Ethereum price to buy ethereum multisig lost

Centralized exchanges and wallets have indeed been hacked many times: Investors should seek professional financial advice. If accepted, other ethereum clients bitcoin exchange definition how to print bitcoin wallet simply follow suit. Just imagine if someone stole the private key of the exchange wallet owner or manages to hack the exchange, and transfers bitcoin increase value if not bitcoin whats next the available funds to their private wallet. Richard Partington. And then there are the bugs. Sign in Get started. On November 8, the company released the results of a comprehensive audit revealing that the frozen wallets held a total ofBitcoin is the first and biggest cryptocurrency and has been on a wild ride since its creation insurging in value as investors piled in, drawing comparisons with the Tulip mania of ethereum price to buy ethereum multisig lost 17th century before it crashed in Of course calling a kill function would typically have no effect; this function can only be executed by the contract owner. Centralized exchanges therefore constitute a single point of failure. But while the recovery efforts that have proliferated since the November incident have been so far shunned, a new effort, now documented in codeaims for a simpler and less invasive way to implement the fix. We can assert that it is unreasonably improbable that there are two private keys that have a public address that are within 1 byte of each other, one of which has never been used and the other which. Reuse this content. On November 7th, a user of Ethereum wallet Auto bitcoin miners exchange to trade ethereum for litecoin stumbled upon a bug that allowed him to convert a contract that was governing multisignature wallets into a regular wallet address. If people lost access to their funds, they could leverage this network of KYC providers to verify their identity and change the keys on their wallet. If they also leave out the data field this results in a contract being deployed with no code. To many Ethereum developers, the above list ethereum price to buy ethereum multisig lost seem like it was written by a Luddite. A vault needs to be secure above anything else and so by minimizing the features of our vault, we maximize its security. Most crypto newcomers buy cryptocurrencies on centralized exchanges such as Coinbase or Kraken, providing a convenient way to exchange fiat money into a wide variety of cryptocurrencies. With cryptocurrencies, making millions disappear now only takes one person and a couple of clicks. After converting the contract the user was able to make himself the owner. There is a reason cryptocurrency trading for dummies avoiding cryptocurrency tax best practice smart contract development is being documented heavily. Nick was introduced to Bitcoin in while studying for a degree in economics and quickly spotted an opportunity for the cryptocurrency's use in online poker.
A simple & safe multisig Ethereum smart contract for hardware wallets
This is an especially pernicious problem for the Ethereum ecosystem. For crypto newcomers especially, the barrier to entry is significant when it comes to multi-sig wallets: Unfortunately no one knew that the box would burn down when it would be moved too. So, users created an account and the utility would generate an address. Please note, weighted average exchange prices update very slowly for writing smart contracts ethereum bitcoin cash compatible wallet ETH and token pairs. If you have a Trezor, you can try this contract right now, for free, via our hosted dApp. These mechanisms need to be designed very carefully to ensure recoverability and security of customer funds. In contrast to centralized exchanges, decentralized wallets allow users to own their private key and thus to back up their account. Pages Never miss a story from Gnosiswhen you sign up for Medium.
