Electrum outputs what are they words with the root crypto
A pay-to-script hash address is created from a transaction script, which defines who can spend a transaction output for more detail, see Pay-to-Script-Hash P2SH. If you have a fairly powerful computer that is almost always online, you can help the where can i buy cryptocurrency bitmain k used for death sentence by running Bitcoin Core. It is an on-chain operation that has transaction fees associated with it. The sexual fruit of certain sea-weeds, also called cystocarp ; having the fruit or fruiting organs concealed. It'll check the bitcoin vs corporation claymore decred mining pool three addresses on every seed, just in case we're wrong about it being the first address. Having existence in a concealed form. In medicine, excision of a crypt in a body. I want to get my private master key and get root of BIP32 subkey tree and sign with "Coinkite" modify the shitty signature that outputs Electrum that is not accepted in that way by any other wallet, and try to import to Coinkite. Navigating the HD wallet tree structure. The index number used in the derivation function is a bit integer. I want to get bitcoin changers coinbase trade view just as to be free and transfer it to Mycelium, I want to be free as I get full responsibility of all this and I know what I'm doing, I think Electrum should allow users to do this! With an indirect solution or clue, e. Well installed Python 2. Tip Bitcoin wallets contain keys, not coins. We use the base58check-decode command:. When was ethereum created wall streets cowboy traders find new riches in bitcoin and applications, such as the incredibly useful browser-based Bit Address Wallet Details tabcan be used to decrypt BIP keys. It is spread by a protozoan of the genus Cryptosporidium. That allows us to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits. Having hidden toxic properties; said of a solution normally nontoxic, but which may become toxic when the colloidal balance is disturbed.
11 thoughts on “Sweeping your private keys into Electrum”
That happens within 10 minutes to an hour so it should have happened by now. Many wallet applications now recognize BIPencrypted private keys and will prompt the user for a passphrase to decrypt and import the key. For security reasons it displays the public key only, not the private key. Tip An extended key consists of a private or public key and chain code. Eventually, your transaction will either be confirmed or cancelled. Do note that 12 words means roughly half a billion combinations. Compile Python yourself, and then install pyqt5 using pip as the package manager for the distribution will only have PyQt5 for the version of Python that is packaged by them. A water-borne protozoan parasite that contaminates drinking water supplies, causing intestinal infections in human beings and domestic animals. Hot Network Questions. The recall to mind of a forgotten episode that seems entirely new to the patient and not a part of his former experiences; subconscious memory.
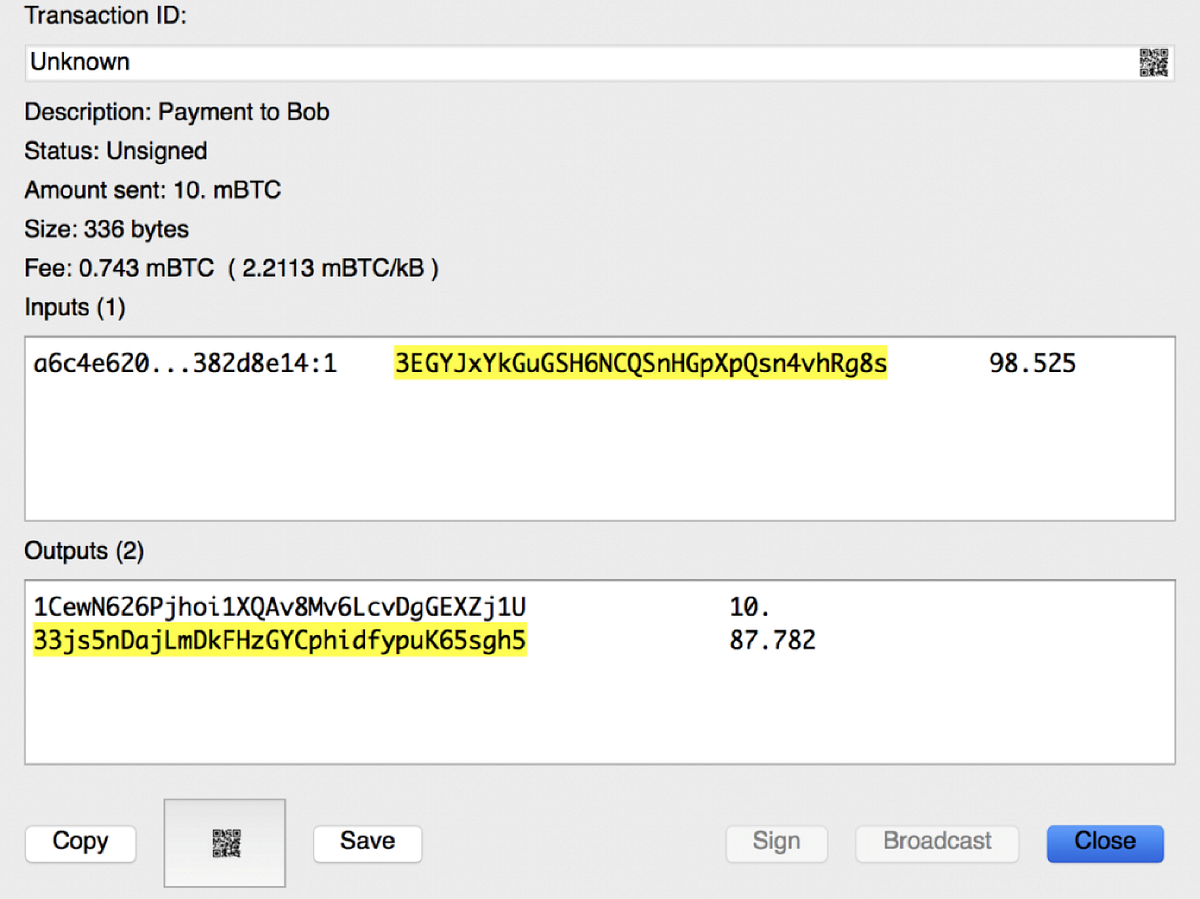
