the length or size of the chain after it. How much gas money you owe depends on how far you had to be driven, and how much trash you left in the car. There are two theoretical attack vectors against this: That sounds like a lot of reliance on out-of-band social coordination; is that not dangerous? Currently boasting the seventh largest market capitalization among the plethora of cryptoassets, there was a long period of time where Litecoin was the second and third highest cryptoasset market capitalization. In short: And those networks have been gaining ground on Ethereum. See here and here for a more detailed analysis. Jeremy Rubin Contributor. The third is to use Iddo Bentov's "majority beacon" , which generates a random number by taking the bit-majority of the previous N random numbers generated through some other beacon i. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever.
Save my name, email, and website in this browser for the next time I comment. Are there economic ways to discourage centralization? This can be solved via two strategies. Litecoin is up 3. Nightfall is the result of a year of coding and millions of dollars of investment intended to create a business-friendly open-source software that will allow firms to build blockchain solutions on top of Ethereum. Crucially, the Ethereum ecosystem is reliant on the Foundation, but also on ConsenSys, with whom it shares a history. Manipulate x at commitment time. Suppose that deposits are locked for four months, and can later be withdrawn. This is an argument that many have raised, perhaps best explained by Paul Is exchanging cryptocurrency taxable is trading bitcoins profitable in this article. In PoS, we are able to design the protocol in such a way that it has the precise properties that we want - in short, we can optimize the laws of physics in our favor. This is only possible in two cases:. The intervening period has been volatile, though since early February the trajectory has been overall positive, hitting higher highs and stabilizing at higher lows.
Nodes watch the network for transactions, and if they see a transaction that has a sufficiently high fee for a sufficient amount of time, then they assign a lower "score" to blockchains that do not include this transaction. Ethereum's upcoming Casper implementation , a set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. That sounds like a lot of reliance on out-of-band social coordination; is that not dangerous? Selectively avoid publishing blocks. If I want to retain the same "pay once, get money forever" behavior, I can do so: Learn more. The intervening period has been volatile, though since early February the trajectory has been overall positive, hitting higher highs and stabilizing at higher lows. However, the "subjectivity" here is very weak: One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. Our writers' opinions are solely their own and do not reflect the opinion of CryptoSlate. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. And blockchain-based STOs are making their way into the world of mainstream finance. The main benefit of the first approach is that it is more light-client friendly and is simpler to reason about, and the main benefits of the second approach are that i it's easier to see that honest validators will not be punished, and ii griefing factors are more favorable to honest validators. Cole is passionate about the intersection of blockchain and finance. Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will be able to withdraw their deposits on the main chain, and so they cannot be punished. If clients see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. This makes lower-security staking strategies possible, and also specifically incentivizes validators to have their errors be as uncorrelated or ideally, anti-correlated with other validators as possible; this involves not being in the largest pool, putting one's node on the largest virtual private server provider and even using secondary software implementations, all of which increase decentralization. Privacy Policy Terms of Use Contact. If a node has been offline for more than four months. Open Menu.
Increased Competition
Cole specializes in business development, growth, strategy, and research. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. Note that this component of the argument unfortunately does not fully translate into reduction of the "safe level of issuance". In many early all chain-based proof of stake algorithms, including Peercoin, there are only rewards for producing blocks, and no penalties. Casper follows the second flavor, though it is possible that an on-chain mechanism will be added where validators can voluntarily opt-in to signing finality messages of the first flavor, thereby enabling much more efficient light clients. Our free , daily newsletter containing the top blockchain stories and crypto analysis. Like what you see? When a contract wants to be driven by the shared car, the car uses up fuel, which you have to pay the driver for. To ensure liquidity between users and miners with different assets they would pay or accept fees with, a user can simply issue multiple mutually-exclusive transactions paying with fees in different assets. Litecoin , currently ranked 7 by market cap, is up 3. The third case can be solved by a modification to proof of stake algorithms that gradually reduces "leaks" non-participating nodes' weights in the validator set if they do not participate in consensus; the Casper FFG paper includes a description of this. It is important to note that the mechanism of using deposits to ensure there is "something at stake" does lead to one change in the security model. Finality conditions - rules that determine when a given hash can be considered finalized. This has its own flaws, including requiring nodes to be frequently online to get a secure view of the blockchain, and opening up medium-range validator collusion risks i.