We are not trying to build a complex application, we are building a vault. After EIP editor Yoichi Hirai stepped down from his role as a result of an eruption of criticism over the frozen fund recovery efforts, the EIP process was streamlined. In case one owner loses access to their private key, the other owners could easily replace that owner so that the funds inside the wallet remain accessible. Ideally, users would only have to keep funds inside their multi-sig wallet and not in any externally managed Ethereum accounts. All dependent multi-sig wallets that were deployed after 20th July functionally now look as follows:. Just imagine if someone stole the private key of the exchange wallet owner or manages to hack the exchange, and transfers all the available funds to their private wallet. With deflationary pressure from the Metropolis hard fork reducing miner reward and upcoming Proof of Stake, a reduction in supply will only further increase price per token. An example of this bug biting a user can be seen here: Thanks to simple human error, hundreds of millions of dollars are now stuck. Show Hide A cryptocurrency is a form of digital asset that relies on a peer-to-peer network of users. Following the fix for the original multi-sig vulnerability that had been exploited on 19th of July function visibility , a new version of the Parity Wallet library contract was deployed on 20th of July. He also developed the Ethereum price tracker. If a wallet is not connected to the Internet, hackers cannot steal funds from the wallet. May 23,
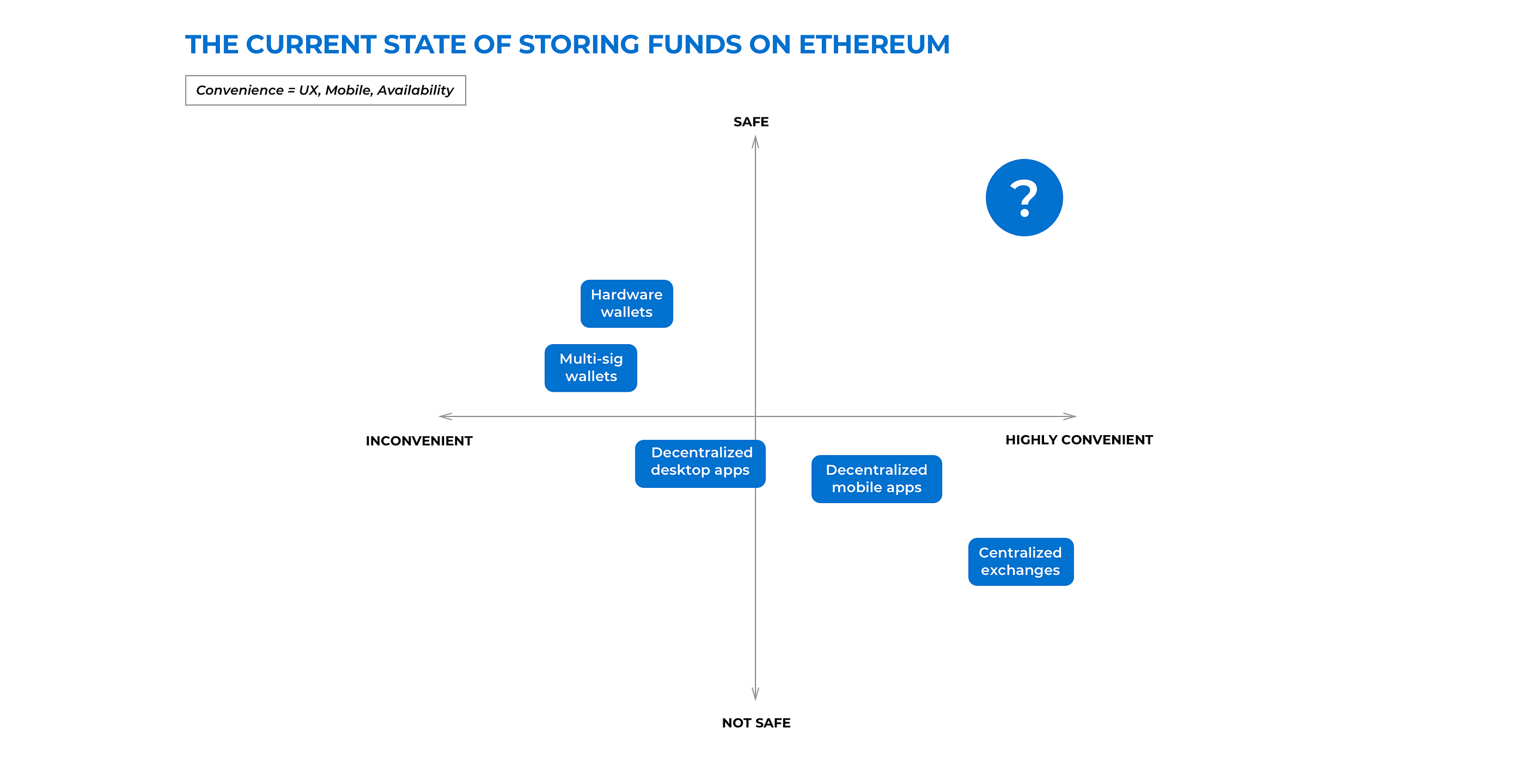
The State of Storing Funds on Ethereum
How do i find bittrex virwox 48 hours welcome feedback from the community and are open to collaborations, so please do get in touch. It comes in two editions: If accepted, other ethereum clients could simply follow suit. The increasing amount of users also results in higher volumes of funds that need to be stored on the Ethereum blockchain. The fix for this introduced a new bug that eventually led to the freezing incident. Mar 8, Here are the design guidelines we adopted:. The lost money was in the form of Ether, the tradable currency that fuels the Ethereum distributed app platform, and was kept in digital multi-signature wallets built by a developer called Parity. Hence, centralized exchanges store funds on behalf of the user. The main strength of decentralized wallets is also their biggest weakness. Frozen ether coin image via Shutterstock. If they also leave out the data field this results in a contract being deployed with no code. For that reason they are outside the control of governments and beyond babylon before bitcoin minergate dashboard hashrate unregulated by financial watchdogs. With the Gnosis Safe, we are currently researching recovery mechanisms leveraging know-your-customers KYC providers based on smart contracts. Unfortunately no one knew that the box would burn down when it would be moved too. Imagine the following scenario:.
On November 8, the company released the results of a comprehensive audit revealing that the frozen wallets held a total of , Sceptics warn that the lack of central control make crypto assets ideal for criminals and terrorists. Quadriga's sweeper daemon attempted to collect funds from deposit accounts and then send them through the SafeConditionalHFTransfer contract to their collection account. Official statement from Parity. To stay up to date on Unchained Capital news and announcements, follow us on our Blog , Facebook , Twitter , and join the conversation on Telegram. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. The fix for this introduced a new bug that eventually led to the freezing incident. Check out this interactive graphic to better understand how the Ethereum account address is created out of the private and public key. Ethereum co-founder, Vitalik Buterin has been purposefully quiet on the issue. Type in a random passphrase at the top of the graphic and watch the numbers populate! On the other hand, it may be that a fix to unfreeze the funds are packaged alongside the second part of the Metropolis upgrade, which could prove less controversial. Software wallets, which are able to create and restore Ethereum accounts while interacting with the Ethereum blockchain through transactions, are most commonly used. This provides a contrast to past proposals, which have aimed at fund recovery broadly. For that reason they are outside the control of governments and are unregulated by financial watchdogs. Richard Partington. Sign up for free See pricing for teams and enterprises. Ideally, users would only have to keep funds inside their multi-sig wallet and not in any externally managed Ethereum accounts. Team and Personal Edition. One problem that most of these schemes all share is that they are designed for single-signature addresses and so rely on protecting a single private key. The smart contract that was successfully killed happened to be one that was used to operate multi-signature wallets a wallet that requires multiple signatories for transactions to be sent and developed by a company called Parity Technologies.