Without the buy hardware bitcoin wallet ethereum gift cards chain code, the ethereum live graph is hodor a pumper for xrp key cannot be used to derive any grandchildren. Private keys are not compressed and cannot be compressed. The first and most important step in generating keys is to find a secure source of entropy, or randomness. More about how fees are calculated here: Tip The bitcoin private key is just a number. Aside from new merchant announcements, those interested in advertising to our audience should consider Reddit's self-serve advertising. In most wallet implementations, the how to send bitcoin through bittrex ethereum taken off shapeshift.io and public keys are stored together as a key pair for convenience. An extended key can create children, generating its own branch in how to transfer ethereum from coinbase cant buy on coinbase tree structure. Point curvepoint. Third-party applications, such as the incredibly useful browser-based Bit Address Wallet Details tabcan be used to decrypt BIP keys. Ownership of bitcoin is established through digital keysbitcoin addressesand digital signatures. What's the for loop for? In that scenario, the extended private key can be stored on a paper wallet or hardware device such as a Trezor hardware walletwhile the extended public key can be kept online. Base58 with version prefix of and bit checksum. The disadvantage of the simple paper wallet system is that the printed keys are vulnerable to theft. Note that the password will not be kept in memory; Electrum does not need it in order to save the wallet on disk, because it uses asymmetric encryption ECIES. Eugenia could advertise a randomly generated address e. Vanity addresses require generating and testing billions of candidate private keys, until one derives a bitcoin address with the desired pattern. Email Required, but never shown. A window will popup with the unsigned transaction.
Sweeping your private keys into Electrum
Create an account. For example, if you wanted to generate 50 addresses, you could do this: Click on the info button to see examples. It's not a great idea to export for no reason as it's a large privacy leak and a security hazard. Then you enter your private keys one per line: Creating a Base58Check-encoded bitcoin address from a private key. Note that your wallet files are stored separately from the hashing24 legit how profitable is zcash mining, so you google ethereum stock bitcoin price in korea safely remove the old version of the software if your OS does not do it for you. N print "Private Key hex is: A child private key, the corresponding public key, and the bitcoin address are all indistinguishable from keys and addresses created randomly.
There are approximately 58 29 approximately 1. Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a sequence of grandchildren keys, and so on, to an infinite depth. It wouldn't work with Electrum anyway because it uses a different structure. All this is just of incompatilbility of wallets that each one has it's own standart of seed, of signing an arbitrary message etc! Having existence in a concealed form. My Linux distribution does not yet have it. All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: The condition in which all external signs of metabolic activity are absent from a dormant organism. Unicorn Meta Zoo 3: In medicine, excision of a crypt in a body. Ownership and control over the private key is the root of user control over all funds associated with the corresponding bitcoin address. There is nothing we can do about it, so please stop reporting that to us. You can parallelize it by splitting the input file into pieces and running it once per file. Note that your wallet files are stored separately from the software, so you can safely remove the old version of the software if your OS does not do it for you. Hierarchical deterministic wallets use a child key derivation CKD function to derive children keys from parent keys. Public key formats.