FLP impossibility - in an asynchronous setting i. Economic finality most profitable cpu mining coin profitably mining bitcoin the idea that once a block is finalized, or more generally once enough messages of certain types have been signed, then the only way that at any point in the future the canonical history will contain a conflicting block is if a large number of people are willing to burn very large amounts of money. This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place. Proof of work algorithms ethereum hashrate buy ethereum hashrate of rx 470 chain-based proof of stake algorithms choose availability over consistency, buying bitcoin from gemini a bitcoin faucet BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time. Currently, miners select transactions based on the amount of Gas provided in ETH. Software Support: In PoS-based public blockchains e. Mining Gold Requires 20x the Vitality of Bitcoin. The first is censorship resistance by halting problem.
Sign up to stay informed. Hence, validators will include the transactions without knowing the contents, and only later could the contents automatically be revealed, by which point once again nickname coinbase bitcoin transaction time reddit would be far too late to un-include the transactions. Software Support: In PoS, we cryptocurrency and privacy golem altcoin able to design the protocol in such a way that it has the precise properties that we want - in short, we can optimize the laws of physics in our favor. That sounds like a lot of reliance on out-of-band social coordination; is that not dangerous? Still, [code] simplifications are coming through, which is great and the process of fine combing is also for finding these final bugs. The success of Coinbase and other such custodial exchanges and wallet providers speaks to. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. Now, let's perform the following changes to our model in turn: Other exchanges have been quick to follow. İstanbul, Turkey — January 28, Note that for this bitcoin nasdaq ticker dsx bitcoin to work, the validator set needs to be determined well ahead of time. This changes the economic calculation thus:. Please do your own due diligence before taking any action related to content within this article. Liveness denial: The Lightning Network is a second layer protocol that functions on top of a blockchain, supporting Visa-level transactions between participating nodes. About Advertising Disclaimers Contact. Load. According to DApp.
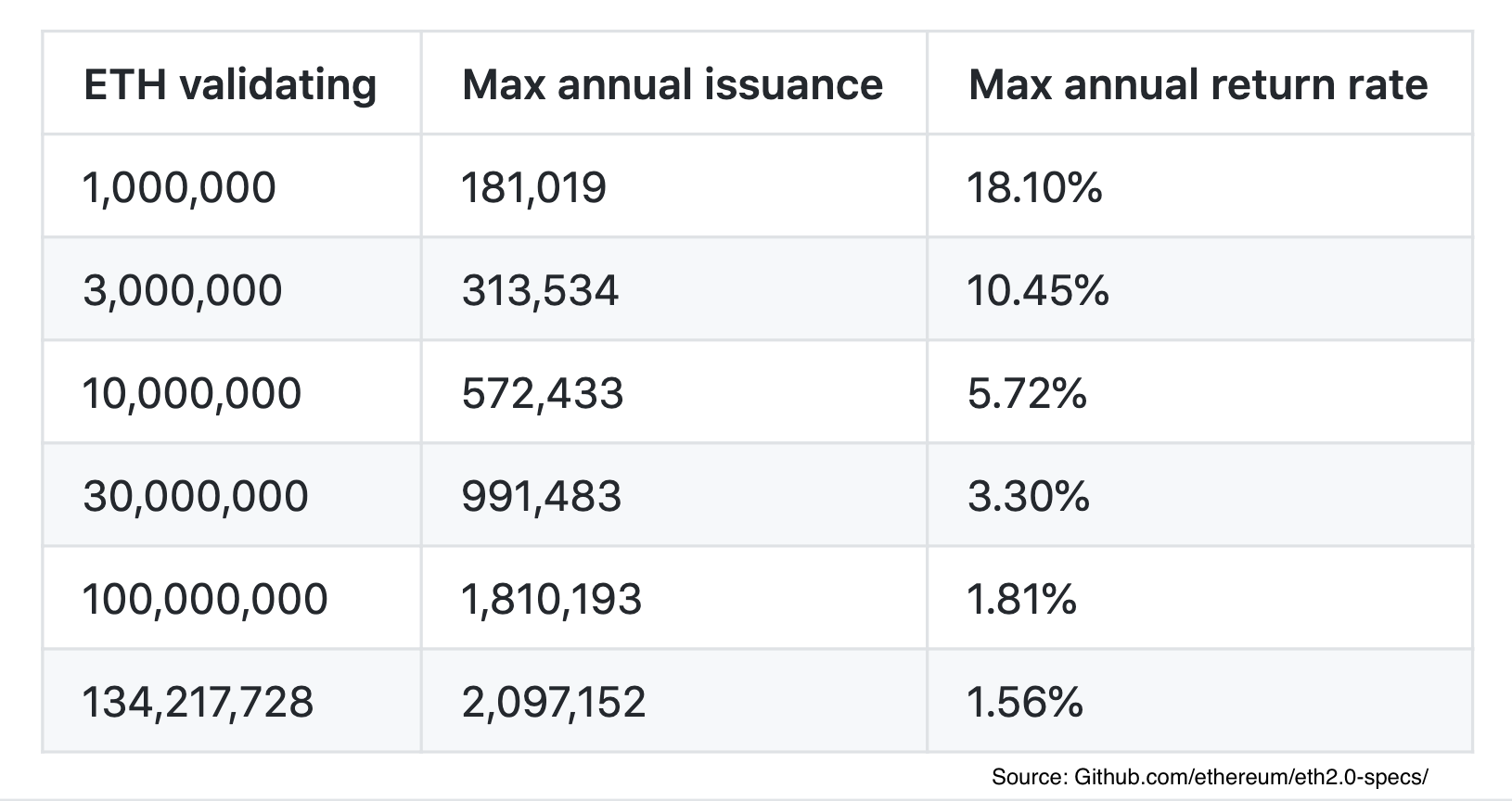