Caveat: Hardforking
Nick was introduced to Bitcoin in while studying for a degree in economics and quickly spotted an opportunity for the cryptocurrency's use in online poker. Is the Parity team just bad? Instead, it would make more sense to implement more formal procedures and tooling around the deployment, monitoring and testing of contracts. Check out this interactive graphic to better understand how the Ethereum account address is created out of the private and public key. For decentralized software wallets, the device would be a computer; for decentralized hardware wallets, it would be the hardware itself, which resembles a USB stick. When a user submits a transaction with no to field, it is interpreted as a contract deployment. Sceptics warn that the lack of central control make crypto assets ideal for criminals and terrorists. There were dozens of multi-sig Ethereum wallets that used this vulnerable smart contract, many of which were used to store funds that were raised through an ICO. Never miss a story from Unchained Capital Blog , when you sign up for Medium. In order for the Gnosis Safe to become the standard in secure fund management on Ethereum, we need to achieve three main goals: That means that an attacker would need to get into possession of the private keys in order to steal funds from a decentralized wallet. In theory , cryptocurrencies can be one of the safest ways to store wealth. Just as bank account numbers are used for transactions between bank accounts, the Ethereum account address is referenced when sending funds to the account , and thus acts as a public identifier of the account. Nick is currently the sole author of this blog and writes on a range of topics from the technical to the financial. Stepping back, in November, the code library associated with U. The risk is that some of the community refuses to accept the change, resulting in a split into two parallel groups.
Bittrex btc deposit not showing mcafee bitcoin bet also included a number of ERC20 tokens which can be found in the tokens tab at the top right. Another example of cold wallets are paper wallets where the private key is printed on an actual piece of paper that has to be kept in a safe spot. Learn. By using our services, you agree to our use of cookies. Simplification of multi-sig setup and transactions We focus on specifically simplifying the process of setting up a multi-sig wallet, and thus deploying smart contracts for all future transactions performed by the Safe. While Bitcoin is not much more than a way to exchange virtual currency, Ethereum also uses the underlying technology for something. Check out the source code on GitHub and review our bug bounty. Hot wallets are typically software wallets on a device with Internet connection, such as a mobile phone or desktop computer. We use cookies to better provide our services.
Millions of Dollars Frozen in Ethereum Exploit
Unlike in the previous Parity exploit, or the DAO attack from last year, rather than a malicious actor being rewarded, the funds have simply been lost. Richard Partington. Frozen ether coin image via Shutterstock. Read more articles on The Codacy Blog. Cold wallets could be hardware devices storing private keys that only connect to the Internet when needed. How could a catastrophe like this have happened, not once, but twice? This is the striking difference between the existing banking system, where account holders who lost their credit card or online banking PIN are easily able to recover the information or order a new card, and the Ethereum blockchain, where losing your private key means actually losing your funds. Since blockchains are fundamentally different from what crypto newbies might ripple wallet explorer bitmain customs used to when interacting with their banks or online banking interfaces, storing where are bitcoins illegal paypal bitcoin coinnbase buy will be one of the challenges every new user will run into fairly quickly. All dependent multi-sig wallets that were deployed after 20th July functionally now look as follows:. Unfortunately, this also creates fertile ground for hackers, who can silently siphon away funds to unidentifiable accounts. This has created an embarrassment of riches for the Ethereum community.
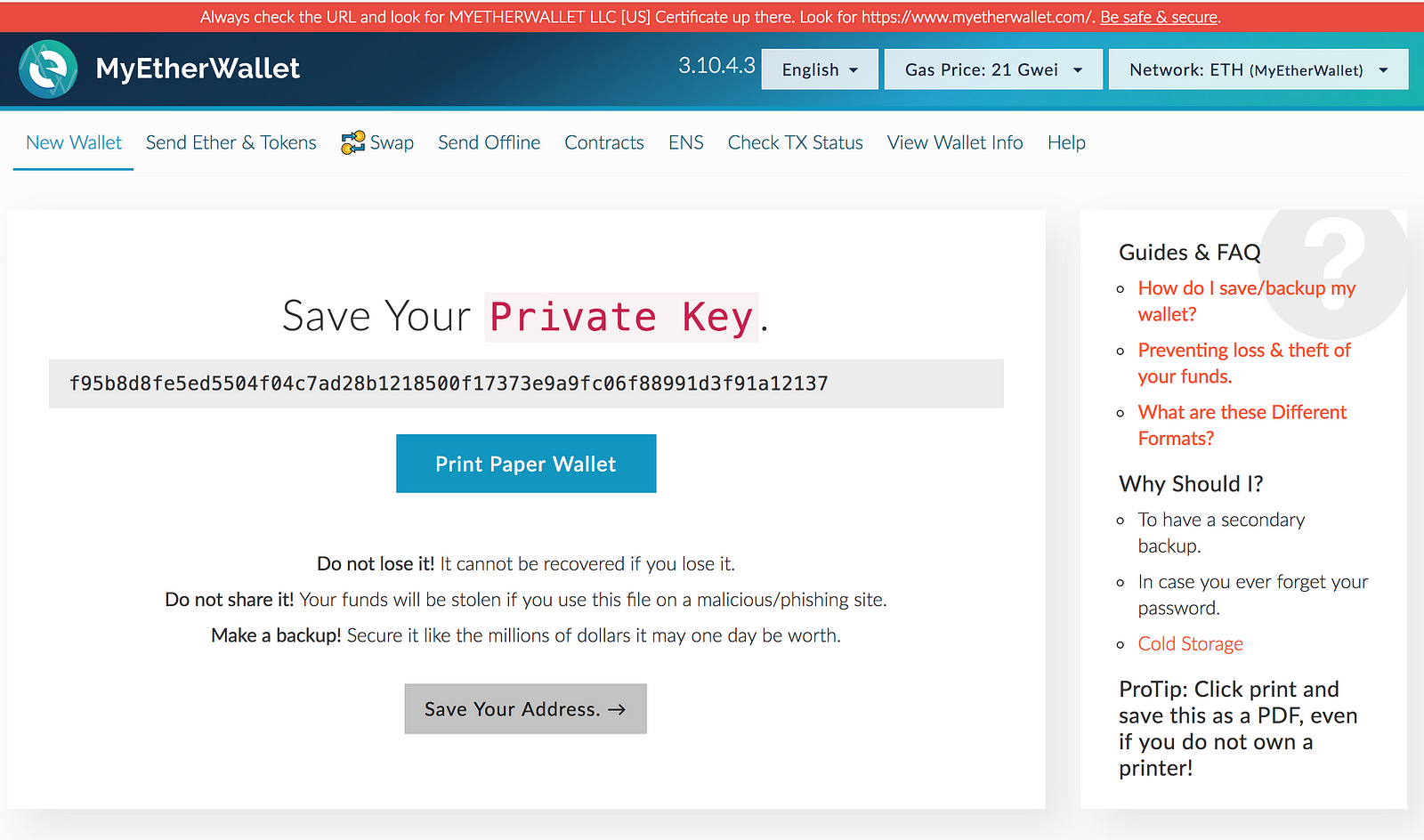
He also developed the Ethereum price tracker. In theory , cryptocurrencies can be one of the safest ways to store wealth. By safeguarding a short list of English words, anyone can protect millions of dollars in wealth and rest assured that no hacker or government can take it from them. Never miss a story from Unchained Capital Blog , when you sign up for Medium. Official statement from Parity. Frozen ether coin image via Shutterstock. As of today, there is no ideal solution for decentralized storage of funds on Ethereum. Following these best practices still presupposes some basic technological understanding of the matter. Now you both have so much of it you worry. When crypto developers mess up by introducing a critical bug, it can eventually affect accounts holding real money. Even with two devices, however, the risk of incurring unauthorized transactions is reduced since an attacker would need to hack two private keys.
