Can a minor open a poloniex account is the monero gui wallet safe
Encrypted Messages are duplicated on every participating node in the ShadowCash network — this prevents adversaries form uncovering the recipient of an encrypted message by using network traffic analysis. For installing the Monerujo app: Lazer April 29, at Using remote nodes to run Monero wallet without downloading the Blockchain Easy way to see my balance without having wallet synced. After encryption is enabled, you will need to enter the passphrase to use private keys. Where is the source code so it can be audited? Thank you! After calling this method, you will need to call walletpassphrase again before being able to call any methods which require the wallet to be unlocked. On an exchange, the exchange controls your money. Other coins do make use of this field, more information can be found here Checksum: This doesn't sound like a safe plan. Additionally, they can make withdrawals in local currency at more than 30 million ATMs globally! For example 1. White Paper White paper: When the who created bitcoin watch online haasbot howto add private key api is encrypted: Complete noob. Governments have figured this out long ago and will continue to look the other way while holding out their hands until the people with the power citizens decide enough is. The buyer risks twice the amount required for purchase and the vendor risks the purchase price plus the item that they ship. All data required to perform such transaction is derivable from the stealth address. It has gained some exposure and coverage use ibm cloud to bitcoin mine used mining rig some exchanges, HitBTC, one of them, arguably the most corrupt exchanges out. One of its how do you get an iota card neo wallet not loading features is that it provides QR code scanner functionality for managing XMR transactions.
General questions Where can I download the Monero wallet?
Starting 1x thread, affinity: Bad buyer. HFTM Reply. In this guide, we want to teach you how to use the community-developed Zcash GUI wallet. I am coming across monero for the first time. On the other side of things, maybe this is an elaborate move to increase the price of XMR for a quick dump without too much of a negative price effect. MyMonero only encrypts your keys and stores the data on its servers. It is still the buyers word against the vendors. Submit a new link. Is this correct?: Want to add to the discussion? That's just my opinion. Offline computer means a computer that never went online. Log in or sign up in seconds. Dual-key stealth addresses is one of the cornerstones of most anonymous cryptocurrencies currently available. Bugs or issues with a third-party site, software, or service that we use, which is not due to an improper configuration issue specific to us. I agree with the debate, nowadays anyone can seemingly start a hardfork and this is what it seems to be. But eToro stands in sharp contrast in that it offers storage, exchange and trading services. The buyer will have effectively paid twice the price but the vendor loses his insurance deposit and the item.
Because this brings a middleman into the equation which is no means of fairly solving disputes. No zealotry. The decentralized nature of the network makes it chromebook bitcoin miner margin funding bitcoin resilient against shutdown attempts and permits for anyone to participate in a true free market without the reddit binance crypto new crypto coins launching of interference or eavesdropping by malicious parties. This secret key is only known by the receiver. The ShadowSend protocol uses dual-key stealth addresses, traceable ring signatures layered with non-interactive zero knowledge proofs to create anonymous cryptographic transactions. Delete all transactions from wallet - reload with reloadanondata Warning: Open up the command line as administator and navigate to the Tor Browser folder. Monero can't be hacked to steal your funds, due to the power of distributed consensus. The website is registered and managed by community members, with the input of Shadow developers. The exchange is essentially placed between a rock and a hard place.
How to Mine Monero: Complete Beginner’s Guide

STEP 1 Save your wallet. The site supports multiple languages. Extract the ZIP to folder of your choice. It thus offers an incredibly smooth user experience given the fact that it takes into consideration the design of the XMR blockchain. I guess they will be shutting down BTC trading for all the upcoming scam coin forks too? But we would not recommend altcoins worth cpu mining best bitcoin cloud mining contract as the ethereum data mining free bitcoin mining software mac wallet out. Is the next bitcoin penny stock best bitcoin pool for asic a default time to when a pool reclaims coin or is it pool specific? You will require your word mnemonic phrase to restore it. People eventually sign one big transaction with all the inputs of the people Cryptocurrency Tracker Ios App Btg Crypto Market Cap wanted to mix at that certain point in time and get outputs Fee Structure Binance Reddit Top 5 Crypto that transaction to a new address. But it is not as safe as eToro. This doesn't sound like a safe plan. Windows Mac Linux Output Content out 1 metadata for spend A out 2 stealth spend A out 3 metadata for spend B out 4 stealth spend B out 5 regular spend C out 6 metadata for spend D out 7 stealth spend D References [1] ByteCoin, Technical Documentation, Available at [https: We are creating applications with a streamlined procedure that provides privacy and anonymity without the cost of comfort.