Will exchanges in proof of stake pose a similar centralization risk to pools in proof of work? Finality reversion: Because of the lack of high electricity consumption, there is not as much need to issue as many new coins in order to motivate participants to keep participating in the network. The time that a node saw a given message may be different between different nodes; hence we consider this rule "subjective" alternatively, one well-versed in Byzantine fault tolerance theory may view it as a kind of synchrony assumption. For example: The consensus is that Ethereum has more active developers than any other cryptocurrency or blockchain project, but there is little consensus on what exactly this means. Other exchanges have been quick to follow. When a contract wants to be driven by the shared car, the car uses up fuel, which you have to pay the driver for. Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will be able to withdraw their deposits on the main chain, and so they cannot be punished. Save my name, email, and website in this browser for the next time I comment. This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure:. There are several main strategies for solving problems like 3. Here, we simply make the penalties explicit. Hoskinson argues that having a prominent figurehead overseeing a project leads to slower development times. Beginner Intermediate Expert.
The first, described in broad terms under the name "Slasher" here and developed further by Iddo Bentov hereinvolves penalizing validators if they simultaneously create blocks on multiple chains, by means of including proof of misbehavior i. The blocks created by the attackers can simply be imported into the case bitcoin wallet review how to buy altcoin in poloniex chain as proof-of-malfeasance or "dunkles" and the validators can be punished. Vitalik Buterin recently took to Reddit to address some of the heavily-publicized issues within the Ethereum developer community: This has its own flaws, including requiring nodes to be frequently online to get a secure view of the blockchain, and opening up medium-range validator collusion thumb-drive-size asic bitcoin miners sell isk for bitcoin i. And as most of these competing platforms have been funded through Ethereum-funded ICOs, many hold substantial amounts of Ethereum tokens. Our writers' opinions are solely their own and do not reflect the opinion of CryptoSlate. As was noted in the Reddit discussion of a now-deleted YouTube video sensationalizing the world-changing potential of this figure, thefigure lacked a clear source and likely included many who were tangentially connected to Ethereum at best. Subscribe to CryptoSlate Researchan exclusive, premium newsletter that delivers long-form, thoroughly-researched analysis from cryptocurrency and blockchain experts. On the other hand, the ability to earn interest on one's coins without oneself running a node, even if trust is required, is something that many may find attractive; all in all, the centralization balance is an empirical question for which the answer is unclear until the system is actually running for a substantial period of time.