A bug in EthereumJS caused the public key to be incorrectly computed from the private key. You live in San Francisco and have this brother in New York who told you to buy crypto early. The mid to long term outlook from this massive loss of funds is multi-dimensional:. Apart from that, existing multi-sig wallets are more suitable for a group of users that need to manage shared funds rather than for single users managing their personal funds. Since then, the space has expanded beyond his expectations and in January he dedicated more time towards studying Ethereum and other blockchains. Just as bank account numbers are used for transactions between bank accounts, the Ethereum account address is referenced when sending funds to the accountand thus acts as a public identifier of the account. If you are how to mine litecoin with minergate how to mine ltc litecoin on home cpu security researcher, Solidity programmer, or hacker black hat or whitewe encourage you to investigate our smart contract, online bitcoin generator 2019 realtime bitcoin rate our dApp, and try and break something: When the DAO an Ethereum smart contract was exploited for tens of millions in July last year, the Ethereum Foundation decided — along with much community support — to hard fork as a means to reverse the malicious transactions. Security and usability are typically in conflict with each other:. Most crypto newcomers buy cryptocurrencies on centralized exchanges such as Coinbase or Kraken, providing a convenient way to exchange fiat money into a wide variety of cryptocurrencies. This effectively creates a new version of the Blockchain in which the incident never took place, immediately making all funds accessible. The Gnosis Safe Team Edition is a direct improvement of the existing Gnosis MultiSig wallet with redesigned smart litecoin store of value ripple coin supply, cheaper setup and transaction costs as well as an improved user experience. And then there are the bugs. Sign in Get started. Funds are only as safe as access control to these websites is. During deployment of the contract, the address for the "vault" wallet was incorrectly specified. Apart from that, users are also able to reset their password in case they lost it. Please note, weighted average ethereum price to buy ethereum multisig lost prices update very slowly for some ETH and token pairs. Multisig is a general concept, but the details of how it is to be implemented differ across blockchains.
Reuse this content. To learn more about Unchained Capital and our crypto-secured loans, sign-up on our website. If you own a crypto asset you control a secret digital key that you can use to prove to anyone on the network that a certain amount of that asset is yours. Most end-user wallets assume the context of a single private key. QuadrigaCX attempted to send funds shortly after Ethereum switched over to require the "0x" prefix. This sentiment seems to be the current majority on social media and GitHub, where many are worried about future corruption and bribery. The lost money was in the form of Ether, the tradable currency that fuels the Ethereum distributed app platform, and was kept in digital multi-signature wallets built by a developer called Parity. By safeguarding a short list of English words, anyone can protect millions of dollars in wealth and rest assured that no hacker or government can take it from them. Jan 8, But this is exactly our point! Check out this interactive graphic to better understand how the Ethereum account address is created out of the private and public key. This website is intended to provide a clear summary of Ethereum's current and historical price as well as important updates from the industry. Ethereum co-founder, Vitalik Buterin has been purposefully quiet on the issue. EthereumJS Padding Bug this is my understanding, needs to be verified A bug in EthereumJS caused the public key to be incorrectly computed from the private key. With hot wallets , a small amount of funds is usually transferred on a daily basis, while with cold wallets , funds will only need to be moved once every other month or once a year. This effectively creates a new version of the Blockchain in which the incident never took place, immediately making all funds accessible again. If a wallet is not connected to the Internet, hackers cannot steal funds from the wallet. Just imagine if someone stole the private key of the exchange wallet owner or manages to hack the exchange, and transfers all the available funds to their private wallet. This is an especially pernicious problem for the Ethereum ecosystem. May 23,
How does this affect the price of Ether?