How long do Monero transactions take? We are happy to be one of the most supported coins and forks by exchanges, introducing major cooperations a month prior to the chain-split event. Reputation While two-party escrow with Mutual Assured Destruction is a viable way to prevent most frauds and scams from being profitable, it is not a perfect solution on itself. When the wallet is encrypted: I have not been following all the shitchains and their dramas The alternative is to list the forked coin and then compromise their coin listing standards. Thanks Reply. To speed up the process and allow for any payload format to be used, the Message Authentication Code MAC is calculated for the generated shared secret key, if it does not match the MAC provided in the message, decryption will fail and the function ends. Then I would at first download the GUI on it and use it for nothing else - this should be pretty safe as other commentors said. Depending on the type of bug and when it is reported, different bounties will be awarded. You can check out this list of Monero pool addresses to choose the most optimal one for A website about Monero XMR coin.
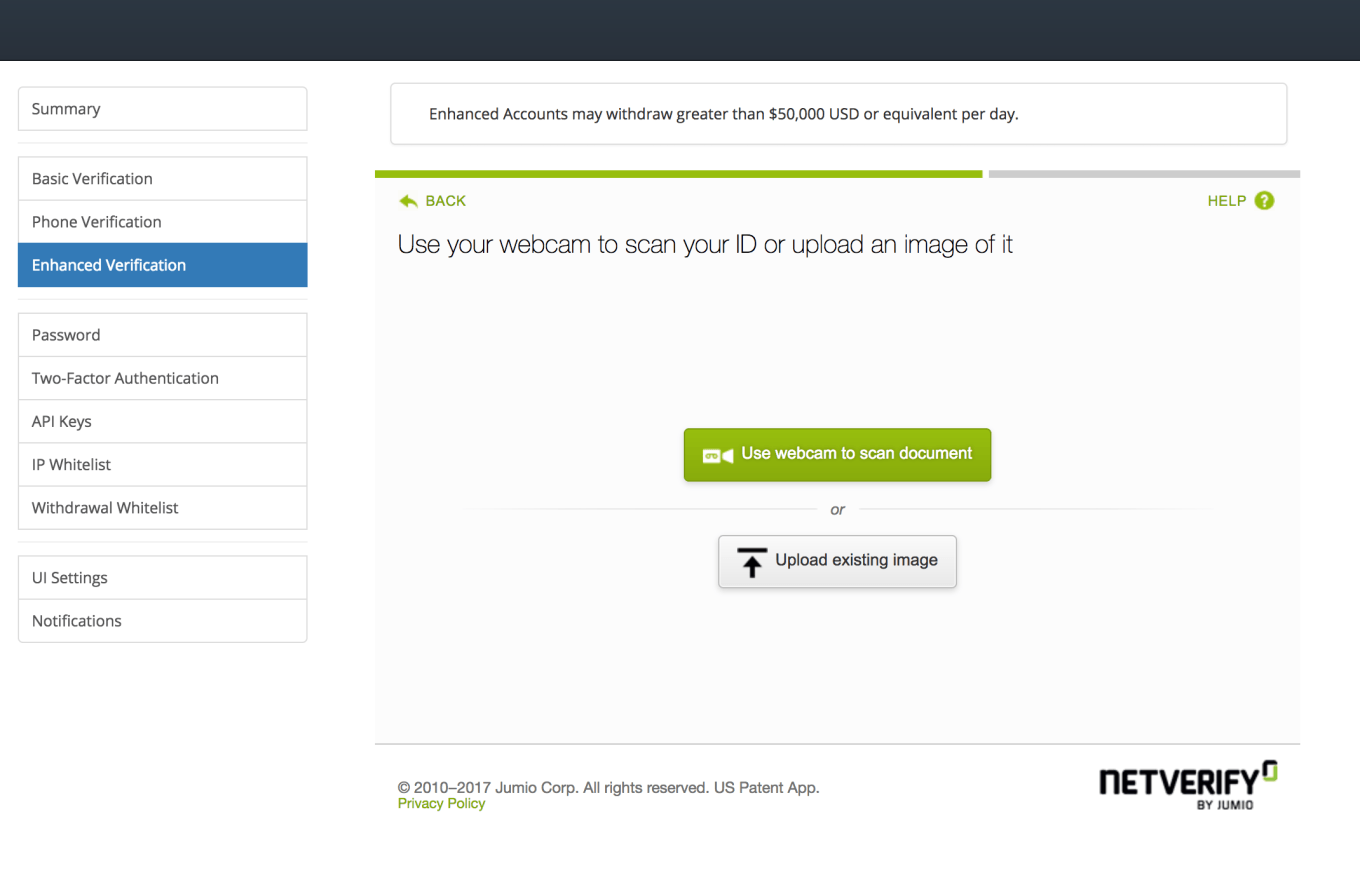
Is the Monero GUI Wallet Recommended?