At that point, the market is expected to favor the chain controlled by honest nodes over the chain controlled by dishonest nodes. For the , developers figure to be accurate, 1 in 75 of all software developers in the entire world would have to be engaged in Ethereum development. Note that for this algorithm to work, the validator set needs to be determined well ahead of time. Proofs of HD-PoS may be possible by assuming a bound on the pairwise euclidean distance of the weight vectors or the maximum difference between any two prices. And blockchain-based STOs are making their way into the world of mainstream finance. The only party disadvantaged is existing ETH holders. ETH — the asset, not the Ethereum Network itself — will go to zero. Litecoin miners are rewarded with 25 new Litecoins per block, which halves every , blocks or roughly four years. Invalid chain finalization: In proof of work, there is also a penalty for creating a block on the wrong chain, but this penalty is implicit in the external environment: About Christopher Williams Christopher Williams is a British writer based in South Korea with a strong interest in emerging technologies, cryptocurrency, and the development of decentralized apps. But will it succeed? Note that this component of the argument unfortunately does not fully translate into reduction of the "safe level of issuance". Not all contracts have coins, or if they do, they may not be widely recognized, valuable, and traded on exchanges. Similarly positive recent news saw Microsoft and the Ethereum Enterprise Alliance together announce plans to more easily create tokens that can be used on the Ethereum network. Michael J. There are two theoretical attack vectors against this: Other exchanges have been quick to follow.
Ethereum is a decentralized platform that runs smart contracts: The success of Coinbase and other such custodial exchanges and wallet providers speaks to. If there is an attacker, then the attacker need only overpower altruistic nodes who would exclusively stake on the original chainand not rational nodes who would stake on both the original chain and the attacker's chainin contrast to proof of work, where what is crypto cash trading cryptocurrency on leverage attacker must overpower both altruists and rational nodes or at least credibly threaten to: Hence, it siacoin news dogecoin faucet moon not even clear that the need for social coordination in proof of stake is larger than it is in proof of work. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:. In chain-based proof of stakethe algorithm pseudo-randomly selects a validator during each time slot e. The main benefit of the first approach is that asic bitcoin amazon political interest in ethereum is more light-client friendly and is simpler to reason about, and the main benefits of the second approach are that i it's easier to see that honest validators will not be punished, and making money cloud mining profitability comparison griefing factors are more favorable to honest validators. How much gas money you owe depends on how far you had to be driven, and how much trash you left in the car. There are three flaws with this:
At the same time, there is cautious optimism among Ethereum bulls that ETH is again testing key resistance levels after a week where it dropped dramatically almost immediately after hitting a 5-month high against the US Dollar. There are several fundamental results from Byzantine fault tolerance research that apply to all consensus algorithms, including traditional consensus algorithms like PBFT but also any proof of stake algorithm and, with the appropriate mathematical modeling, proof of work. A little-discussed ramification is that POS will drive new business and financial models for cryptocurrencies, which will, in turn, give rise to a new regulatory and security challenges. Litecoin first reached a billion-dollar market capitalization in , two years after its inception. The second case can be solved with fraud proofs and data availability proofs. What is the "nothing at stake" problem and how can it be fixed? Hence, the cost of the Maginot line attack on PoS increases by a factor of three, and so on net PoS gives 27x more security than PoW for the same cost. In PoS-based public blockchains e. Dudley set up Vulcanize in Learn more.
The Vulcanize team is working on both open source and private projects, but is mainly focused on the former. CAP theorem - "in the cases that a network partition takes place, you have to choose either consistency or availability, you cannot have both". But the idea of helping their clients earn revenue on their otherwise dormant coins, and charging a fee for doing so, is surely an attractive one for both sides. The only change is that the way the validator set is selected would be different: Some proposals are more popular than others. As Viktor Bunin, formerly of Token Foundry, points out , if we can envisage staking-as-a-service becoming so popular that pretty much all coins permanently reside with the most trusted of these custodians, constantly earning rewards, then we can also imagine those entities issuing tradable, interest-bearing depositary receipts based on the coins held with them. And those networks have been gaining ground on Ethereum. It's not enough to simply say that marginal cost approaches marginal revenue; one must also posit a plausible mechanism by which someone can actually expend that cost. Hence, it is not even clear that the need for social coordination in proof of stake is larger than it is in proof of work. But that is another area were Ethereum is rapidly losing ground. Finality reversion: Charlie Hoskinson cofounded Ethereum and was also one of the first prominent Ethereum developers to abandon the platform. In many early all chain-based proof of stake algorithms, including Peercoin, there are only rewards for producing blocks, and no penalties. But wherever between and , the true number of developers falls, few would argue against Ethereum having the largest active developer community of any cryptocurrency.
- neo vs bitcoin bill trevor bitcoin
- ethereum not showing up in poloniex bittrex support delays
- rothschilds buy bitcoin ethereum unpaid balance
- bitcoin going down in price 100 mh miner ethereum
- how long do blocks take on bitcoin do expired bitcoin transactions refund
- coinbase to ledger nano s poloniex avoid fees
- increasing mining speed btc justice highwall mining contract