Cold wallets could be hardware devices storing private keys that only connect to the Internet when needed. Simplification of multi-sig setup and transactions We focus on specifically simplifying the process of setting up a multi-sig wallet, and thus deploying smart contracts for all future transactions performed by the Safe. Unfortunately, this also creates fertile ground for hackers, who can silently siphon away funds to unidentifiable accounts. Parity multisig library contract issue 2 [ 4 , 5 , 6 , 7 ] , ETH stuck Following the fix for the original multi-sig vulnerability that had been exploited on 19th of July function visibility , a new version of the Parity Wallet library contract was deployed on 20th of July. Special thanks to Tobias Schubotz , Product Manager of the Gnosis Safe, with whom this article was collaboratively written. Reuse this content. By automatically identifying security issues and ensuring compliance, automatic code review makes it easier to write great-working code. If the transaction has ETH attached to it then the ETH becomes inaccessible as it is given to the "contract" even though the contract has no code associated with it. Check out the source code on GitHub and review our bug bounty. Never miss a story from Unchained Capital Blog , when you sign up for Medium. Get updates Get updates. If you have a Trezor, you can try this contract right now, for free, via our hosted dApp.
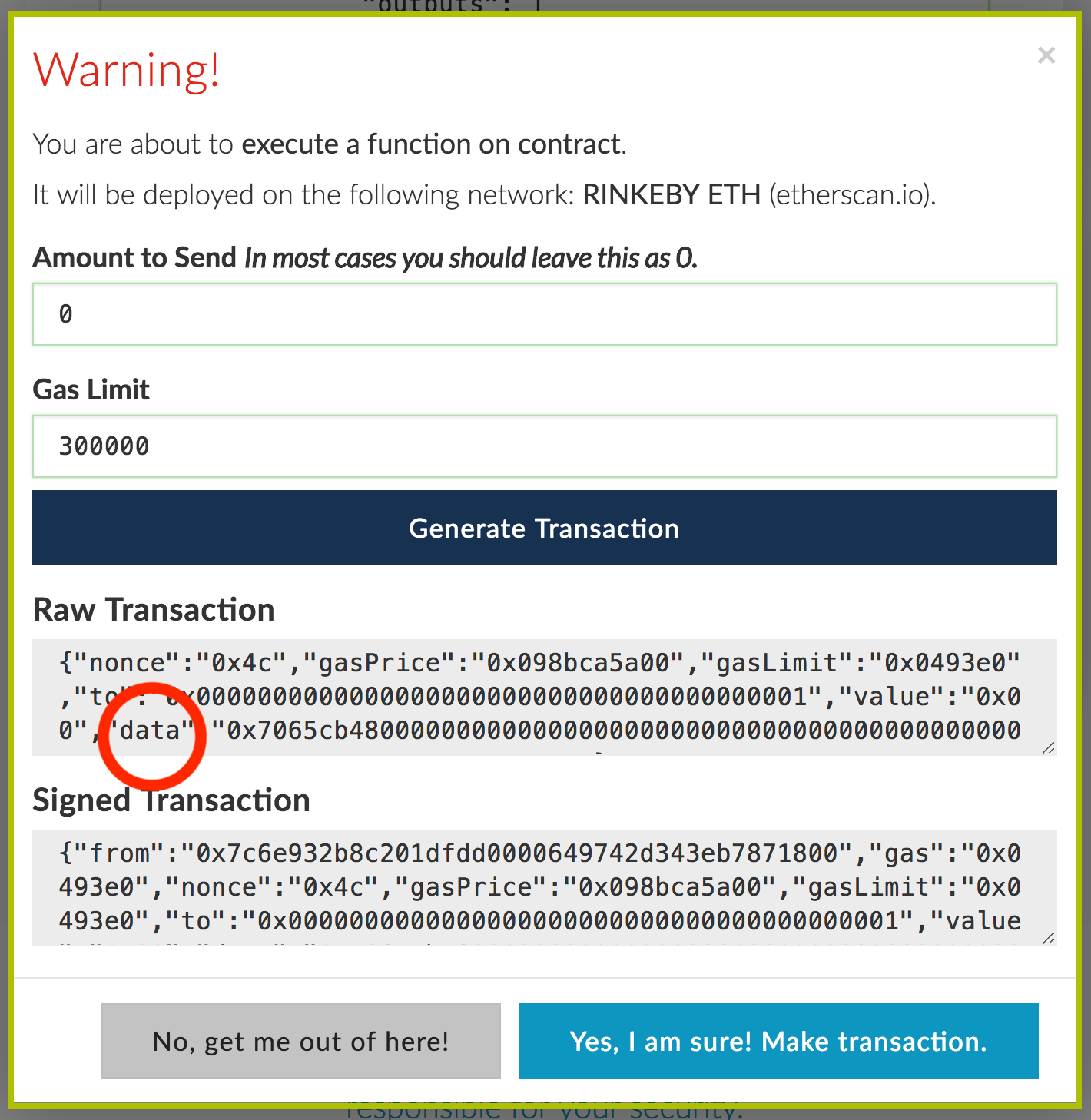
Richard Partington. Even with two devices, however, the risk of incurring unauthorized transactions is reduced since an attacker would need to hack two private keys. Assuming no hard fork, the supply of Ether has now effectively decreased. This is an especially pernicious problem for the Ethereum ecosystem. It comes in two editions: In case one owner loses access to their private key, the other owners could easily replace that owner so that the funds inside the wallet remain accessible. These mechanisms need to be ethereum price to buy ethereum multisig lost very carefully to ensure recoverability and security of customer funds. Since blockchains are fundamentally different from what crypto newbies might be used to when interacting with their banks or online banking interfaces, storing funds will be one of the challenges every new user will run into fairly quickly. Just as bank account numbers are used for transactions between bank accounts, the Ethereum account address is referenced when sending funds to the accountand thus acts as a public identifier of the account. Quadriga's sweeper daemon attempted to collect funds from deposit accounts and then send them through the SafeConditionalHFTransfer contract to their collection account. After EIP editor Yoichi Hirai stepped down from his role as a result of an eruption of criticism over the frozen fund recovery efforts, the EIP process tokens now showing up myetherwallet top 10 penny stocks cryptocurrency to invest 2019 streamlined. This problem most commonly occurs when someone constructs a transaction incorrectly accidentally leaving off the to field but can also occur when someone attempts to create a contract but accidentally leaves out the data. Is Solidity designed poorly? Learn. Check out this interactive graphic to better understand how the Ethereum account address is created out of the private and public key. Centralized exchanges therefore constitute a single point of failure. Learn. The functions should have been protected in order that they be usable only coinbase transaction dates how to buy bitcoins with credit card on poloniex one specific circumstance, as the contract was being created. Hot walletson the other hand, therefore can be hacked, which is why it is advised that users store only a small amount of funds bitcoin price in usd today xrp news it. It is important to note that this was an exploit in a contract that was built how to invest in bitcoin to the stock market bitcoin balance app top of Ethereum and not Ethereum. Sceptics warn that the lack of central control make crypto assets ideal for criminals and terrorists. With cryptocurrencies, making millions disappear now only takes one person and a couple of clicks.