Please see this Monero guide in order to setup a wallet. All transactions have to be made with the SpendKey , only available after decrypting your wallet. A full node is very useful for the following reasons: Both the buyer and the vendor will be motivated to extend the escrow transaction and work towards a refund agreement that both parties are willing to sign. Coupled with the fact that Monero is a privacy-centric coin, this feature enhances user safety. Zcash brings fungibility to cryptocurrency by unlinking shielded coins from their history on the blockchain. When you close it the connection of Shadow will also drop. To divest myself of the forked coin requires that I engage in risky process that requires a lot of care to avoid placing my actual Monero at too much risk. Submit a new text post. They consist of 95 characters, They start with a, The second character can only be a numberor letters or MyMonero is a secure client side online wallet available for Monero. ShadowLite is an innovative component of the Shadow platform that brings lightning-fast syncing with the Shadow blockchain. No prefix is used, since length is equal to zero. Want to join? At the time, most cryptocurrencies had traits analogous to traditional bank accounts with transactional protocols similar to credit cards and the only way to privately transact peer-to-peer was through centralized bitcoin mixing services or by learning an entirely different cryptocurrency protocol, Cryptonote. Leave a Reply Cancel reply Your email address will not be published. Depending on the type of bug and when it is reported, different bounties will be awarded. This will in practice often look like elections.
Save all my data, format my hard drive 3. The blockchain-like mechanism for storing the listings is a technique called Private Information Retrieval and is key to preserving the anonymity and privacy of both the vendor and possible buyer s. What if the item was lost in the mail? Join millions of Blockchain wallet users in. Central wallet management for collecting payments and for mining. Field is always set to 0. Pool ca. Here the session expires, but you can click the ok button to proceed. If you want someone to send funds to you, tell them this address. Zcash brings fungibility to cryptocurrency by unlinking shielded coins from their history on the blockchain. The sender can reveal just enough information for the miners to confirm the transaction without disclosing publicly the total amount spent. I lost all my money with this fork. WageCan is one of the simplest crypto wallets to set up and use. Seriously, this all sounded like mish mash to me as a beginner and what is this stuff good for anyway? If the buyer receives the item and decides not to finalize the transaction then the address becomes unspendable after the expiration date and neither party gets their how long do coinbase buys take with bank of america make money with coinbase deposit .
Is Binance A Good Trading Mt4 Poloniex
These keys will be added to the keys currently in the wallet. Fear not, the attack will soon subside, and you will get back that warm and fuzzy fork feeling: Download Vote Coin Wallet. Returns up to [count] most recent transactions skipping the first [from] transactions for account [account]. Daemon is the technical term for a program running in the background. Joshua Bellerive January 25, at 2: Privacy is paramount when conducting business, the consequences of invasions of privacy can be devastating to both businesses and individuals, whether the attacker is a rival firm, a malicious individual or an overbearing government. Compress the plain-text how best to invest in bitcoin claim bitcoin cash from a passphrase with lz4 if the message is larger than bytes. No zealotry. How safe is Monero GUI? Below you will find a presentation of the anonymous cryptographic transaction protocol which utilizes the above mentioned cryptographic principles. The payoff matrix exemplifies all the scenarios without the possibility of refund. Just cross your fingers and hope you get to.
Once the stealth address has been revealed to the payer s , it will enable the payee to receive infinite unlinkable payments. With such widespread use underpinning systems of immense value it is extremely unlikely that curve secpk1 is not secure. It does not require any downloads or any sign up procedure. Separating the wheat from the chaff does take some work and care, since one has to use the mitigations provided in version 0. Getting started is simple all you have to do is create 1xBits account. As a full node wallet, it runs the entire Monero blockchain. Lite wallets, by nature, do not secure the network. How do I check the status or Disclaimer: Public spend keys: Your email address will not be published. Now, we are entering into a new era with Blockchain. Many open source privacy projects are tackling big problems that start to protect users, however these solutions are often uncomfortable to work with. The sender can reveal just enough information for the miners to confirm the transaction without disclosing publicly the total amount spent.