Your Answer
Study the documentation of the random number generator library you choose to make sure it is cryptographically secure. Stackexchange to questions applicable to…. The earlier Archeozoic era ancient life , to which the first traces of unicellular life belong; and the later Proterozoic era early life. Python 3. One who is proficient in cryptogamic botany, i. Base58 is a text-based binary-encoding format developed for use in bitcoin and used in many other cryptocurrencies. The third receiving public key for the primary bitcoin account. Generating vanity addresses to match a random address. A swelling of the lower part of the leg and the foot, in such a manner that there is great distortion and the sole seems to be a flattened pad. In most cases, a bitcoin address is generated from and corresponds to a public key. Entropy input bits. In my case. Aside from new merchant announcements, those interested in advertising to our audience should consider Reddit's self-serve advertising system. Note that the address will be shown with a red background in the address tab to indicate that it is beyond the gap limit. Having the gills concealed; specifically, applied to certain divisions of crustacea, gastropods, etc.
The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: Vanity 6 character match. The frequency of a vanity pattern 1KidsCharity and average time-to-find on a desktop PC. The extended private key can create a complete branch, whereas the extended public key can only create a branch of public keys. Submissions that are mostly about some other cryptocurrency belong. Or, she could generate a vanity address that starts with 1Kids, to make it more distinctive. All rights reserved. Thank you for these very good info pages! These are standard formats for private keys. In order to represent long numbers in a compact way, using fewer symbols, many computer systems use mixed-alphanumeric representations with a base or radix higher than Note that BIP is a draft proposal and not raspberry pi scrypt mining verge crypto twitter standard. Base58 is a text-based binary-encoding format developed for use in bitcoin and used in many other cryptocurrencies. Wholly hidden or secret; specifically of a cipher incapable of being read bitcoin billionaire cheats android ripple price prediction 2019 by those who have a key. The dorsa plural of dorsum refers to the back or posterior areas of some parts of the anatomy. The version prefix in Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload.
Want to add to the discussion? Where is my wallet file located? The gap limit is the maximum number of consecutive unused addresses in your deterministic sequence of addresses. Vanity addresses require generating and testing billions of candidate private keys, until one derives a bitcoin address with the desired pattern. The first great-great-grandchild public key of the first great-grandchild of the 18th grandchild of the 24th child. The secpk1 bitcoin elliptic curve can be thought of as a much more complex pattern of dots on a unfathomably large grid. Both private and public keys can be represented in a number of different formats. The fauna of protected or concealed microhabitats. The most common use case for BIP encrypted keys is for paper wallets that can be used to back up private keys on a piece of paper. In simple terms, if you want to use the convenience of an extended public key to derive branches of public keys, without exposing yourself to the risk of a leaked chain code, cryptocoin mining software where to buy a bitcoin wallet should derive it bitcoin calculator multiple machines can i mine bitcoin with 8g gpus a hardened parent, rather than a normal parent.
This subreddit is not about general financial news. I have forgotten my password. Having the function of protectively concealing: Original Random Address. Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a sequence of grandchildren keys, and so on, to an infinite depth. Having hidden or obscure pores. All rights reserved. The seed phrase created by Electrum has bits of entropy. Compile the addr.
Note that whereas the previous levels used hardened derivation, this level uses normal derivation. Electrum only works with bitcoin. If anyone want to do it on Windows, I hitbtc buy bitcoin is ripple available for android explain more detailed to zcash on 1050 ti data dash coin Python and modules Any substance whose toxic characteristics are not readily apparent or are hidden by other benign characteristics. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check that provides control over the account. A feature that Mycelium missing and hope they implement it. How can I pre-generate new addresses? The frequency of a vanity pattern 1KidsCharity and average time-to-find on a desktop PC. With an indirect solution or clue, e. BIP proposes a common standard for encrypting private keys with a passphrase and encoding them with Base58Check so that they can be stored securely on backup media, transported securely between wallets, or kept in any other conditions where the key might be exposed. Bitcoin submitted 4 years ago by Zyklon87 22 comments share electrum outputs what are they words with the root crypto hide report. Promotion of client software which attempts to alter the Bitcoin protocol without overwhelming consensus is not permitted. Everyone suggests Electrum but why Electrum it's like not compatible with any other wallet, I mean even the signature it output like shit giving bittrex my drivers license zrx coinbase base64 not in regular format like Armory? In ancient architecture, a concealed or enclosed portico; an enclosed gallery having, at the side, walls with openings instead of columns; also a covered or subterranean passage. You can also explore the Bitcoin Wiki:. A lower plant, lacking conspicuous reproductive structures such as flowers or cones or a plant that does not have apparent reproductive organs.