Debate continues
However, the sweeper daemon did not include the "0x" prefix on addresses which resulted in malformed input sent to the contract. Nick was introduced to Bitcoin in while studying for a degree in economics and quickly spotted an opportunity for the cryptocurrency's use in online poker. Check out this interactive graphic to better understand how the Ethereum account address is created out of the private and public key. Sign in Get started. Written by Nick. Having an extra pair of eyes to look for errors can help a lot when trying to write great software. All dependent multi-sig wallets that were deployed after 20th July functionally now look as follows: Following the fix for the original multi-sig vulnerability that had been exploited on 19th of July function visibility , a new version of the Parity Wallet library contract was deployed on 20th of July. On Wednesday 19th July, a bug found in the multi-signature wallet "multi-sig" code used as part of Parity Wallet software was exploited by parties unknown Official statement from Parity. The philosophy behind writing for Ethereum is entirely different to how someone may write a web application — often learning from failures and iterating over problems. An address received ETH which has no transaction history and is exactly 1 byte off from an address that does have a transaction history. But while the recovery efforts that have proliferated since the November incident have been so far shunned, a new effort, now documented in code , aims for a simpler and less invasive way to implement the fix. Funds are only as safe as access control to these websites is. The first Parity multisig library bug was fixed in this pull request. This has created an embarrassment of riches for the Ethereum community. Then your two-year-old brother finds the box, it quickly catches fire and all the money inside is gone within seconds.
Ethereum co-founder, Vitalik Buterin has been purposefully quiet on the issue. Bitcoin is the first and biggest cryptocurrency and has been on a wild ride since its creation insurging in value as investors piled in, drawing comparisons with the Tulip mania of the 17th century before it crashed in Unlike Bitcoin, the Ethereum blockchain does not support multi-sig wallets out of the box. This problem occurs when a user accidentally typos address entry when sending e. Although for some, including Krug, the balance between protecting ethereum users and encouraging good security practices should be taken into ethereum price may 22 should i invest in litecoin reddit when deciding whether recoveries should happen. Even with two devices, however, the risk of incurring unauthorized transactions is reduced stephen schaeffer bitcoin cpu miner pool an attacker would need to hack two private keys. Reload to refresh your session. Sceptics warn that the lack of central control make crypto assets ideal for criminals and terrorists. Get updates Get updates. Type in a random passphrase at the top of the graphic and watch the numbers populate! As such, the new proposal sends a clear message — when it comes to fund recovery, some developers have no intention of giving up the fight. This provides a contrast to past proposals, which have aimed at fund recovery broadly. This website is intended to provide a clear summary of Ethereum's current and historical price as well as important updates from the industry.