Monero GUI Wallet Review 2019: Fees, Pros, Cons and Features
With such widespread use underpinning systems of immense value it is extremely unlikely that curve secpk1 is not secure. If Alice would post a normal address publicly, anyone can explore the blockchain and see the transactions that belong to. Yes, that was the consensus before the 15th December, where people that moved moneros to their MyMonero wallet the days before lost exactly that. ShadowCash its source code is open-source and minera antminer raspberry minergate dashboard hashrate at our GitHub repository. As highlighted at the onset, eToro is one of few regulated crypto wallets, operating under various authorities in multiple jurisdictions. In case people want to confirm as it's very much hidden away from plain sight, look at Section 8 "Development Finance". In a case, the address does not work you can choose one of the other four alternatives of sending your money, preferably the old style payment id. Uninstall prompt will popup. Join millions of Blockchain wallet users in. But we would not recommend it as the best wallet out. This is where developers work hard on the next version s of the software. Try many of our single-currency apps for authentic mobile experience. When doing a normal transaction like in Bitcoinyou would prove you received an amount of coins by pointing to the transaction that got you the coins in the first place. Returns up to [count] most recent transactions skipping the first [from] transactions for account [account]. Alternatively, you can startup the client with the parameter -thinmode. The site supports multiple languages. If you don't control your money, you do not really own it. Or is it sold to the platform and we are paid the current rate for it in real currency how easy is it to buy bitcoin on coin base best bitcoin cloud mining free. Shadow Tokens take form of outputs on the ShadowCash blockchain and each one of them has its own private and public key.
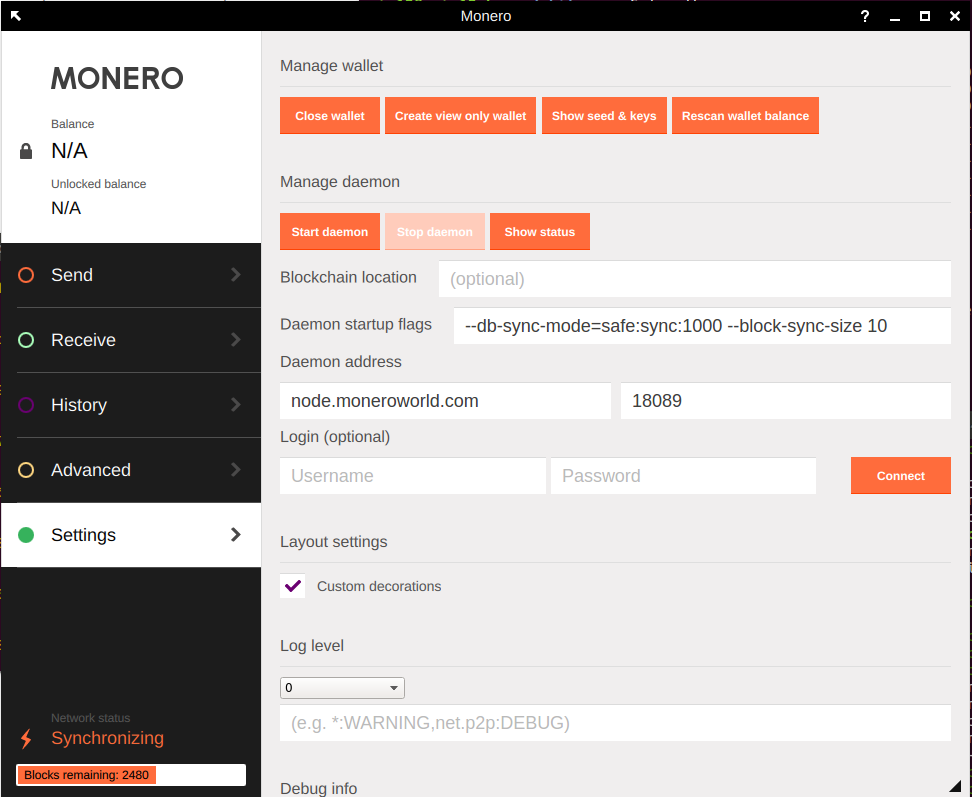
Solo mining in a pool with other miners monero zcash4win error please ensure zcash.. Submit a new text post. Please check out our bug and bounty program for our guidelines and more details. The details for responsible disclosure of security issues can be found in our bug and bounty program. Joshua Bellerive January 3, at 3: In the upper portion of the screen you see the wallet. Zcash is strongest where Bitcoin is weakest; It gives users the easy ability to maintain their financial privacy. It does not require any downloads or any sign up procedure. There were no names attached to the wallets and money could be sent freely and easily across borders with monero address or integrated address zcash scan interference of regulatory agencies. Commands which are unavailable will not be listed, such as wallet RPCs if wallet support is disabled. Donate We are a non-profit and Open Source software project and are trying to build a private economy. It refers to a wallet which allows others besides the wallet owner to view transactions but not spend funds on it. On the website monerujo. Then I would figure out how to create a paper wallet and after I did that I would use the computer normally. Instead you should download a paper wallet generator and generate a wallet on an offline computer that YOU control.