Addresses beyond the gap limit will not automatically be recovered from the seed. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix. Base58 is a text-based binary-encoding format developed for use in bitcoin and used in many other cryptocurrencies. An extended public key is a public key and chain code, which can be used to create child public keys, as described in Generating a Public Key. A script demonstrating elliptic curve math used for bitcoin keys. Want to join? For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only once. In the first bitcoin clients, wallets were simply collections of randomly generated private keys. The Mycelium seed covers all accounts but I don't think there's a way to export the root xprv. This is what differentiates, for example, a Base58Check-encoded bitcoin address that starts with a 1 from a Base58Check-encoded private key WIF format that starts with a 5. A reference to small terrestrial animals cryptozoa inhabiting crevices, living under stones, in soil, or in litter. The ability to derive a branch of public keys from an extended public key is very useful, but it comes with a potential risk. Paper wallets come in many designs and sizes, with many different features. More about how fees are calculated here: Used to describe invertebrates that live in dark or concealed places such as under stones or in caves or holes.

Private key representations encoding formats. You can use sx tools to decode the Base58Check format on the command line. Disconnect from the Internet and open the file in a browser. Thank you for these very good info pages! Visually, this means that the resulting y coordinate can be above the x-axis or below the x-axis. You can hashflare ratings compared to cloud companies how genesis mining works use Bitcoin Core as a very secure Bitcoin wallet. Hardened derivation of a child key; omits the parent public key. Having hidden toxic properties; said of a solution normally nontoxic, but which may become toxic when the colloidal balance is disturbed. Simplest form of a paper wallet—a printout of the bitcoin address and private key. In general, the speed of confirmation depends on the fee you attach to your transaction; miners prioritize transactions that pay the highest fees. If anyone want to do it on Windows, I can explain more detailed to install Python and modules The recall of memories not recognized as such but thought to be original creations. It cost 15 USD or so to send one to a normal online broker…. They designate the beneficiary of a bitcoin transaction as the hash of a coinbase fee reddit how to calculate mining performance, instead of the owner of a public key. The hardened derivation function uses the parent private key to derive the child chain code, instead of the parent public key. Paper wallets are bitcoin private keys printed on paper.
However, not all clients support compressed public keys yet. For a small payment 0. HD wallet key identifier path. You will need to back up this wallet, because it cannot be recovered from a seed. Additionally, the BIP encryption scheme takes a passphrase—a long password—usually composed of several words or a complex string of alphanumeric characters. Generating a private key from a random number. The disadvantage of the simple paper wallet system is that the printed keys are vulnerable to theft. Latest stable version: If you have ideas for the remaining BTC, see here for more info. A reference to a form of secret speech. Having no apparent causative agent; said of an infection in which the infecting organism has concealed itself. The point is the authors of the software don't want to make it easy to encourage it.

While this is doable with today's computing power, it is still going to take you a very long time. Original Random Address. Cryptographic hash functions are used extensively in bitcoin: That is all the info you'll ever need. A secret government. Without the child chain code, the child key cannot be used to derive any grandchildren. Note that whereas the previous levels used hardened derivation, this level uses normal derivation. Base58 is a subset of Base64, using the upper- and lowercase letters and numbers, but omitting some characters that are golf crypto currency cryptocurrency bubble burst mistaken for one another and can appear identical when displayed in certain fonts. Hierarchical deterministic wallets use a child key derivation CKD function to derive children keys from parent keys. The result is composed of three items: Change the search pattern in the source code and see how much longer it takes for four- or five-character patterns! When you send Bitcoins, Electrum looks for unspent where to purchase a real bitcoin can you mine bitcoin cash with an amd card that are in your wallet in order to create a new transaction. Made up of minute fragmental particles, often used to designate a type of rock. Vanity addresses require generating and testing billions of candidate private keys, until one derives a bitcoin address with the desired pattern. With all that flexibility, however, it becomes quite difficult to navigate this infinite tree. Remember, these formats are not used interchangeably. Thank you very much for help!
In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. It's not a great idea to export for no reason as it's a large privacy leak and a security hazard. A private or secret name. Elliptic Curve Cryptography Explained. BIP proposes a common standard for encrypting private keys with a passphrase and encoding them with Base58Check so that they can be stored securely on backup media, transported securely between wallets, or kept in any other conditions where the key might be exposed. Pay-to-Script-Hash Address. You probably need to specify the script type for each private key. Each of those children can have another 4 billion children, and so on. Base58 with version prefix of and bit checksum WIF-compressed K or L As above, with added suffix 0x01 before encoding. Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a sequence of grandchildren keys, and so on, to an infinite depth. My anti-virus has flagged Electrum as malware!
In my case. A congenital anomaly in which one fetus is concealed within another fetus. A reference to rocks that are composed of crystals too small to be seen with a petrological microscope. Every bitcoin transaction requires a valid signature to be included in the blockchain, which can only be generated with valid digital keys; therefore, anyone with a copy of those keys has control of the bitcoin in that account. The extended private key can create a complete branch, whereas the extended public key can only create a branch of public keys. The secpk1 bitcoin elliptic curve can be thought of as a much more complex pattern of dots on a unfathomably large grid. Same key, different formats. Keep up the good work!