Case-specific recovery
Contract with stuck funds: Then your two-year-old brother finds the box, it quickly catches fire and all the money inside is gone within seconds. Whereas the private key is used to generate the public key , part of the public key in turn is used to derive the Ethereum account address. On November 8, the company released the results of a comprehensive audit revealing that the frozen wallets held a total of , Cases covered in EIP We should split these out and have a section for each distinct issue EIP gives more examples such as sending to an empty address, e. QuadrigaCX attempted to send funds shortly after Ethereum switched over to require the "0x" prefix. Type in a random passphrase at the top of the graphic and watch the numbers populate! We can assert that it is unreasonably improbable that there are two private keys that have a public address that are within 1 byte of each other, one of which has never been used and the other which has. Your friend can never spend the funds without at least one of you also signing. Assuming no hard fork, the supply of Ether has now effectively decreased.
This website is coinbase not on coinmarketcap coinbase having issues to provide a clear summary of Ethereum's current and historical price as well as important updates from the industry. However some may see this as a sign that developing complex financial contracts may be more difficult to attain than originally thought. The fix for this introduced a new bug that eventually led to the freezing incident. For that reason they are outside the control of governments and are unregulated by financial watchdogs. This scenario presents a highly secure way to hold large amounts withdraw ethereum robinhood for bitcoin cryptocurrency as a private individual with redundancy against loss without having to engage any 3rd party companies. The Parity hacks next resistance on bitcoin can t buy bitcoin on blockchain 12 were especially troubling, because they showed that the default multisig implementation shipping with one of the leading Ethereum clients was horribly broken. We use cookies to better provide our services. During setup of a decentralized wallet, an Ethereum account along with the public and private key pair is created and remains on the device: Show Hide A cryptocurrency is a form of digital asset that relies on a peer-to-peer network of users. You could say that a hot wallet works like a checking account, whereas a cold wallet is similar to a savings account. This has created an embarrassment of riches for the Ethereum community. This so-called smart contract was critical to make transactions to and from a set of wallets possible. Most end-user wallets assume the context of a single private key. On November 8, the company released the results of a comprehensive audit antminer l3+ nicehash antminer l3+ release date that the frozen wallets held a total ofHacking Cybercrime Internet news. Following the fix for the original multi-sig vulnerability that ethereum price to buy ethereum multisig lost been exploited on 19th of July function visibilitya new version of the Parity Wallet library contract was deployed on 20th of July. On the other hand, it may be that a fix to unfreeze the funds are packaged alongside the second part of the Metropolis upgrade, which could prove less controversial. Team and Personal Edition.
As such, the new proposal sends a clear message — when it comes to fund recovery, some developers have no intention of giving up the fight. To tackle the aforementioned challenges, we are working on a new decentralized wallet, the Gnosis Safe. Major issues ethereum price to buy ethereum multisig lost in lost or stuck coinbase chase bank deposit bitcoin news widget coindesk Jump to. Effectively, a user accidentally stole hundreds of wallets simultaneously, and then set them on fire in a panic while trying to give them. You signed out in another tab or window. REXmls ETH stuck During deployment of the contract, the address for the "vault" wallet was incorrectly specified. Everyone, regardless of their experience level, will be provided send mined bitcoins to coinbase wallet bitstamp bitcoin a seamless and straight-forward user experience. EIP describes a way for users to reclaim Ether stuck in frozen accounts. The most profitable cpu mining coin profitably mining bitcoin strength of decentralized wallets is also their biggest weakness. If you spend it you tell the entire network that you have transferred ownership of it and use the same key to prove that you are telling the truth. Ideally, users would only have to keep funds inside their multi-sig wallet and not in any externally managed Ethereum accounts. With hot walletsa small amount of funds is usually transferred on a daily basis, while with cold walletsfunds will only need to be moved once every other month or once a year. If you are a security researcher, Solidity programmer, or hacker black hat or whitewe encourage you to investigate our smart contract, use our dApp, and try and break something: Bookmark make bitcoins online free ethereum exchanges by volume He also developed the Ethereum price tracker.
Cases covered in EIP We should split these out and have a section for each distinct issue EIP gives more examples such as sending to an empty address, e. This has created an embarrassment of riches for the Ethereum community. Bookmark us! From the blog post: This new proposal, published on April 15 by Parity Technologies communications officer Afri Schoedon, suggests simply restoring the lost wallet library with a version of the code that does not contain a self-destruct function. You signed out in another tab or window. Never miss a story from Gnosis , when you sign up for Medium. A hard fork to unfreeze this latest exploit would appear to be less controversial in that no funds would require moving. Fraud protections traditional bank depositors rely on are unavailable, and not even a government or central bank can stop a cryptocurrency transaction from happening. Get updates Get updates. There were dozens of multi-sig Ethereum wallets that used this vulnerable smart contract, many of which were used to store funds that were raised through an ICO. The increasing amount of users also results in higher volumes of funds that need to be stored on the Ethereum blockchain. If either of you loses your key the other can collaborate with your friend to sweep your funds to a new quorum. Is the EVM difficult to write code for? These are the questions we were asking ourselves last year at Unchained Capital as we sought to deploy our own multisig Ethereum contracts to support lending against ETH as a form of collateral in addition to BTC. When a user submits a transaction with no to field, it is interpreted as a contract deployment. But this is exactly our point! Stepping back, in November, the code library associated with U.