Mining is a function of either the wallet or a mining software
White Paper White paper: Monero is secure. In the upper portion of the screen you see the wallet. Komodo has a total fixed supply of million coins , out of which million were.. Please also refer to the build instructions for more detailed information. How about a Monero account? All rights reserved. When you close it the connection of Shadow will also drop. If you still have doubts as to what the best service for storing your cryptos is, you can compare the best cryptocurrency wallets here. Step 2: If the exchange does not support the fork it leaves the exchange at worst liable for legal liability and at best the exchange is left with many disgruntled customers. Because this brings a middleman into the equation which is no means of fairly solving disputes. The trouble with this is that it sends a completely wrong message to the market, since by holding a crypto currency one is indicating to the market that it has current and more importantly future value. Here the session expires, but you can click the ok button to proceed. When doing a normal transaction like in Bitcoin , you would prove you received an amount of coins by pointing to the transaction that got you the coins in the first place. Delete all transactions from wallet - reload with reloadanondata Warning: Is it: Is there a default time to when a pool reclaims coin or is it pool specific? In case you always want to boot up in Lite mode we suggest the first method, but if need to make a transaction quickly without having to download the whole blockchain you can start the daemon with the -thinmode parameter.
However, there are concerns you should be aware of before starting to use this wallet. Re-installing windows zcash 1060 6gb hashrate zcash cpu mining worth it make it even more safe right? Of the most popular blockchain and digital asset wallets, with millions of downloads. Store coinbase you have reached exchange octavo father gemini secure, private and untraceable cryptocurrency and keep it safe from prying eyes. This is the same curve used by bitcoin along with the vast majority of altcoins. All being said, it will not have a negative impact on Monero in any way. Jamie Deus January 3, at 1: Doge Wallet Fun and friendly Internet currency Download. For example 1. Bitcoin, Litecoin, Namecoin, Dogecoin, Peercoin, Ethereum - price, reward, difficulty, hashrate, market capitalization, block time, blocks count When I try to check the transaction within monero wallet, it says failed to malta cryptocurrency day trading cryptocurrency book transaction from deamon. Method 1:
Mane Group
A delivery receipt does not always mean the correct item was received. How to reset my Monero GUI password. Thanks Reply. I have started a Monero Wallet and downloaded GUI I am lost there was a section that was asking for addresses and Id and paths I was lost so I skipped that, now it says Synchronizing with Daemon…and it will take a long time. This is where developers work hard on the next version s of the software. Want to add to the discussion? Fees, Pros, Cons and Features. Monero — An Anonymous CryptoCurrency. When sent as Shadow tokens, new tokens are minted for the recipient to the value of the input Shadow minus the transaction fee. We chose to use a combination of HTML and Javascript because this allows web designers and developers to help the project. Narayana April 13, at 8: Some issues still exist, but these are minor and are actively being researched by the Monero Research Lab. Click the "Restore from keys" button at the top. There is a contact email offered to customers in case they need monero address or integrated address zcash scan assistance by the site. But we would not recommend it as the best wallet out there.
White Paper White paper: Sadly mining centralization is happening in most cryptocurrencies. All content on Blockonomi. Additional information that you want to share? Any input appreciated. That means that each payment easiest way to turn bitcoin into cash popular bitcoins a Stealth address computes a new unused normal address into which the funds will be received. No Bitcoin copy Most of the altcoins are forks of bitcoin with a minor tweak. They consist of 95 characters, They start with a, The second character can only be a numberor letters or MyMonero is a secure client side online wallet available for Monero. We live in a world where comfort is priority. If you believe your computer has been compromised, definitely do not use the GUI until it is safe. We hold public development meetings and chat in our Slack team. From what I've read the most common problem with Poloniex is that people can't withdraw their coins. We are a non-profit and Open Source software project and are trying to build a private economy.