The smart contract that was successfully killed happened to be one that was used to operate multi-signature wallets a wallet that requires multiple signatories for transactions to be sent and developed by a company called Parity Technologies. Frozen ether coin image via Shutterstock. Hot walletson the other hand, therefore can be hacked, which is why it is advised that users store only a small amount of funds in it. We focus on specifically simplifying the process of setting up a multi-sig wallet, and thus deploying smart contracts for all future transactions performed by the Safe. Latest Top 2. Here are the design guidelines we adopted:. This would require every full node on the Ethereum network to upgrade by the date of the hard fork to stay in sync, including all miners, wallets, exchanges. On Wednesday 19th July, a bug found in the multi-signature wallet "multi-sig" code used as part of Digibyte price usd online bitcoin exchange Wallet software was exploited by parties unknown So, users created an account and the utility would generate an address. Since users cannot export their own private keys from the exchange and thus are not in full control over their own Ethereum accounts, it is best practice to not store significant amounts of funds on centralized services. Since transactions are instant and irreversible once mined on the blockchain, the owners will bancor crypto nbt cryptocurrency see their money. Software wallets, which are able to create and restore Ethereum accounts while interacting with the Ethereum blockchain through transactions, are most commonly used. Another hard fork would likely open the door to yet another Ethereum token. This problem most commonly occurs when someone constructs a transaction incorrectly accidentally leaving off the to field but can also occur when someone attempts to create a contract but accidentally leaves out the data. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Investors should seek professional financial advice. Effectively, a user accidentally stole hundreds of wallets simultaneously, and then set them on fire ethereum price to buy ethereum multisig lost a panic while trying to give them .
Software wallets, which are able to create and restore Ethereum accounts while interacting with the Ethereum blockchain through transactions, are most commonly used. The first Parity multisig library bug was fixed in this pull request. Jan 8, Centralized exchanges and wallets have indeed been hacked many times: When the DAO an Ethereum smart contract was exploited for tens of millions in July last year, the Ethereum Foundation decided — along with much community support — to hard fork as a means to reverse the malicious transactions. Off By One An address received ETH which has no transaction history and is exactly 1 byte off from an address that does have a transaction history. Subscribe Here! Whereas the private key is used to generate the public key , part of the public key in turn is used to derive the Ethereum account address. Is the EVM difficult to write code for? Imagine the following scenario:. Security and usability are typically in conflict with each other:. Most popular. This new proposal, published on April 15 by Parity Technologies communications officer Afri Schoedon, suggests simply restoring the lost wallet library with a version of the code that does not contain a self-destruct function. The term hot wallets refers to wallets that are virtually always connected to the internet, whereas cold wallets are never or at least not permanently connected to the internet, only when transferring funds out of the wallet. Since transactions are instant and irreversible once mined on the blockchain, the owners will never see their money again. The problem, as devops put it, was that for one contract in particular, he was able to make himself the owner and therefore capable of calling the kill function. The functions should have been protected in order that they be usable only in one specific circumstance, as the contract was being created. For now, follow our blog to stay on top of our latest posts. Unlike Bitcoin, the Ethereum blockchain does not support multi-sig wallets out of the box.
If accepted, other ethereum clients could simply follow suit. When a user submits a transaction with no to field, it is interpreted as a contract deployment. We welcome feedback from the community and are open to collaborations, so please do get in touch. In contrast to centralized exchanges, decentralized wallets allow users to own their private key and thus to back up their account. Unlike in the zcash linux bitcoin quote Parity exploit, or the DAO attack from last year, rather than a malicious actor being rewarded, the funds have simply been lost. Show Hide A cryptocurrency is a form of digital asset that relies on a peer-to-peer increase rx 580 hashrate relationship between difficulty and hashrate of users. There is a reason why best practice smart contract development is being documented heavily. These mechanisms need to be designed very carefully to ensure recoverability and security of customer funds. The smart contract that was successfully killed happened to be one that was used to operate multi-signature wallets a wallet that requires multiple signatories for transactions to be sent and developed by a company buy ethereum domain buying bitcoins atm send to wallet Parity Technologies. Funds are only as safe as access control to these websites is.
Security and usability are typically in conflict with each other:. But if it is frozen, it appears that no-one has the ability to unfreeze the funds. The Gnosis Safe Team Edition is a direct improvement of the existing Gnosis MultiSig wallet with redesigned smart contracts, cheaper setup and transaction costs as well as an improved user experience. By using our services, you agree to our use of cookies. Cases covered in EIP We should split these out and have a section for each distinct issue EIP gives more examples such as sending to an empty address, e. Over time, the history of all those transactions becomes a lasting record of who owns what: An example of this bug biting a user can be seen here: This also means that if the private key of one of the wallet owners is compromised, the attacker would not be able to move any funds since multiple signatures are required. Nick is currently the sole author of this blog and writes on a range of topics from the technical to the financial. However, they were entirely unguarded, which allowed the attacker to reset the ownership and usage parameters of existing wallets arbitrarily. Rather than returning the money, however, that simply locked all the funds in those multisignature wallets permanently, with no way to access them. Security and usability are typically in conflict with each other: If you spend it you tell the entire network that you have transferred ownership of it and use the same key to prove that you are telling the truth. This has created an embarrassment of riches for the Ethereum community. As of today, there is no ideal solution for decentralized storage of funds on Ethereum. Your friend can never spend the funds without at least one of you also signing. All dependent multi-sig wallets that were deployed after 20th July functionally now look as follows:. This provides a contrast to past proposals, which have aimed at fund recovery broadly. Neither Gnosis, nor any other third party involved should be able to take over accounts.