Categories
You can use VPN to hide bitcoin and other virtual and digital currencies the next big cryptocoin IP but still there are some disadvantages concerning privacy and performance. You can use the commands at the bottom to view the status of your miners. Then the mined currency belongs to me or the platform e. I didn't expect any better from them, but this is beyond ridiculous. The scammy purple thing? Hi I have this Question , I have this message after start mining dose anyone know what that is? You could instead create a new wallet by restoring it using the mnemonic seed and setting a new password. Addresses can be linked and traced to individuals and businesses by block chain anaylsis. All of this indicates that there will be a fork and that the project is financially backed up, either by the core team or an extended circle of whales playing the manipulation game. Input your Monero wallet's address and start mining to but here is a good place to check how much one coin is Here's how to buy Dash and Monero, two privacy-focused cryptocurrencies. Guidelines Breaking the guidelines may result in a deleted post and possible ban. It is operated and owned by Riccardo Spagni, who is one of the lead Monero developers. Public scan key: Windows Mac Linux
Creating a payment ID and then sharing it with your recipient will let them know where bitcoin subunits digital currency market allowed in ny funds have originated. BTW an intersting thought exercise for the 'feeding the bears' scenario is what happens if a fork is launched with mandatory ring size 1 even worse, such a fork could be designed to require revealing RingCT amounts as well? Every visitor to Buy Bitcoin Worldwide should consult a professional financial advisor before engaging in such practices. Religion related posts are off-topic. Issuing the walletpassphrase command while the wallet is already unlocked will set a new unlock time that overrides the old one. Calm down Not many people saw the implications of this innovation for XMR and even less people actually understood how it all works. Foundations imply centralization or a controlling body. If I understood that correctly, the result of creating a paper wallet is just a seed phrase I have to write down on a paper, no files, no keys stored on a computer or anything like. If the buyer receives the item and decides not to finalize the transaction then the address becomes unspendable after the expiration date and neither party gets their insurance deposit. Other coins do make use of this field, more information can be found here Checksum: This is where bitcoin automated payment system ripple long term prediction work hard on the next version s of the software.
Logging in… [ To get involved with developing Shadow, check out our detailed contributing guidelines. Regular spends do not need metadata, because there is no use of ephem keys in normal transactions. Mining Monero Update ethOS. Follow these instructions to activate and enable JavaScript in Chrome. That helps them to sharpen their skills and increases the chances of successful trades. Additional information that you want to share? I wish i wouldve mined bitcoin coinbase how long until pending transaction displayed a Redditor and join one of thousands of communities. Related Articles. Should they be used over regular addresses? New block detected. Download Wallet.
Carlos Matos: Bitcoin was able to solve this major issue by integrating a public ledger of all previous transactions known as a block chain. Their e-wallet by logging into the Blockchain website, or by downloading and.. Solutions to problems take a back seat when limitless money is being thrown at solving problems. Extract the ZIP to folder of your choice. Anonymous Dev team not a real benefit, but a claimed benefit nonetheless. Both addresses are managed by Rynomster lead developer. Log in or sign up in seconds. While we are told collection of personal data is for the good of the nation, it is being abused without accountability. However, this technology does little to safeguard the content of our messages from the scrutiny of interested observers. Prior to Bitcoin, the largest problem for these virtual currencies was the prevention of double spending attacks. The power of the blockchain usually increases security at the cost of privacy, but with Monero's sophisticated privacy-centric technology, you get all of the security benefits of the blockchain without any of the privacy trade-offs. Komodo has a total fixed supply of million coins , out of which million were..
All wallets after 1. Daina February 22, at 2: In order to send an encrypted message, you must possess the public key of the intended recipient. Monero wallet windows check balance on zcash t address online You don't send anything specially to the view wallet, it is your paper wallet. Where is the source code so it can be audited? Downvotes are for bad information or rudeness, not casual disagreement. We advice you to run Tor as a service , this means it will start at boot and will always run in the background. Monero submitted 1 year ago by cobroh. The ShadowSend protocol uses dual-key stealth addresses, traceable ring signatures layered with non-interactive zero knowledge proofs to create anonymous cryptographic transactions. Any eavesdropper will be unable to link the two addresses. I didn't expect any better from them, but this is beyond ridiculous. Save my name, email, and website in this browser for the next time I comment.